
by Brian Thompson | Jul 23, 2024 | Employee Benefits, Identity Theft
Understanding the Problem with Identity Theft Protection Services
The Prevalence of Bundled Services
Identity theft protection services are often offered as part of a package with other products. This bundling creates a widespread misconception that all identity theft protection services are similar. Consumers and partners frequently think, “It’s offered everywhere already, so why choose a standalone service?” It is important to understand where those fall short and what makes a superior identity theft protection program.
Misconceptions about Standalone Services
The reality is that bundled services typically offer limited protection. They may include basic monitoring or reimbursement for financial losses but leave significant gaps in coverage. These gaps expose individuals to various risks that are not addressed by partial services.
Common Misconceptions about Bundled Identity Theft Protection
Limited Protection of Bundled Services
Bundled identity theft protection services often provide minimal coverage. This might include basic alerts or financial reimbursements, which do not fully address the complexities of identity theft.
Risks of Partial Coverage
Partial coverage means that many aspects of identity theft are left unprotected. Individuals might face risks related to medical identity theft, tax fraud, and other areas that require comprehensive monitoring and protection.
Our Comprehensive Solution for Identity Theft Protection
End-to-End Recovery Service
Expert Recovery Advocates
Our end-to-end recovery service is a cornerstone of our protection plan. Imagine having an expert recovery advocate who handles all necessary actions on your behalf, from detecting issues to restoring your pre-theft status. This comprehensive service ensures you don’t have to navigate the complexities of identity restoration alone.
Simplifying the Restoration Process
Our expert recovery advocates take on the burden of restoring your identity, allowing you to focus on your life. They handle everything from contacting creditors to filing necessary paperwork, making the process as smooth and stress-free as possible.
All-Around Protection
Comprehensive Coverage
Our identity theft protection service is like a puzzle with all pieces perfectly aligned. We provide comprehensive protection that covers every angle, ensuring your identity is safeguarded from all potential threats.
Safeguarding Against All Potential Threats
We protect against a wide range of threats, including financial, medical, and legal identity theft. Our service ensures that no matter where the threat comes from, your identity is secure.
Proactive Monitoring
Advanced Monitoring Systems
Think of our proactive monitoring as having a dedicated team of detectives constantly watching over your personal information. Our advanced monitoring system detects suspicious activities early, preventing issues before they escalate.
Early Detection of Suspicious Activities
By catching suspicious activities early, we can prevent identity theft before it happens. This proactive approach saves you from the stress and potential financial loss associated with identity theft.
Robust Safety Net Provided by a Superior Identity Theft Protection Program
Beyond Financial Reimbursement
While other plans might offer some financial reimbursement, our protection extends beyond just money. We safeguard your identity, credit, and even legal aspects, offering a full safety net that catches you no matter what.
Protecting Identity, Credit, and Legal Aspects
Our comprehensive protection includes monitoring and safeguarding your credit reports, legal documents, and personal information. This robust safety net ensures that all aspects of your identity are covered.
Personalized Assistance
Tailored Recovery Plans
In the event of identity theft, our recovery advocates are there to guide you through the entire process. They create personalized recovery plans tailored to your situation, ensuring a smooth and efficient restoration of your identity.
Guidance Through the Recovery Process
Our advocates are with you every step of the way, providing the support and guidance you need to restore your identity quickly and effectively.
Proven Track Record
Success Stories and Testimonials
Our service has successfully protected numerous clients, with testimonials highlighting our exceptional support and effective recovery. We’ve helped many individuals and families navigate identity theft crises, demonstrating our expertise and reliability.
Demonstrating Expertise and Reliability
Our proven track record showcases our commitment to protecting your identity. Our clients’ success stories and positive feedback are a testament to our high level of service and effectiveness.
Addressing Redundancies in Identity Theft Protection
Integrating Various Protective Measures
Unlike basic or bundled services that only provide partial coverage, our plan offers an all-in-one solution. By integrating various protective measures into a single comprehensive package, we eliminate the gaps left by other services.
