
by Brian Thompson | Jun 11, 2024 | Employee Benefits, Identity Theft
Identity Theft Protection as an Employee Benefit
Identity theft is a growing concern that can have devastating effects on individuals and businesses alike. As an employer, integrating identity theft protection as an employee benefit into your wellness program is not just a valuable benefit but a necessity. Below we explore why identity theft protection is crucial for employee wellness and how it can enhance your organization’s overall productivity and employee satisfaction.
Understanding Identity Theft
Identity theft occurs when someone uses another person’s personal information without permission, typically for financial gain. This can include stealing Social Security numbers, credit card information, or other sensitive data. According to the ITRC Impact Report, identity theft can lead to severe emotional and financial distress, making it difficult for victims to perform effectively at work.

The Toll of Identity Theft on Employees
The emotional and financial stress caused by identity theft can significantly impact employees’ well-being and job performance. A study found that 9 in 10 victims of identity theft experience negative emotions such as worry, anxiety, and anger. Moreover, 8 in 10 reported employment problems related to identity theft, including issues with coworkers and supervisors. When employees are distracted by personal crises, their productivity and morale can suffer, leading to higher turnover and lower engagement.
Why Employers Should Offer Identity Theft Protection
Employers have a unique opportunity to support their workforce by offering identity theft protection as an employee benefit as part of their wellness programs. By doing so, companies demonstrate a commitment to their employees’ overall well-being, which can enhance employee loyalty and employee satisfaction. Protecting employees’ identities helps them feel secure, enabling them to focus on their work without the distraction of dealing with identity theft issues.
Boosting Corporate Security Through Identity Protection Benefits
-
Social Media Protection
Implementing identity protection measures can play a critical role in safeguarding a company’s social media integrity. If an employee’s social media account is compromised, the repercussions can be significant. Unauthorized users may spread misinformation, engage in phishing attacks against the employee’s contacts, or even misuse the company’s brand to commit fraud. An effective identity protection program actively monitors for such irregular activities, promptly detects unauthorized access, and alerts the employees, thereby minimizing potential harm to the company.
-
Comprehensive Employee Education
Ongoing education is another cornerstone of strengthening corporate security via identity protection benefits. Employees serve as the first line of defense against security breaches. Regular training sessions should cover:
- The importance of robust password practices and account security measures.
- Awareness of the latest techniques used by cybercriminals and identity thieves.
- Updates on recent data breaches and security threats which could potentially impact the company.
This continual education helps in building a knowledgeable workforce that can recognize and mitigate threats effectively.
-
Protection of Sensitive Corporate Information
Identity protection benefits extend beyond personal data to include critical corporate assets like company credit cards, usernames, and passwords. For employees entrusted with accessing sensitive corporate information, safeguarding these assets is paramount. Identity protection services ensure that all components are closely monitored for any unauthorized access or transactions, further securing corporate financial and digital assets.
Through these measures, identity protection benefits not only secure individual employees but also fortify the organization’s overall cybersecurity framework.
Employee Engagement and Business Success
Employee engagement stands as a cornerstone of business success. Engaged employees drive productivity, foster a positive work environment, and contribute to the economic vitality of their organizations. Disengaged employees, on the other hand, can lead to substantial financial losses, with engagement research indicating potential costs to businesses in the billions annually.
One prevalent issue that can swiftly erode employee engagement is identity theft. This personal crisis demands considerable time and emotional energy to resolve, often diverting the employee’s focus and commitment away from work responsibilities. The process is fraught with uncertainty and stress, making it difficult for employees to maintain their usual levels of engagement at work. The resultant impact is not just on the employees’ productivity, but also on their morale and loyalty to the company, ultimately threatening overall business stability and success.
How Identity Protection Benefits Enhance Corporate Security
Employers have a unique opportunity to support their workforce by offering identity theft protection as an employee benefit as part of their wellness programs. By doing so, companies demonstrate a commitment to their employees’ overall well-being, which can enhance employee loyalty and employee satisfaction. Protecting employees’ identities helps them feel secure, enabling them to focus on their work without the distraction of dealing with identity theft issues.
Moreover, a robust identity protection program doesn’t just offer security after the fact; it provides comprehensive, preventative solutions aimed at mitigating risks before they occur. Such measures include educating employees on the importance of data security, protecting sensitive information like corporate credit cards, usernames, and passwords, and implementing tools to monitor and protect against breaches on social media platforms.
