defend-id | blog
Insights & developments in Identity Protection
How to Avoid 4th of July Scams: Essential Tips for a Safe and Secure Holiday
The 4th of July is an amazing day filled with fireworks, barbecues, and celebrations of our nation's independence. Unfortunately, scammers see see it as an opportunity to exploit unsuspecting patriots. Whether it's through phishing emails, fake sales, or counterfeit...
How Identity Theft Can Ruin Your Credit: Essential Steps to Protect Yourself
Identity theft is a serious crime that can devastate your finances and your life. When someone steals your personal information, they can use it to open new accounts in your name, run up debts, and damage your credit score. Here we will discuss How to Protect Your...
Unmasking Identity Theft: Debunking 9 Common Myths
Safeguarding our personal information is crucial! Yet, many of us operate under certain misconceptions, trusting myths that could leave us vulnerable. Welcome to "Unmasking Identity Theft: Debunking 9 Common Myths." This blog post aims to shed light on the most common...
The Importance of Identity Theft Protection in Employee Wellness Programs
Identity Theft Protection as an Employee Benefit Identity theft is a growing concern that can have devastating effects on individuals and businesses alike. As an employer, integrating identity theft protection as an employee benefit into your wellness program is not...
Protecting Your Identity While Traveling: Tips for a Secure Vacation
Traveling can be exciting, but it also comes with risks, such as identity theft. Vacationers are often more relaxed and less vigilant about their personal information, making them easy targets for thieves. However, with a few simple precautions, you can enjoy your...
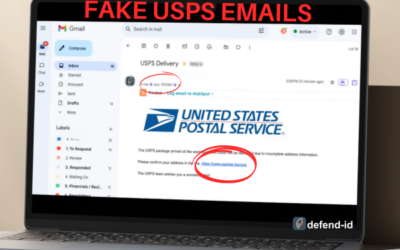
Fake USPS Emails: Protect Your Personal Information
Beware of Fake USPS Emails: Protect Your Personal Information Understanding the Scam Scammers are constantly evolving their tactics to deceive unsuspecting individuals, and one of the prevalent scams involves fake USPS emails. These emails often contain fraudulent...