Eliminating Gaps with a Unified Approach
This unified approach ensures you receive the highest level of protection without needing multiple subscriptions or relying on fragmented services. Our all-in-one package provides a seamless and comprehensive solution.
Customer Testimonials
Exceptional Customer Support
Check out our exceptional customer support and performance metrics, which speak volumes about our effectiveness and customer satisfaction. Our clients consistently praise our prompt and professional assistance.
Performance Metrics and Satisfaction
Our performance metrics highlight our success in preventing and resolving identity theft cases. Customer satisfaction is our top priority, and our results reflect our commitment to excellence.
Conclusion
Unparalleled Defense with Comprehensive Protection
While identity theft protection might seem ubiquitous, our comprehensive, all-in-one package provides unparalleled defense. With our service, you have a dedicated superhero team working tirelessly to keep you safe.
True Peace of Mind with Our Service
Don’t settle for incomplete protection—choose a service that offers true peace of mind. Our comprehensive identity theft protection ensures that all aspects of your identity are safeguarded, providing you with confidence and security.
Articles related to superior identity theft protection:

by Brian Thompson | Jul 23, 2024 | Uncategorized
Exceptional customer service is a cornerstone of our resource center, which is demonstrated through impressive inbound call statistics and glowing testimonials from our clients. This article delves into our performance metrics and shares real customer experiences, showcasing our commitment to customer support excellence by resolving issues promptly and efficiently.
Resource Center Inbound Call Statistics
2nd Quarter 2024 Performance:
- Abandon Rate: 1.7% (Goal: <3%)
- Average Speed of Answer: 15 seconds (Goal: <20 seconds)
- Percentage of Calls Accepted within 20 Seconds: 80.6% (Goal: >80%)
These stats underscore our dedication to answering calls swiftly and minimizing abandoned calls, ensuring that customers receive timely assistance and reinforcing our focus on customer support excellence.
Why Inbound Call Support Matters
At defend-id call support is crucial for maintaining high customer satisfaction levels. Quick response times and efficient problem resolution enhance the customer experience and build trust. Our resource center’s performance metrics highlight our ability to meet and exceed customer expectations consistently, demonstrating our commitment to customer support excellence.
Customer Testimonials: Real Experiences
Marcelina M.
“It was such a pleasure to speak with you today, you were able to identify and help me to resolve my issue quickly and on my first call! I appreciate your dedication to providing excellent customer service, I hope you’ll share this with your boss, so you can be recognized for your excellent customer service. Thank you again for your time and attention. Cheers.”
Jun Chen
“My assigned recovery advocate is the best recovery advocate ever! She is so professional and makes me feel right at ease with how she can handle my case. She is beyond helpful, and I’m glad I have her as someone to support me through this difficult time…”
The Role of Recovery Advocates
Our recovery advocates play a crucial role in providing support and guidance during identity theft incidents. Their expertise and professionalism ensure that clients feel secure and well-assisted throughout the recovery process, embodying our commitment to customer support excellence.
More Client Feedback
Richard K.
“Very thankful for everything that your Recovery Advocate has done. This issue has been completely resolved without further incidents. We truly appreciate everything that she has done thus far.”
Rendard L.
“My advocate was most kind, helpful, and very knowledgeable in the ‘identity theft’ subject matter. It was a pleasure working with her to resolve my issue…”
Angie V.
“Thank you so much for all your help and for checking back in with me now and each quarter! You really impress me, as it is clear you actually care about the people you are helping. That sort of customer service and kindness has become a rarity.”
Commitment to Professional Assistance
We are committed to providing professional assistance through our well-trained advocates. Their ability to handle complex situations with empathy and expertise is what sets our service apart, demonstrating our dedication to customer support excellence.
Additional Testimonials
Teresa J.