These proactive steps ensure that employees can dedicate their attention to their career growth, while the company benefits from maintaining a secure, engaged, and focused workforce. By integrating these elements into their corporate security strategy, companies can shield themselves and their employees from the profound impacts of identity theft, making the workplace a safer and more productive environment.Implementing Identity Theft Protection in Wellness Programs
Implementing Identity Theft Protection in Wellness Programs
To effectively integrate identity theft protection as an employee benefit into your wellness program, consider the following steps:
- Choose Comprehensive Services: Select a service that offers comprehensive monitoring and recovery solutions. defend-id, for example, provides fully managed recovery services, credit monitoring, dark web monitoring, expense reimbursement insurance, and many other features.
Expanding on the Details:
- Identity Theft Expense Reimbursement: Ensure that the service includes a robust identity theft expense reimbursement. It’s vital that the plan offers substantial coverage to handle the potential expenses arising from fraud. For instance, a standard should be set at a minimum of $1 million in coverage. This coverage should be backed by a reputable insurance provider, such as AIG, guaranteeing that the funds are available for a breadth of costs including, but not limited to, an employee’s lost wages, legal fees, medical records request fees, CPA fees, childcare fees, and more.
- Enhanced Dark Web Monitoring: The identity protection plan should also feature a proactive dark web monitoring service. This means that employees should have the option to register sensitive documents, like driver’s licenses and credit cards, with the service provider. In the event that these registered documents are found on the dark web, the employee should be alerted immediately. Following the alert, the provider should actively collaborate with the employee to address and resolve the issue, ensuring minimal impact and swift action.
- Educate Employees: Raise awareness about the risks of identity theft and how to prevent it. Provide regular training sessions and resources to help employees understand the importance of protecting their personal information.
- Offer Flexible Plans: Provide flexible product and pricing structures to meet the diverse needs of your employees. Consider offering both individual and family plans to ensure all employees and their dependents are protected.
- Promote the Benefits: Communicate the advantages of identity theft protection to your employees. Highlight how these services can save time, reduce stress, and provide peace of mind.
Success Stories and Testimonials

Real-life examples and testimonials can be powerful tools to illustrate the benefits of identity theft protection. One employee shared their experience with defend-id, stating, “My Recovery Advocate was a great help. This was my first experience with ID theft. He helped me through all of it, every step because I was lost. I felt the entire process was easy and a ton of weight is now off my shoulders”. Such stories emphasize the real impact these services can have on employees’ lives.
Check out a case study of a mortgage company in CT here: Case Study
Final thoughts
Identity theft protection as an employee benefit is an essential component of a comprehensive employee wellness program. By offering these services, employers can help mitigate the emotional and financial stress caused by identity theft, ultimately enhancing workplace productivity and employee satisfaction. Investing in identity theft protection is not just a benefit; it is a proactive step toward fostering a secure and focused workforce.
Encourage your organization to prioritize identity theft protection as an employee benefit today. For more information on integrating these services into your wellness program, visit defend-id.
defend-id.
Articles related to identity theft protection employee benefit:

by Brian Thompson | Jun 5, 2024 | General, Identity Theft
Traveling can be exciting, but it also comes with risks, such as identity theft. Vacationers are often more relaxed and less vigilant about their personal information, making them easy targets for thieves. However, with a few simple precautions, you can enjoy your trip without worrying about your personal information falling into the wrong hands. Here are essential tips to protect your identity while traveling and ensure a secure vacation.
1. Secure Your Personal Documents
Before you leave for your vacation, make sure to secure your personal documents. This includes your passport, driver’s license, and any other identification cards you may be carrying. Keep these documents in a secure location, such as a hotel safe or a locked suitcase. Avoid carrying unnecessary documents with you, and if you need to bring them, make sure to keep them hidden and out of sight. By taking these precautions, you can minimize the risk of your personal information being stolen while you’re traveling.
2. Use a VPN When Accessing Public Wi-Fi
When you’re traveling and need to connect to public Wi-Fi, it’s important to use a virtual private network (VPN) to protect your identity. Public Wi-Fi networks are often unsecured, making it easy for hackers to intercept your personal information. A VPN creates a secure connection between your device and the internet, encrypting your data and keeping it safe from prying eyes. By using a VPN, you can browse the internet, check your email, and access your online accounts without worrying about your personal information being stolen.
3. Be Cautious with Your Credit Cards
When traveling, it’s important to be cautious with your credit cards to protect your identity. Avoid using your credit card for purchases at unsecured or unfamiliar locations, as these may be more susceptible to skimming devices or fraudulent activity. Instead, opt for cash or use a secure payment method such as a mobile wallet or chip-enabled card. Additionally, regularly monitor your credit card statements and report any suspicious activity immediately to your credit card company. By taking these precautions, you can enjoy your vacation without the worry of identity theft.
4. Avoid Oversharing on Social Media
While it may be tempting to share every detail of your vacation on social media, it’s important to exercise caution. Oversharing can make you a target for identity theft, as criminals can use the information you post to piece together your personal details. Avoid posting your exact travel dates, location, or any other sensitive information that could be used to compromise your identity. Instead, wait until you return home to share your vacation memories. By being mindful of what you share online, you can help protect your identity while traveling.
5. Set Up a Mail Hold
If you’re going to be away from home for more than a few days, submit a mail hold to the U.S. Postal Service for up to 30 days. You can retrieve your mail once the hold has expired. A mail hold can keep bank statements, credit card bills, and other mail from being used to steal your identity. To hold your mail longer or to reroute your mail, sign up for the Postal Service’s forwarding service.
6. Don’t Bring Unneeded Documents and Cards
Travelers typically need to carry a driver’s license or identification card, travel credit cards, insurance cards, and possibly a passport. But you should leave behind your Social Security card, birth certificate, and other documents that have sensitive personal information. In other words, your wallet, purse, or backpack shouldn’t hold documents and cards that you may want to bring but don’t need to bring.
7. Be Careful at ATMs
For identity thieves, an ATM can be a money-making machine. For instance, they might install a skimming device or shimming device on an ATM to capture card numbers and PINs. To protect your card number and PIN at an ATM when you’re traveling:
- Use a bank-operated ATM rather than a non-bank ATM. Non-bank ATMs, found at places like convenience stores, might not be as safe as those overseen by banks and other financial institutions.
- Change your ATM passcode before and after your trip.
- Use your hand to block the ATM keypad. This can help prevent a person or a hidden camera from seeing your PIN as you’re typing it.
8. Act Quickly if a Card Is Lost or Stolen
If your credit or debit card has been lost or stolen while traveling, report it right away to the card issuer. This may help prevent or minimize financial harm. You can contact the card issuer by looking for the customer service phone number on the card or finding it on the card issuer’s website or app. Federal law safeguards consumers against steep financial losses from a lost or stolen credit or debit card. In the case of a lost or stolen credit card, you might be responsible for as much as $50 in unauthorized charges (though many cards offer zero liability protection). For a lost or stolen debit card, your financial liability depends on how fast you report that the card went missing.
9. Consider an Identity Monitoring Service to protect your identity while traveling
Adding an identity monitoring service to your security toolkit could give you some peace of mind while you’re traveling. An identity monitoring service like the one offered by Defend-ID tracks personal information in credit applications, on websites, in public records, and in other places to spot possible signs of identity theft, and may also offer ID theft insurance.
Frequently Asked Questions
What should I do if my identity is stolen while traveling?
- Contact your providers: Reach out to all of your banks and credit card companies, not just the ones directly involved in the identity theft. You might be advised to close existing accounts and open new ones to help avoid problems.
- Contact the authorities: File identity theft reports with a local law enforcement agency and the FTC.
- Freeze your credit files: …with the three major credit reporting agencies—Experian, TransUnion, and Equifax. A credit freeze severely limits access to your credit information. You can unfreeze your files at any time.
- Review your recent transactions: Go through your bank and credit card accounts online to see whether any suspicious activity shows up. If it does, reach out to your bank or credit card company as soon as possible.
- Monitor your credit report: Obtain your credit report from each of the three credit bureaus to keep an eye out for any suspicious activity. You can also get your reports from all three bureaus weekly at AnnualCreditReport.com.
- Change online passwords: This is especially important for bank accounts and credit card accounts.
Should You Travel With Your Social Security Card?
You should never travel with your Social Security card. Instead, leave it at home in a safe place. In fact, the Social Security Administration advises not carrying your Social Security card with you at all, whether you’re traveling or not. Instead, share your card only when it’s required, which the federal agency says rarely happens.
Does Travel Insurance Cover Credit Card Theft?
Travel insurance might cover credit card theft. However, the coverage likely won’t include reimbursement for financial losses. Rather, a travel insurance company’s representatives can help you cancel credit cards, file a police report, and carry out other tasks associated with credit card theft.