“Thanks to my representative for all their help. I do not know how I would have resolved the problem without their experience and guidance. It was a pleasure working with them.”
Gloria O.
“My Advocate was extremely professional and patient. He resolved my issue immediately. I am so thankful I have this program in place.”
Annette S.
“Thank you for your service. I appreciated the security and support I received during my identity theft event.”
Client Satisfaction: Key to Our Success
Client satisfaction is at the heart of our operations. The positive feedback we receive is a testament to the hard work and dedication of our team, reflecting our focus on customer support excellence.
Understanding Identity Theft Solutions
We offer comprehensive solutions for identity theft, providing clients with the resources and support they need to navigate and resolve such incidents effectively, upholding our standard of customer support excellence.
Personal Stories: Clients’ Journeys
Michael M.
“My advocate was fantastic as far as putting me at ease. Her value cannot be expressed enough.”
Kenneth K.
“Thanks to my Advocate, they have been an absolute pleasure to work with. Thank you for all your help!”
Barbara D.
“My Restoration Specialists made me feel safe during a very bad situation.”
Ensuring Customer Security
Our priority is to ensure the security and peace of mind of our clients. We take every measure to provide a safe and supportive environment during their recovery journey, showcasing our commitment to customer support excellence.
More Satisfied Clients
Kent C.
“My Advocate put me at ease after a very stressful event. Thank you again for everything.”
David H.
“Great services, all around!”
Gerald K.
“Very prompt and comprehensive service.”
Building Trust Through Customer Support Excellence
We build trust with our clients by consistently delivering excellent service. Our commitment to quality and professionalism is evident in the feedback we receive, emphasizing our dedication to customer support excellence.
Final Testimonials
Jonathon E.
“My recovery advocate was FANTASTIC!!! Thank you.”
Dean S.
“My specialists did an awesome job and was very professional.”
Thomas S.
“Very helpful and assuring me that everything will be taken care of.”
Thomas S.
“The representative I spoke with was very helpful and courteous.”
Discover how our resource center excels with exceptional inbound call statistics and heartfelt testimonials from satisfied clients, reflecting our commitment to customer support excellence.
FAQs
How quickly can I expect my call to be answered? Our average speed of answer is 15 seconds, ensuring that you receive prompt assistance.
What is the abandon rate for calls? Our abandon rate is impressively low at 1.7%, well below our goal of less than 3%.
How effective are your recovery advocates? Our recovery advocates are highly effective, providing professional and empathetic support to resolve identity theft issues efficiently.
What percentage of calls are accepted within 20 seconds? We accept 80.6% of calls within 20 seconds, demonstrating our commitment to quick response times.
How do clients feel about your services? Clients consistently provide positive feedback, praising our professional and supportive recovery advocates.
What steps do you take to ensure customer satisfaction? We prioritize customer satisfaction through quick response times, professional support, and comprehensive identity theft solutions.
Our resource center’s stellar inbound call statistics and heartfelt testimonials underscore our unwavering commitment to providing exceptional customer service. These achievements reflect our team’s dedication to resolving issues efficiently and ensuring customer satisfaction. We strive to maintain these high standards and continue delivering customer support excellence to our clients.
Related Articles to Customer Support Excellence:

by Brian Thompson | Jul 2, 2024 | General, Identity Theft
The 4th of July is an amazing day filled with fireworks, barbecues, and celebrations of our nation’s independence. Unfortunately, scammers see see it as an opportunity to exploit unsuspecting patriots. Whether it’s through phishing emails, fake sales, or counterfeit event tickets, these scams can quickly turn a fun holiday into a nightmare. This guide aims to help you recognize and avoid common 4th of July scams so you can enjoy a safe and worry-free celebration.
1. Patriotic Emails and Social Media Posts
Scammers know that patriotic feelings run high around the 4th of July. They send out emails and social media posts designed to tug at your heartstrings, often using themes related to veterans, elections, or national pride. These messages might include links that download malware onto your device or steal your personally identifiable information (PII). Be cautious: if something seems off, don’t click on it. Verify the source before engaging with any patriotic-themed content.