By following these tips, you can significantly reduce the risk of identity theft while traveling and enjoy a secure vacation. Remember, while there is no foolproof way to prevent identity theft, taking these precautions can help you stay safe and protect your personal information.
Article related to protecting your identity while traveling
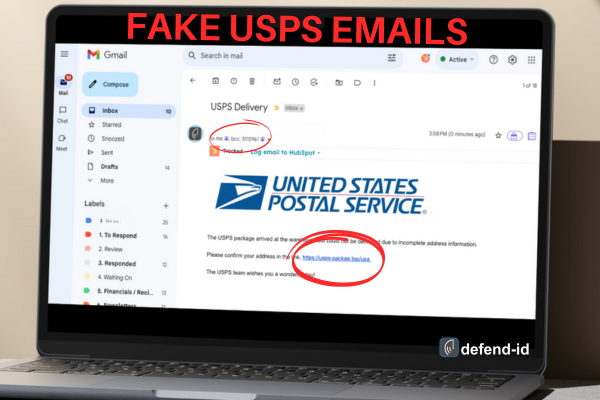
by Brian Thompson | May 29, 2024 | Identity Theft
Beware of Fake USPS Emails: Protect Your Personal Information
Understanding the Scam
Scammers are constantly evolving their tactics to deceive unsuspecting individuals, and one of the prevalent scams involves fake USPS emails. These emails often contain fraudulent information about an attempted or intercepted package delivery and prompt the recipient to click on a link to find out more about the delivery status. Unfortunately, clicking on this link can activate malware designed to steal personal information. Information such as usernames, passwords, and financial account numbers stored on your computer or mobile device.
How the Fake USPS Emails Scam Works
Scammers send emails that look convincingly like they are from USPS, using official logos and language to trick recipients. These fake USPS emails typically include:
- A Subject Line Indicating Delivery Issues: Subjects may read “USPS Delivery Failure Notification” or similar, indicating that there was an issue delivering a package.
- Fraudulent Delivery Information: The body of the email often states that a package was attempted to be delivered on a specific date, but for some reason, it could not be completed.
- A Malicious Link: Recipients are instructed to click on a link to print a delivery label or to find out more about the delivery status. Clicking this link can install malware on your device.
Once the malware is installed, it can log your keystrokes, steal your personal information, and gain access to your financial accounts.
Identifying Fake USPS Emails
To protect yourself from these scams, it’s crucial to recognize the tell-tale signs of fake USPS emails:
- Poor Grammar and Spelling Errors: Legitimate organizations typically do not send out emails with grammatical errors or spelling mistakes. Scammers often make these errors, so it’s a red flag if you notice them.
- Sense of Urgency: Scammers often create a sense of urgency, stating that immediate action is required, or there will be dire consequences. This tactic is meant to pressure you into acting quickly without thinking.
- Requests for Personal Information: USPS will never ask for personal information via email. If an email requests personal information under the guise of reconfirming details, it is likely a scam.
- Unusual Sender Email Address: Check the sender’s email address. Scammers often use addresses that look similar to official ones but may have slight variations or unusual domains.
- Unexpected Package Notifications: The USPS does not notify customers about package delivery attempts by email. If you receive such a message, it is best to assume it is fraudulent.
Real-life Examples of Fake USPS Emails
Customers being targeted will receive an email with a subject line like “USPS Delivery Failure Notification.” The email states that a package was attempted to be delivered on a certain date but could not be completed. It then instructs the recipient to click on a link to print a delivery label and take it to their local post office to pick up the package. This link, however, installs malicious software on the recipient’s computer, logging keystrokes and potentially obtaining personal identification information and account details.
Protecting Yourself from Fake USPS Emails and Email Scams
Here are some practical steps you can take to protect yourself from falling victim to fake USPS emails and other phishing attacks:
- Be Skeptical of Unsolicited Emails: Always be cautious of unexpected emails, especially those that claim you have a package waiting or need to take immediate action.
- Check the Sender’s Email Address: Look closely at the sender’s email address. Legitimate emails from USPS will come from an official domain, not a random or suspicious-looking address.
- Hover Over Links Without Clicking: Before clicking on any link, hover over it with your mouse to see the URL. If it looks suspicious or unfamiliar, do not click on it.
- Verify Information with USPS Directly: If you are unsure about an email, contact USPS directly using a verified phone number or their official website. Do not use any contact information provided in the suspicious email.
- Forward Suspicious Emails to USPS: If you receive a suspicious email, forward it to SPAM@USPIS.gov. This helps USPS investigate and address the issue.
- Keep Your Computer and Software Updated: Regularly update your operating system, antivirus software, and any other applications to protect against malware and other threats.
What to Do if You Clicked on a Link in Fake USPS Emails
If you have clicked on a link in fake USPS emails, take the following steps immediately:
- Disconnect from the Internet: Temporarily disconnect your computer from the internet to prevent further data transmission.
- Run a Full Virus Scan: Use your antivirus software to run a full system scan. Remove any detected threats.
- Change Your Passwords: Change the passwords for your email, financial accounts, and any other accounts that may have been compromised. Use strong, unique passwords for each account.
- Monitor Your Accounts: Keep a close eye on your financial accounts and credit reports for any unusual activity. Report any suspicious transactions to your bank or credit card company.
Conclusion
Scams are a growing threat, but with the right knowledge and precautions, you can safeguard your personal information. Always be wary of emails that seem suspicious, and remember that the USPS will never notify you about package deliveries via email. If in doubt, contact the USPS directly to verify the authenticity of any communication. Stay safe and protect yourself from fake USPS emails and other scams by following these simple guidelines.
By staying vigilant and recognizing the signs of a scam email, you can protect your personal information from falling into the hands of cybercriminals. Always be cautious when receiving unsolicited emails, especially those that request personal information or prompt you to click on links. Remember, it is better to be safe and verify the legitimacy of an email than to risk compromising your personal information.
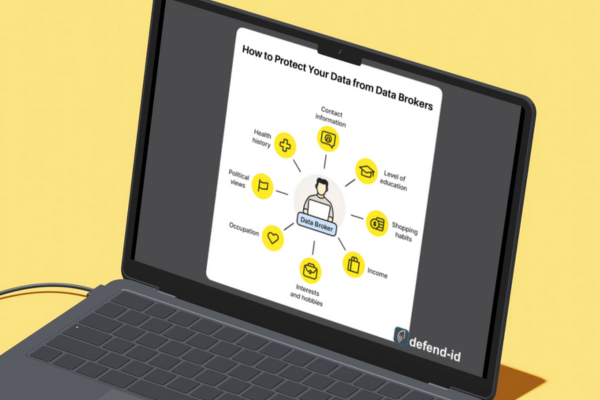
by Brian Thompson | May 22, 2024 | Uncategorized
Have you ever wondered how those targeted ads seem to know exactly what you’re interested in? Or why spam emails flood your inbox with extreme precision? The answer lies in the world of data brokers – companies that collect and sell your personal information to anyone willing to pay. It’s crucial to protect your data from data brokers to maintain your privacy and security.
What Are Data Brokers?
Data brokers are businesses that specialize in collecting data about individuals from various sources. They gather details such as your name, address, purchasing habits, online behavior, and even your beliefs. Companies then purchase this information to create targeted marketing campaigns, influencing what you see and buy online. Understanding how to protect your data from data brokers is essential in this digital age.
How Do Data Brokers Collect Data?
Data brokers use a variety of methods to gather information:
- Public Records: Data from government databases like property records, voter registrations, and court documents.
- Online Tracking: Cookies and web beacons track your browsing habits across websites.
- Social Media: Information shared on platforms like Facebook, Twitter, and Instagram.
- Purchasing Data: Retailers sell purchase histories and customer information.
- Surveys and Contests: Data from forms you fill out online or at events.
The Risks of Data Brokerage
While the idea of data brokers might seem harmless, the reality can be concerning:
- Privacy Invasion: Your personal life is exposed without your knowledge or consent.
- Identity Theft: Detailed information about you can be exploited by hackers and scammers.
- Loss of Control: Once your data is out there, it’s challenging to get it back or control its use. Learning how to protect your data from data brokers can mitigate these risks.
How to Protect Your Data and Remove It from Data Broker Sites
Protecting your data requires proactive steps. Here’s how you can start:
Opt-Out Procedures
Many data brokers allow you to opt-out of their databases. Here are steps for some of the major ones:
- Acxiom
- Visit Acxiom’s opt-out page.
- Fill out the online form with your personal information.
- Submit the form and follow any additional instructions.
- Experian
- Go to Experian’s data removal site.
- Complete the required information fields.
- Confirm your identity and submit your request.
- Equifax
- Navigate to Equifax’s opt-out page.