2. Shopping Scams
Retailers love to offer deals during the 4th of July, and bad guys take full advantage of this. They create fake websites that look like real sites, offering unbelievable discounts on popular items. Before making a purchase, ensure the website is legitimate. Use trusted retailers, look for secure payment options, and read reviews. A password manager can help keep your online shopping secure by storing and generating strong passwords.
3. Fake Event Tickets
Summer concerts, parades, and fireworks shows are highlights of the 4th of July. Unfortunately, scammers sell counterfeit tickets for these events, often through social media or classified ads. Always buy tickets from official sources or authorized sellers. Check the event and seller’s legitimacy before purchasing, and avoid deals that seem too good to be true.
Real-Life Example: Last year, “Jane” bought tickets for a local fireworks show through an ad on social media. When she and her family arrived at the park, they were told the tickets were fake. Verify tickets through official channels, or potentially lose some money and have a few crying children on your hands!
4. Fireworks Scams
In states where personal fireworks are allowed, scammers often set up temporary stands selling fake or overpriced fireworks. These vendors might disappear after a day or two, taking your money with them. To avoid these scams, buy fireworks from well-known retailers and use cash to minimize risk. If something feels wrong, walk away and report the vendor.
5. Virus Attacks and Tech Support Scams
Bad guys love holidays because people are often distracted and more careless. They might send fake alerts claiming your computer is infected, hoping you’ll download malicious software or pay for unnecessary tech support. Remember, the Social Security Office does not contact you by phone. Use reliable antivirus software and never provide personal information to unsolicited callers.
Expert Quote: “Cybercriminals capitalize on the chaos of holidays to launch attacks. Always double-check the legitimacy of any unsolicited tech support offers,” advises Ryan Smith, a cybersecurity consultant at RLS Consulting.
6. Fake Online Sales and Deals
Scammers set up fake e-commerce sites offering amazing deals on electronics, fireworks, and other popular items. These sites often look professional but are designed to steal your credit card information. Stick to well-known retailers, check for secure payment methods, and be wary of deals that seem too good to be true.
7. Vacation Rental Scams
Planning a getaway for the holiday? Scammers post fake rental listings with attractive prices to lure you in. Always book through trusted platforms, read reviews, and verify the property’s details with the host. Avoid paying through wire transfers or prepaid debit cards, which are hard to trace and recover.
Local Resource: If you suspect a vacation rental scam, report it to the Federal Trade Commission (FTC) through their website.
8. Phishing Emails and Texts
Phishing scams are common during the 4th of July, with fraudsters sending messages that appear to come from reputable companies. These emails and texts might offer exclusive deals or contest entries. Scrutinize any unexpected messages, verify the sender’s information, and never click on suspicious links. Use security solutions to protect against phishing attacks.
Question: Have you ever received a suspicious email or text around a holiday? How did you handle it?
9. Charity Scams
During patriotic holidays, scammers often pose as charities supporting veterans or other causes. Research any charity before donating. Use websites like Charity Navigator to verify legitimacy, and always donate through the charity’s official website. Avoid giving out personal information or donating via cash or wire transfer.
Real-Life Example: “John” donated $75 to what he thought was a veterans’ charity. It turned out to be a scam, and his personal information was compromised. Now, he always checks Charity Navigator before making any donations.
10. Counterfeit Merchandise
Scammers often sell fake patriotic merchandise, from apparel to fireworks, during the 4th of July. These items can be unsafe and fail to meet safety standards. Buy from reputable retailers, check product reviews, and verify the seller’s authenticity to avoid wasting money on counterfeit goods.
11. Deceptive 4th of July Sales
Scammers exploit the holiday shopping frenzy by creating fake sales on popular items. To protect yourself, shop only from trusted retailers, verify secure payment options, and use prepaid credit cards for online purchases. Always double-check URLs to ensure you’re on the correct website.
12. Giveaways and Sweepstakes Scams
Fake giveaways and sweepstakes are another tactic scammers use to collect your personal information. Be cautious of offers that seem too good to be true. Verify the legitimacy of contests through official channels and never provide sensitive information.
Consider using a security tool like defend-id to monitor your credit for any unusual activity after entering sweepstakes or giveaways.
13. Social Media Scams
Scammers target users on social media with fake ads and posts. Report and block suspicious accounts and avoid clicking on unknown links. Using a VPN can help protect your online privacy and security.
14. Holiday-themed Text Messages
Fake holiday-themed text messages can contain malicious links. Never click on links from unknown senders. Report suspicious messages and block the numbers to prevent future scams.
15. General Cyber Safety Tips
- Keep your antivirus software updated: Regularly update your antivirus program to protect against new threats.
- Use a VPN: A VPN can help keep your online activity private and secure.
- Verify URLs: Always check the URL before entering personal information on a website.
- Update passwords: Regularly update your passwords and use a password manager to keep them secure.
Don’t let 4th of July scams ruin your summer!
By staying vigilant and following these tips, you can protect yourself from 4th of July scams and enjoy a safe holiday. Spread awareness among your friends and family to help them stay safe as well.
Share this article on social media to spread awareness about 4th of July scams. Subscribe to our newsletter for more tips on cybersecurity and scam prevention.
4th of July scams FAQs
- What are common 4th of July scams?
- Common scams include fake sales, counterfeit event tickets, phishing emails, and fake charity solicitations.
- How can I identify a fake online sale?
- Look for red flags like poorly designed websites, unusually low prices, and lack of contact information. Stick to known retailers and use secure payment methods.
- What should I do if I suspect a phishing email?
- Scrutinize the message, verify the sender’s information, and avoid clicking on suspicious links. Use security solutions to protect against phishing attacks.
- How can I verify the legitimacy of a charity?
- Research the charity on websites like Charity Navigator or the Better Business Bureau. Use credit cards or checks for donations and verify the request through the charity’s official website.
- What are the risks of buying fireworks from roadside stands?
- Risks include purchasing fake or overpriced fireworks and sharing payment information with fraudulent sellers. Buy from reputable vendors and use cash to avoid scams.
Detailed Steps for Reporting Scams
- Identify the Scam: Gather all information about the scam, including emails, texts, or receipts.
- Report to Authorities: Contact the FTC through their website or call their hotline. Report identity theft to the Identity Theft Resource Center.
- Notify Financial Institutions: Inform your bank or credit card company to freeze or monitor your accounts.
- Change Passwords: Update your passwords and use a password manager for added security.
- Monitor Credit: Use tools like Credit Karma to keep an eye on your credit report for any unusual activity.
- Spread Awareness: Share your experience with friends and family to help them avoid similar scams.
Articles related to 4th of July scams:

by Brian Thompson | Jun 26, 2024 | Employee Benefits, Identity Theft
Identity theft is a serious crime that can devastate your finances and your life. When someone steals your personal information, they can use it to open new accounts in your name, run up debts, and damage your credit score. Here we will discuss How to Protect Your Credit from Identity Theft.
A low credit score makes it difficult to get approved for loans, credit cards, and other forms of credit. It can also make borrowing money more expensive since you will likely have to pay higher interest rates. A low credit score also makes it difficult to rent an apartment, get a job, or even get insurance.
How Identity Theft Can Ruin Your Credit Score
Identity thieves can damage your credit in various ways. Here are a few examples:
- Opening New Accounts: Thieves can open new accounts in your name and not make payments, leading to collections and even bankruptcy.
- Maxing Out Credit Cards: They can max out your existing credit cards, significantly damaging your credit score.
- Changing Addresses: They can change the address on your accounts so you don’t receive important billing information, leading to missed payments and further damage to your credit score.
- Filing for Bankruptcy: Thieves can file for bankruptcy in your name, which will stay on your credit report for up to 10 years, making it very difficult to get approved for credit.
The Impact of a Low Credit Score Due to Identity Theft
A low credit score can significantly impact your life. Here are a few examples:
- Loan Approval: You may not be able to get approved for a loan to buy a car or a home.
- Higher Interest Rates: You may have to pay higher interest rates on credit cards and loans.
- Difficulty Renting or Getting a Job: You may have difficulty renting an apartment or getting a job.
- Insurance Issues: You may have difficulty getting insurance.
- Job Promotions and Scholarships: You may be denied a job promotion or a scholarship.
The Emotional Impact of Identity Theft
Identity theft not only ruins your credit but also has a significant emotional impact on victims. Victims may experience feelings of anger, anxiety, stress, and depression. They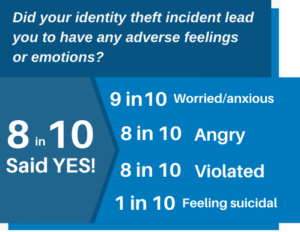 may also feel violated, betrayed, and helpless.
may also feel violated, betrayed, and helpless.
According to a study by the Identity Theft Resource Center, 70% of identity theft victims experience emotional distress. The study also found that victims are more likely to experience anxiety, depression, and post-traumatic stress disorder (PTSD) than people who have not been victims of identity theft.
If you are a victim of identity theft, it is important to seek help from a mental health professional. Talking to someone about what you are going through can help you cope with the emotional impact of the crime.
Steps to Recover from Identity Theft
If you find yourself a victim of identity theft, don’t panic. Here’s a systematic guide to help you regain control and mitigate any potential damage:
- Notify Your Insurance Provider: If you have identity theft insurance, inform them first for guidance and help.
- Alert Your Financial Institutions: Contact your bank and credit card issuers immediately to halt transactions and secure accounts.
- Contact Affected Companies: Reach out to companies where the theft occurred to inform their fraud department.
- Implement a Fraud Alert: Place a fraud alert on your credit with one of the three major credit bureaus.
- Review Your Credit Reports: Access your free credit reports from AnnualCreditReport.com and report any discrepancies.
- File a Report with the FTC: Visit identitytheft.gov to file a comprehensive identity theft report with the Federal Trade Commission (FTC).
- Report to Local Law Enforcement: Filing a police report provides an official record of the identity theft.
- Secure Your Online Presence: Change all online account passwords, consider using a password manager, and activate two-factor authentication.
- Replace Important Documents: Apply for replacements for stolen IDs like your driver’s license, passport, and Social Security card.
- Subscribe to Identity Theft Protection Services: Consider services like defend-id which monitor your financial and digital presence, providing alerts and insurance.
Steps to Take if You Suspect Identity Theft
If you suspect you’ve fallen victim to identity theft, take these essential steps promptly:
- Contact Your Financial Institutions: Reach out to your bank and credit card issuers immediately to freeze your accounts and halt unauthorized transactions.
- Report to Your Identity Theft Insurance Provider: Notify your provider right away for guidance and resources, including legal and financial assistance.
How Identity Theft Protection Services Help
Identity theft protection services, such as defend-id, play a crucial role in safeguarding your online and financial accounts from fraudulent activities. With defend-id’s advanced monitoring technology, subscribers receive alerts about potential fraud approximately four times faster than many competing services.
- Comprehensive Monitoring and Swift Alerts: defend-id provides detailed monitoring by keeping track of your personal and financial account activities. If something unusual is detected, defend-id promptly sends out an alert.
- Robust Insurance Coverage: defend-id offers significant financial protection with an insurance policy that can provide up to $1,000,000 in compensation for eligible losses caused by identity theft.
Protecting Yourself from Identity Theft and Fraud
Protecting yourself from identity theft and fraud is crucial. One effective way to safeguard your personal information is by using comprehensive services like defend-id, which offers robust monitoring and insurance coverage.
- Comprehensive Insurance Coverage: defend-id provides each plan member with a $1,000,000 insurance policy.
- Real-Time Monitoring and Alerts: defend-id monitors your financial and online accounts continuously, alerting you swiftly to any suspicious activity.
- Family Protection: defend-id’s Family Plan extends protection to up to five family members, including both adults and children.
- Trial Period: defend-id offers a 14-day free trial, allowing you to experience their service before committing.
Taking proactive steps by enrolling in a service like defend-id can provide peace of mind and significantly reduce the chances of suffering from identity theft and fraud.
Tactics Used by Identity Thieves
Identity thieves deploy various tactics to access personal data. They might steal your wallet, ID, or mail containing personal information, use a change-of-address scam, send phishing emails, texts, and calls, buy your data off the Dark Web, hack into your email, or intercept your data on an unsecured Wi-Fi network. Understanding these methods allows you to be more vigilant and take preventative measures to secure your personal and financial information.
Take Action Today
Identity theft is a serious crime, but you can protect yourself by taking necessary steps to safeguard your personal information and monitoring your credit reports regularly.
Resources:
- The Federal Trade Commission (FTC): 1-877-438-4338
- The Identity Theft Resource Center: 1-888-400-5530
- The National Association of Consumer Advocates: 1-800-644-7222
Don’t let identity theft ruin your credit and your life. Take action today to protect yourself!
Articles related to How to Protect Your Credit from Identity Theft:

by Brian Thompson | Jun 12, 2024 | Identity Theft
Safeguarding our personal information is crucial! Yet, many of us operate under certain misconceptions, trusting myths that could leave us vulnerable. Welcome to “Unmasking Identity Theft: Debunking 9 Common Myths.” This blog post aims to shed light on the most common myths surrounding identity theft protection and the truths hiding behind them. Dive in with us as we demystify and decode the realities of identity safety in our interconnected world.
Myth #1
“If I have identity theft protection, I’m 100% safe from all scams and fraud!”
Truth: While identity theft protection can alert you to suspicious activity, it doesn’t prevent the theft from happening in the first place. Always stay vigilant and cautious with your personal data!
Reality Check
While having identity theft protection is a proactive step towards securing your personal information, it’s important to understand its limits. These services are designed to monitor and alert you to suspicious activities, but they don’t take action on your behalf. You won’t find them automatically blocking access to your accounts, changing your passwords, or filing claims for you. That’s your role. Identity theft protection services act as an early warning system, but they rely on you to take decisive action.
Myth #2
“I don’t need identity theft protection; I’m careful with my personal info!”
Truth: Even if you’re cautious, data breaches at companies where you have accounts can expose your information. Identity theft protection helps monitor and alert you of potential threats.
Myth #3
“Credit monitoring is the same as identity theft protection.”
Truth: Credit monitoring is just one component. Identity theft protection often includes credit monitoring, but also checks other areas for fraud like bank accounts, social security, and even dark web scans! However, it’s important to recognize that while these services are comprehensive, they do not cover every single account type. Many programs focus primarily on credit-based accounts such as banking and credit cards, and some extend to popular social media platforms. Yet, it is less common for these programs to monitor other types of accounts like those for shopping, news sites, membership portals, and smaller social media platforms.
Myth #4
“Free credit reports offer the same protection as paid identity theft protection services.”
Truth: Free credit reports show your credit history, but they don’t actively monitor or alert you to suspicious activity. For more proactive monitoring, consider dedicated services.
Myth #5
“Once I’ve been a victim, I won’t be targeted again.”
Truth: Unfortunately, victims of identity theft can be targeted multiple times. It’s vital to ensure ongoing protection even after an incident.
Myth #6
“A strong password is enough to protect me.”
Truth: Strong passwords are essential, but cybercriminals have various methods like phishing and data breaches to bypass them. Comprehensive protection goes beyond just passwords!
Myth #7
“Only adults are at risk of identity theft.”
Truth: Sadly, children can also be victims. Their clean credit histories can be attractive to thieves. It’s essential to monitor their information too.
Myth #8
“I would instantly know if I became a victim.”
Truth: Some forms of identity theft can go undetected for months or even years! Regular monitoring can help catch issues before they escalate.
Myth #9
“Only people who shop online are at risk of identity theft.”
Truth: Identity theft can occur through various channels, not just online shopping. While online transactions are a common target due to the digital exchange of personal and financial information, identity thieves can also exploit physical documents, phone scams, and even public Wi-Fi networks. It’s essential to protect your personal information in all environments, both online and offline.
Do Data Breaches Always Lead to Identity Theft?
A clear understanding of the relationship between data breaches and identity theft is crucial. Not every data breach results in identity theft. A data breach occurs when there is unauthorized access to private data, but it does not necessarily mean the information was used maliciously. However, if the exposed data is accessed and misused by cybercriminals, it often leads to identity theft. Thus, while breaches raise the risk of identity theft, they don’t always result in such crimes. The actual impact depends on whether the breached information is criminally exploited.
Understanding Your Coverage
Identity theft can be financially devastating, but not all losses may be covered by your identity theft protection plan. It’s important to understand that while some plans include insurance for certain losses, coverage varies significantly among different providers and policies.
Vulnerability of Personal Data
Despite the immense resources companies allocate to cybersecurity, the harsh reality is that personal data can still be hacked or stolen. Major incidents such as the Equifax breach, which affected 230 million consumers, underscore the pervasiveness of the risk. From large corporations to individual users, no one is entirely immune to potential cybersecurity threats. Adopting identity theft protection services can be a start. These services can’t prevent all forms of data breaches but can enhance the security of your accounts.
Internal Threats and Other Sources of Identity Theft
It’s a common misconception that identity theft only emerges from massive corporate breaches. While these events are significant and newsworthy, they are far from the only source of such crimes. Identity thieves often exploit lesser-known access points, such as videogame systems and social media platforms, to harvest personal information. Additionally, phishing schemes frequently target specific companies, sometimes for sums as trivial as $7—a lucrative prospect for a disgruntled former employee. Moreover, an alarming 30% – 50% of all identity theft cases originate not from shadowy outsiders but from within the workplace itself, committed by coworkers who misuse their access to sensitive data.
Is Identity Theft Protection Just Scanning Software?
Identity theft protection often includes credit monitoring, but also checks other areas for fraud like bank accounts, social security, and even dark web scans! However, it’s important to understand that these services are not just set-it-and-forget-it solutions. While they provide comprehensive monitoring and alert systems, they do not autonomously manage security tasks such as blocking your accounts or changing your passwords. As a user, you will need to take action based on the alerts you receive. Essentially, identity theft protection services are proactive tools designed to notify you of potential threats, enabling you to take timely preventive measures.
Is Identity Theft Protection a Turnkey Solution?
The primary role of identity theft protection services is to monitor and alert the user to suspicious activities or potential threats, prompting them to take appropriate action. Users are expected to actively manage and secure their accounts, update their passwords regularly, and initiate any necessary legal or financial claims. Identity theft protection services do not handle actions such as closing or securing your accounts, updating your passwords, or managing the process of filing claims.
Understanding the Realities of Identity Theft
Understanding the realities of identity theft is the first step in truly protecting yourself. By debunking these myths, we hope to provide clarity and pave the path for more informed decisions. “Unmasking Identity Theft: Debunking 9 Common Myths” underscores the need to stay updated, vigilant, and proactive. Remember, in the realm of digital safety, knowledge isn’t just power; it’s your best line of defense. Stay safe, stay informed, and always prioritize your digital well-being.
Related Articles:




 may also feel violated, betrayed, and helpless.
may also feel violated, betrayed, and helpless.