- Enter your personal details.
- Submit your opt-out request.
Other notable data brokers include Intelius, Spokeo, and PeopleFinder. Each has its own opt-out process, typically found on their websites.
Data Removal Services
Consider using services that specialize in data removal:
- DeleteMe: A subscription service that removes your information from various data broker sites.
- PrivacyDuck: Offers personalized data removal services to enhance your privacy.
- Many identity theft protection services are starting to offer this service as well.
Best Practices
In addition to opting out and using removal services, follow these best practices to protect your data from data brokers:
- Privacy Settings: Adjust settings on social media to limit who can see your information.
- Monitor Your Credit: Regularly check your credit report for any suspicious activity.
- Encrypted Communication: Use tools like Signal or WhatsApp for private conversations.
- Be Cautious: Think twice before sharing personal details online or with unfamiliar entities.
Conclusion
Data brokers play a significant role in the digital landscape, often without our knowledge or consent. By understanding how they operate and taking steps to protect your data from data brokers, you can regain control over your personal data. Start today by opting out of major data broker sites and implementing privacy best practices to safeguard your information.
Protecting your privacy is not just about avoiding ads; it’s about keeping your personal life secure and private. If you’re looking for comprehensive identity theft protection, consider services like Aura, which can help monitor and protect your data from various threats.
Take control of your data and protect your privacy now. If you have any questions or need further assistance, feel free to leave a comment below or share this article with others who might benefit.

by Brian Thompson | May 8, 2024 | Identity Theft
Identity theft is a bit scary—Compromised Bank Account Identity Theft is really disturbing. Think of how violating that crime is when it comes to invading your bank account. Time is of the essence to secure your money and, of course, any further risk to your identity. This guide is going to walk you through everything you need to know to do so.
Ways to Recognize If a Thief Has Your Bank Account Account:
Signs of your bank account being hacked, you can easily detect. Quickly act on what you detect, the earlier the better.
- Unexplained Transactions: Always review your bank statement for any transaction not made by you. That’s a clear indication of possible unauthorized access.
- Changes in Account Information: Any changes that are made to your personal information on the bank’s records not made by you should raise concern.
- Locked Out of Account: If you are suddenly locked out of your online banking account, it might be because someone else has gained access.
- Unfamiliar Charges on Credit Reports: Regularly review your credit reports for unfamiliar inquiries or accounts.
- Missing Mail: Missing bank statements could suggest that an identity thief has changed your address.
- Alerts from Your Bank: Pay attention to any alerts from your bank regarding suspicious activities.
- Declined Transactions: If your card is unexpectedly declined, it could be an indicator of fraudulent activity or that the bank has locked your account.
Immediate Steps to Take After Discovering Fraud
Contact your bank
- Contact Your Bank Immediately: As soon as you notice any suspicious activity, contact your bank’s fraud department. This is critical to prevent further unauthorized transactions.
- Secure Online Accounts: Change the passwords and PINs for all affected accounts, including your online banking access. Choose strong, unique passwords for each account to enhance security.
Engage with Credit Bureaus
- Place Fraud Alerts: Contact one of the three major credit bureaus—Equifax, Experian, or TransUnion to place a fraud alert on your credit reports, making it more difficult for identity thieves to open new accounts in your name.
- Consider a Credit Freeze: A credit freeze prevents new creditors from accessing your credit report, which stops new account openings. Visit AnnualCreditReport.com to learn how to apply for a freeze.
Report the Incident
- Federal Trade Commission (FTC): File a report with the FTC at IdentityTheft.gov. This site also provides a personalized recovery plan.
- Local Law Enforcement: Report to local police if significant financial loss is involved or if you possess information about the identity thief.
Prevention: Safeguarding Your Information
- Educate Yourself and Family: Stay informed about common tactics employed by identity thieves and educate your family on protecting personal information. Navigating the Digital Labyrinth: Safeguarding Your Identity in a Technology-Driven World
- Secure Personal Documents: Keep sensitive documents in a secure location and dispose of them properly when no longer needed.
While the immediate aftermath of discovering your bank account has been compromised is stressful, taking structured, informed steps can greatly mitigate the damage. By following the outlined procedures, you can not only address the current fraud but also enhance your defenses against future threats. For more detailed steps and assistance, visiting websites such as the FTC’s IdentityTheft.gov can provide tailored recovery plans based on your specific situation.
Articles related to Compromised Bank Account Identity Theft:






