
by Brian Thompson | Jul 23, 2024 | Employee Benefits, Identity Theft
Understanding the Problem with Identity Theft Protection Services
The Prevalence of Bundled Services
Identity theft protection services are often offered as part of a package with other products. This bundling creates a widespread misconception that all identity theft protection services are similar. Consumers and partners frequently think, “It’s offered everywhere already, so why choose a standalone service?” It is important to understand where those fall short and what makes a superior identity theft protection program.
Misconceptions about Standalone Services
The reality is that bundled services typically offer limited protection. They may include basic monitoring or reimbursement for financial losses but leave significant gaps in coverage. These gaps expose individuals to various risks that are not addressed by partial services.
Common Misconceptions about Bundled Identity Theft Protection
Limited Protection of Bundled Services
Bundled identity theft protection services often provide minimal coverage. This might include basic alerts or financial reimbursements, which do not fully address the complexities of identity theft.
Risks of Partial Coverage
Partial coverage means that many aspects of identity theft are left unprotected. Individuals might face risks related to medical identity theft, tax fraud, and other areas that require comprehensive monitoring and protection.
Our Comprehensive Solution for Identity Theft Protection
End-to-End Recovery Service
Expert Recovery Advocates
Our end-to-end recovery service is a cornerstone of our protection plan. Imagine having an expert recovery advocate who handles all necessary actions on your behalf, from detecting issues to restoring your pre-theft status. This comprehensive service ensures you don’t have to navigate the complexities of identity restoration alone.
Simplifying the Restoration Process
Our expert recovery advocates take on the burden of restoring your identity, allowing you to focus on your life. They handle everything from contacting creditors to filing necessary paperwork, making the process as smooth and stress-free as possible.
All-Around Protection
Comprehensive Coverage
Our identity theft protection service is like a puzzle with all pieces perfectly aligned. We provide comprehensive protection that covers every angle, ensuring your identity is safeguarded from all potential threats.
Safeguarding Against All Potential Threats
We protect against a wide range of threats, including financial, medical, and legal identity theft. Our service ensures that no matter where the threat comes from, your identity is secure.
Proactive Monitoring
Advanced Monitoring Systems
Think of our proactive monitoring as having a dedicated team of detectives constantly watching over your personal information. Our advanced monitoring system detects suspicious activities early, preventing issues before they escalate.
Early Detection of Suspicious Activities
By catching suspicious activities early, we can prevent identity theft before it happens. This proactive approach saves you from the stress and potential financial loss associated with identity theft.
Robust Safety Net Provided by a Superior Identity Theft Protection Program
Beyond Financial Reimbursement
While other plans might offer some financial reimbursement, our protection extends beyond just money. We safeguard your identity, credit, and even legal aspects, offering a full safety net that catches you no matter what.
Protecting Identity, Credit, and Legal Aspects
Our comprehensive protection includes monitoring and safeguarding your credit reports, legal documents, and personal information. This robust safety net ensures that all aspects of your identity are covered.
Personalized Assistance
Tailored Recovery Plans
In the event of identity theft, our recovery advocates are there to guide you through the entire process. They create personalized recovery plans tailored to your situation, ensuring a smooth and efficient restoration of your identity.
Guidance Through the Recovery Process
Our advocates are with you every step of the way, providing the support and guidance you need to restore your identity quickly and effectively.
Proven Track Record
Success Stories and Testimonials
Our service has successfully protected numerous clients, with testimonials highlighting our exceptional support and effective recovery. We’ve helped many individuals and families navigate identity theft crises, demonstrating our expertise and reliability.
Demonstrating Expertise and Reliability
Our proven track record showcases our commitment to protecting your identity. Our clients’ success stories and positive feedback are a testament to our high level of service and effectiveness.
Addressing Redundancies in Identity Theft Protection
Integrating Various Protective Measures
Unlike basic or bundled services that only provide partial coverage, our plan offers an all-in-one solution. By integrating various protective measures into a single comprehensive package, we eliminate the gaps left by other services.
Eliminating Gaps with a Unified Approach
This unified approach ensures you receive the highest level of protection without needing multiple subscriptions or relying on fragmented services. Our all-in-one package provides a seamless and comprehensive solution.
Customer Testimonials
Exceptional Customer Support
Check out our exceptional customer support and performance metrics, which speak volumes about our effectiveness and customer satisfaction. Our clients consistently praise our prompt and professional assistance.
Performance Metrics and Satisfaction
Our performance metrics highlight our success in preventing and resolving identity theft cases. Customer satisfaction is our top priority, and our results reflect our commitment to excellence.
Conclusion
Unparalleled Defense with Comprehensive Protection
While identity theft protection might seem ubiquitous, our comprehensive, all-in-one package provides unparalleled defense. With our service, you have a dedicated superhero team working tirelessly to keep you safe.
True Peace of Mind with Our Service
Don’t settle for incomplete protection—choose a service that offers true peace of mind. Our comprehensive identity theft protection ensures that all aspects of your identity are safeguarded, providing you with confidence and security.
Articles related to superior identity theft protection:

by Brian Thompson | Jun 26, 2024 | Employee Benefits, Identity Theft
Identity theft is a serious crime that can devastate your finances and your life. When someone steals your personal information, they can use it to open new accounts in your name, run up debts, and damage your credit score. Here we will discuss How to Protect Your Credit from Identity Theft.
A low credit score makes it difficult to get approved for loans, credit cards, and other forms of credit. It can also make borrowing money more expensive since you will likely have to pay higher interest rates. A low credit score also makes it difficult to rent an apartment, get a job, or even get insurance.
How Identity Theft Can Ruin Your Credit Score
Identity thieves can damage your credit in various ways. Here are a few examples:
- Opening New Accounts: Thieves can open new accounts in your name and not make payments, leading to collections and even bankruptcy.
- Maxing Out Credit Cards: They can max out your existing credit cards, significantly damaging your credit score.
- Changing Addresses: They can change the address on your accounts so you don’t receive important billing information, leading to missed payments and further damage to your credit score.
- Filing for Bankruptcy: Thieves can file for bankruptcy in your name, which will stay on your credit report for up to 10 years, making it very difficult to get approved for credit.
The Impact of a Low Credit Score Due to Identity Theft
A low credit score can significantly impact your life. Here are a few examples:
- Loan Approval: You may not be able to get approved for a loan to buy a car or a home.
- Higher Interest Rates: You may have to pay higher interest rates on credit cards and loans.
- Difficulty Renting or Getting a Job: You may have difficulty renting an apartment or getting a job.
- Insurance Issues: You may have difficulty getting insurance.
- Job Promotions and Scholarships: You may be denied a job promotion or a scholarship.
The Emotional Impact of Identity Theft
Identity theft not only ruins your credit but also has a significant emotional impact on victims. Victims may experience feelings of anger, anxiety, stress, and depression. They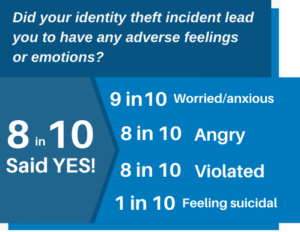 may also feel violated, betrayed, and helpless.
may also feel violated, betrayed, and helpless.
According to a study by the Identity Theft Resource Center, 70% of identity theft victims experience emotional distress. The study also found that victims are more likely to experience anxiety, depression, and post-traumatic stress disorder (PTSD) than people who have not been victims of identity theft.
If you are a victim of identity theft, it is important to seek help from a mental health professional. Talking to someone about what you are going through can help you cope with the emotional impact of the crime.
Steps to Recover from Identity Theft
If you find yourself a victim of identity theft, don’t panic. Here’s a systematic guide to help you regain control and mitigate any potential damage:
- Notify Your Insurance Provider: If you have identity theft insurance, inform them first for guidance and help.
- Alert Your Financial Institutions: Contact your bank and credit card issuers immediately to halt transactions and secure accounts.
- Contact Affected Companies: Reach out to companies where the theft occurred to inform their fraud department.
- Implement a Fraud Alert: Place a fraud alert on your credit with one of the three major credit bureaus.
- Review Your Credit Reports: Access your free credit reports from AnnualCreditReport.com and report any discrepancies.
- File a Report with the FTC: Visit identitytheft.gov to file a comprehensive identity theft report with the Federal Trade Commission (FTC).
- Report to Local Law Enforcement: Filing a police report provides an official record of the identity theft.
- Secure Your Online Presence: Change all online account passwords, consider using a password manager, and activate two-factor authentication.
- Replace Important Documents: Apply for replacements for stolen IDs like your driver’s license, passport, and Social Security card.
- Subscribe to Identity Theft Protection Services: Consider services like defend-id which monitor your financial and digital presence, providing alerts and insurance.
Steps to Take if You Suspect Identity Theft
If you suspect you’ve fallen victim to identity theft, take these essential steps promptly:
- Contact Your Financial Institutions: Reach out to your bank and credit card issuers immediately to freeze your accounts and halt unauthorized transactions.
- Report to Your Identity Theft Insurance Provider: Notify your provider right away for guidance and resources, including legal and financial assistance.
How Identity Theft Protection Services Help
Identity theft protection services, such as defend-id, play a crucial role in safeguarding your online and financial accounts from fraudulent activities. With defend-id’s advanced monitoring technology, subscribers receive alerts about potential fraud approximately four times faster than many competing services.
- Comprehensive Monitoring and Swift Alerts: defend-id provides detailed monitoring by keeping track of your personal and financial account activities. If something unusual is detected, defend-id promptly sends out an alert.
- Robust Insurance Coverage: defend-id offers significant financial protection with an insurance policy that can provide up to $1,000,000 in compensation for eligible losses caused by identity theft.
Protecting Yourself from Identity Theft and Fraud
Protecting yourself from identity theft and fraud is crucial. One effective way to safeguard your personal information is by using comprehensive services like defend-id, which offers robust monitoring and insurance coverage.
- Comprehensive Insurance Coverage: defend-id provides each plan member with a $1,000,000 insurance policy.
- Real-Time Monitoring and Alerts: defend-id monitors your financial and online accounts continuously, alerting you swiftly to any suspicious activity.
- Family Protection: defend-id’s Family Plan extends protection to up to five family members, including both adults and children.
- Trial Period: defend-id offers a 14-day free trial, allowing you to experience their service before committing.
Taking proactive steps by enrolling in a service like defend-id can provide peace of mind and significantly reduce the chances of suffering from identity theft and fraud.
Tactics Used by Identity Thieves
Identity thieves deploy various tactics to access personal data. They might steal your wallet, ID, or mail containing personal information, use a change-of-address scam, send phishing emails, texts, and calls, buy your data off the Dark Web, hack into your email, or intercept your data on an unsecured Wi-Fi network. Understanding these methods allows you to be more vigilant and take preventative measures to secure your personal and financial information.
Take Action Today
Identity theft is a serious crime, but you can protect yourself by taking necessary steps to safeguard your personal information and monitoring your credit reports regularly.
Resources:
- The Federal Trade Commission (FTC): 1-877-438-4338
- The Identity Theft Resource Center: 1-888-400-5530
- The National Association of Consumer Advocates: 1-800-644-7222
Don’t let identity theft ruin your credit and your life. Take action today to protect yourself!
Articles related to How to Protect Your Credit from Identity Theft:

by Brian Thompson | Jun 11, 2024 | Employee Benefits, Identity Theft
Identity Theft Protection as an Employee Benefit
Identity theft is a growing concern that can have devastating effects on individuals and businesses alike. As an employer, integrating identity theft protection as an employee benefit into your wellness program is not just a valuable benefit but a necessity. Below we explore why identity theft protection is crucial for employee wellness and how it can enhance your organization’s overall productivity and employee satisfaction.
Understanding Identity Theft
Identity theft occurs when someone uses another person’s personal information without permission, typically for financial gain. This can include stealing Social Security numbers, credit card information, or other sensitive data. According to the ITRC Impact Report, identity theft can lead to severe emotional and financial distress, making it difficult for victims to perform effectively at work.

The Toll of Identity Theft on Employees
The emotional and financial stress caused by identity theft can significantly impact employees’ well-being and job performance. A study found that 9 in 10 victims of identity theft experience negative emotions such as worry, anxiety, and anger. Moreover, 8 in 10 reported employment problems related to identity theft, including issues with coworkers and supervisors. When employees are distracted by personal crises, their productivity and morale can suffer, leading to higher turnover and lower engagement.
Why Employers Should Offer Identity Theft Protection
Employers have a unique opportunity to support their workforce by offering identity theft protection as an employee benefit as part of their wellness programs. By doing so, companies demonstrate a commitment to their employees’ overall well-being, which can enhance employee loyalty and employee satisfaction. Protecting employees’ identities helps them feel secure, enabling them to focus on their work without the distraction of dealing with identity theft issues.
Boosting Corporate Security Through Identity Protection Benefits
-
Social Media Protection
Implementing identity protection measures can play a critical role in safeguarding a company’s social media integrity. If an employee’s social media account is compromised, the repercussions can be significant. Unauthorized users may spread misinformation, engage in phishing attacks against the employee’s contacts, or even misuse the company’s brand to commit fraud. An effective identity protection program actively monitors for such irregular activities, promptly detects unauthorized access, and alerts the employees, thereby minimizing potential harm to the company.
-
Comprehensive Employee Education
Ongoing education is another cornerstone of strengthening corporate security via identity protection benefits. Employees serve as the first line of defense against security breaches. Regular training sessions should cover:
- The importance of robust password practices and account security measures.
- Awareness of the latest techniques used by cybercriminals and identity thieves.
- Updates on recent data breaches and security threats which could potentially impact the company.
This continual education helps in building a knowledgeable workforce that can recognize and mitigate threats effectively.
-
Protection of Sensitive Corporate Information
Identity protection benefits extend beyond personal data to include critical corporate assets like company credit cards, usernames, and passwords. For employees entrusted with accessing sensitive corporate information, safeguarding these assets is paramount. Identity protection services ensure that all components are closely monitored for any unauthorized access or transactions, further securing corporate financial and digital assets.
Through these measures, identity protection benefits not only secure individual employees but also fortify the organization’s overall cybersecurity framework.
Employee Engagement and Business Success
Employee engagement stands as a cornerstone of business success. Engaged employees drive productivity, foster a positive work environment, and contribute to the economic vitality of their organizations. Disengaged employees, on the other hand, can lead to substantial financial losses, with engagement research indicating potential costs to businesses in the billions annually.
One prevalent issue that can swiftly erode employee engagement is identity theft. This personal crisis demands considerable time and emotional energy to resolve, often diverting the employee’s focus and commitment away from work responsibilities. The process is fraught with uncertainty and stress, making it difficult for employees to maintain their usual levels of engagement at work. The resultant impact is not just on the employees’ productivity, but also on their morale and loyalty to the company, ultimately threatening overall business stability and success.
How Identity Protection Benefits Enhance Corporate Security
Employers have a unique opportunity to support their workforce by offering identity theft protection as an employee benefit as part of their wellness programs. By doing so, companies demonstrate a commitment to their employees’ overall well-being, which can enhance employee loyalty and employee satisfaction. Protecting employees’ identities helps them feel secure, enabling them to focus on their work without the distraction of dealing with identity theft issues.
Moreover, a robust identity protection program doesn’t just offer security after the fact; it provides comprehensive, preventative solutions aimed at mitigating risks before they occur. Such measures include educating employees on the importance of data security, protecting sensitive information like corporate credit cards, usernames, and passwords, and implementing tools to monitor and protect against breaches on social media platforms.
These proactive steps ensure that employees can dedicate their attention to their career growth, while the company benefits from maintaining a secure, engaged, and focused workforce. By integrating these elements into their corporate security strategy, companies can shield themselves and their employees from the profound impacts of identity theft, making the workplace a safer and more productive environment.Implementing Identity Theft Protection in Wellness Programs
Implementing Identity Theft Protection in Wellness Programs
To effectively integrate identity theft protection as an employee benefit into your wellness program, consider the following steps:
- Choose Comprehensive Services: Select a service that offers comprehensive monitoring and recovery solutions. defend-id, for example, provides fully managed recovery services, credit monitoring, dark web monitoring, expense reimbursement insurance, and many other features.
Expanding on the Details:
- Identity Theft Expense Reimbursement: Ensure that the service includes a robust identity theft expense reimbursement. It’s vital that the plan offers substantial coverage to handle the potential expenses arising from fraud. For instance, a standard should be set at a minimum of $1 million in coverage. This coverage should be backed by a reputable insurance provider, such as AIG, guaranteeing that the funds are available for a breadth of costs including, but not limited to, an employee’s lost wages, legal fees, medical records request fees, CPA fees, childcare fees, and more.
- Enhanced Dark Web Monitoring: The identity protection plan should also feature a proactive dark web monitoring service. This means that employees should have the option to register sensitive documents, like driver’s licenses and credit cards, with the service provider. In the event that these registered documents are found on the dark web, the employee should be alerted immediately. Following the alert, the provider should actively collaborate with the employee to address and resolve the issue, ensuring minimal impact and swift action.
- Educate Employees: Raise awareness about the risks of identity theft and how to prevent it. Provide regular training sessions and resources to help employees understand the importance of protecting their personal information.
- Offer Flexible Plans: Provide flexible product and pricing structures to meet the diverse needs of your employees. Consider offering both individual and family plans to ensure all employees and their dependents are protected.
- Promote the Benefits: Communicate the advantages of identity theft protection to your employees. Highlight how these services can save time, reduce stress, and provide peace of mind.
Success Stories and Testimonials

Real-life examples and testimonials can be powerful tools to illustrate the benefits of identity theft protection. One employee shared their experience with defend-id, stating, “My Recovery Advocate was a great help. This was my first experience with ID theft. He helped me through all of it, every step because I was lost. I felt the entire process was easy and a ton of weight is now off my shoulders”. Such stories emphasize the real impact these services can have on employees’ lives.
Check out a case study of a mortgage company in CT here: Case Study
Final thoughts
Identity theft protection as an employee benefit is an essential component of a comprehensive employee wellness program. By offering these services, employers can help mitigate the emotional and financial stress caused by identity theft, ultimately enhancing workplace productivity and employee satisfaction. Investing in identity theft protection is not just a benefit; it is a proactive step toward fostering a secure and focused workforce.
Encourage your organization to prioritize identity theft protection as an employee benefit today. For more information on integrating these services into your wellness program, visit defend-id.
defend-id.
Articles related to identity theft protection employee benefit:

by Brian Thompson | Apr 24, 2024 | Breach, Employee Benefits, Identity Theft
The need for robust identity theft protection is critical as businesses face growing cyber threats.. Annually, millions are affected by identity fraud, with businesses bearing a substantial brunt—both in terms of compromised employee data and overall organizational integrity. Beyond a mere perk, identity theft protection is essential for maintaining productivity, safeguarding sensitive information, and attracting and retaining top talent.
Benefits of Identity Theft Protection for Businesses:
- Reduced Employee Disengagement: Studies show resolving identity theft issues can take 100-200 hours, leading to decreased focus and productivity. Identity theft protection services help mitigate these disruptions, allowing employees to concentrate on their work without the added stress of personal security breaches.
- Enhanced Corporate Security: Employee identity theft can lead to broader data breaches affecting company data and client trust. Offering identity theft protection helps reduce the risk of such breaches, strengthening your cybersecurity posture and shielding both employee and corporate data from cyber threats.
- Ongoing Security Education: Identity theft protection programs include education on the latest security practices and vulnerabilities. This proactive approach empowers employees to safeguard their personal and professional data, contributing to overall corporate security.
- Safeguarding Corporate Information: Identity theft protection services monitor and alert employees about suspicious activities linked to corporate assets like credit cards and login credentials. This monitoring helps prevent unauthorized access, protecting sensitive data from cybercriminals.
- Attracting and Retaining Top Talent: Offering identity theft protection as a benefit can significantly enhance your company’s appeal to prospective employees, particularly millennials, who are projected to make up 75% of the workforce by 2025. Modern benefits like these demonstrate a company’s commitment to employee well-being, making them attractive places to work.
Building Trust and Loyalty:
A company’s reputation is bolstered by offering identity theft protection. This benefit showcases that a company cares about its employees’ safety and personal data, which can improve trust and loyalty among current employees and attract new ones.
Beyond Individual Protection:
Identity theft protection services go beyond individual protection, enhancing overall corporate security. They provide tools that monitor and report potential security breaches, not just internally but also on external platforms like social media and the dark web, where stolen data can be found.
Early Detection and Fast Resolution:
Identity theft protection services specialize in the early detection of identity threats, critical for minimizing damage. They monitor various channels to quickly identify and address potential threats before they escalate into serious issues.
Comprehensive Protection Features:
Many identity theft protection plans offer features beyond basic monitoring, including:
- Credit Lock: to restrict access to your credit report and prevent unauthorized accounts from being opened.
- Social Media Monitoring: to track your social media profiles for suspicious activity.
- Password Management Tools: to securely store and manage strong passwords.
These features provide layered security, helping employees protect their digital footprints from potential cyber threats.
Financial Protection and Support:
Financial recovery from identity theft can be daunting. Most identity theft protection services include insurance to cover financial repercussions like legal fees and lost wages, providing essential support during recovery. They also offer mitigation services like dark web monitoring and many others. The most important factor is their ability to help employees recover when fraud does occur!
Investing in identity theft protection is more than a security measure. It is a strategic business decision that enhances your corporate image, increases data privacy, and ensures a resilient organizational culture.
Ready to fortify your business against identity theft? Download your free Defend-ID Identity Theft Response Plan now and take a pivotal step toward comprehensive business security and employee satisfaction!
Articles related to identity theft protection for businesses:
by Brian Thompson | Apr 18, 2024 | Employee Benefits, Identity Theft
Incognito mode, or private browsing, is a feature found in most modern web browsers like Google Chrome, Firefox, and Safari. It promises a level of privacy and secrecy by not saving your browsing history, cookies, site data, or information entered in forms. Understanding the nuances of incognito mode misconceptions is crucial for using this feature effectively.
What Incognito Mode Actually Does
- No Local Trace: When you use incognito mode, your browser does not save your browsing history or cookies after you close the window. This means anyone else using the same device won’t be able to see what you were doing.
- Session Isolation: Each incognito session is isolated from the other. If you sign into a website in incognito mode, your login state won’t carry over to the normal browsing windows. This is particularly useful for accessing multiple accounts simultaneously.
- Some Forms of Shield Against Tracking: While not foolproof, using incognito mode can reduce tracking from some cookies, as they are deleted once you close the window.
Popular Myths vs. Reality
- Myth: Incognito mode makes you invisible online.
Reality: Incognito mode does not hide your IP address or encrypt your traffic. Your internet service provider (ISP), websites you visit, and network administrators can still see your activity.
- Myth: It is a tool for anonymous browsing.
Reality: Incognito mode does not offer anonymity. For true anonymity, one would need tools like VPNs or the Tor browser.
- Myth: You are safe from malware and viruses in incognito mode.
Reality: Incognito mode does not protect you from viruses or malware. It only prevents your browsing history and cookies from being saved.
The Privacy You Get (And Don’t Get) With Incognito Mode
While incognito mode offers a basic level of privacy by not saving your history or cookies, it does not protect you from all types of surveillance. Employers, ISPs, and websites can still track your visits and interactions through various means like your IP address.
Better Alternatives for Serious Online Privacy
For those who are serious about maintaining privacy online, consider the following:
- VPNs (Virtual Private Networks): A VPN encrypts your internet connection and hides your IP address, providing a much higher level of privacy than incognito mode.
- Tor Browser: For maximum anonymity, the Tor browser routes your traffic through multiple nodes, making it extremely difficult to track.
- Secure Browsers: Browsers like Brave are built with privacy in mind, offering various features to block trackers and ads by default.
Conclusion: Is Incognito Mode Enough?
While incognito mode is helpful for keeping your local browsing private, it’s not a one-stop solution for all privacy needs. Knowing its limitations helps set realistic expectations about what privacy you can actually achieve while online.
Remember, no tool is perfect, but understanding the tools you use can make a significant difference in your digital life. So, next time you go incognito, remember that it’s just one piece of the privacy puzzle.
FAQs about Incognito Mode:
- Does incognito mode save any data?
No, it does not save your browsing history, cookies, site data, or information entered in forms on your device after you close the session.
- Can my employer see what I browse in incognito mode if I’m on a company network?
Yes, your employer can still track your browsing activity if you are connected to the company’s network.
- Is incognito mode the same in all browsers?
While the core functionality is the same, some browsers might offer slight variations in how they handle cookies and data during incognito sessions.
If you’re ever in doubt about what incognito mode can do for you, just remember it’s great for keeping things off your local machine but not much else when it comes to the wider web. For anything beyond that, you’ll need to beef up your privacy tools arsenal.
Article related to incognito mode misconceptions:
by Brian Thompson | Feb 21, 2024 | Employee Benefits, healthcare, Identity Theft
Guarding Employee Wellness: Why Identity Theft Protection is a Great Option for Business Owners and HR Leaders
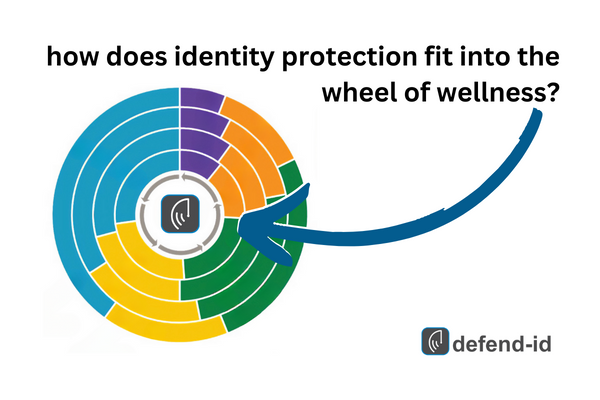
In today’s rapidly evolving work landscape, the separation between professional and personal life is becoming increasingly blurred, especially with the increase in remote working. In this newer working environment, employees crave benefits that cater not only to their physical health but also to their financial and emotional wellness. The LIMRA-EY 2023 Workforce Benefits Study brings to light this shift by introducing the Wheel of Wellness, encompassing five key dimensions of wellness: Physical, Mental, Financial, Societal, and Professional 1.
A novel yet pivotal benefit that aligns with multiple facets of the Wheel of Wellness is Identity Theft Protection. Here’s how it dovetails with the five key dimensions:

- Financial Wellness:
Identity theft is no minor issue; it’s a financial slap in the face. The average loss per person is a staggering $3,500. In the United States, total identity theft losses amount to $10.2 billion 2. Offering identity theft protection is a proactive step towards safeguarding an employee’s financial wellness, and ensuring economic resilience, which is a core part of the financial dimension of wellness.
- Mental Wellness:
The ripple effects of identity theft extend beyond financial loss to mental turmoil. The peace of mind from knowing there’s a safety net can be invaluable in promoting mental wellness among employees 3 4. According to the ITRC study, 75% of respondents showed severe distress stemming from the misuse of their information, leading many to seek professional help to navigate their identity theft ordeal—whether it entailed consulting a doctor for physical symptoms or engaging in mental health counseling.
- Professional Wellness:
The time and focus consumed in resolving identity theft issues can impede professional performance. By offering identity theft protection, employers show a proactive stance in supporting their employees’ career development and performance, aligning with the Professional dimension of wellness.
- Societal and Physical Wellness:
While these dimensions may not seem to have a direct link to identity theft protection, a comprehensive approach to employee wellness fosters a conducive environment for societal engagements and physical wellness.
The Stark Reality
A substantial number of Americans are living on the financial edge. Recent surveys reveal that a third of Americans have $100 or less in their savings account going into 2023 6, and many cannot cover a $1,000 emergency 7. This precarious financial situation underscores the necessity of identity theft protection as a part of employee benefits.
Incorporating Identity Theft Protection acts as a barrier against financial distress. Additionally, it contributes to the mental and professional well-being of employees. This benefit’s ripple effect resonates through the Wheel of Wellness. It creates a holistic protective shield around employees. For business owners or HR leaders, including identity theft protection in your benefits is a forward-thinking step. It nurtures a well-rounded, satisfied, and productive workforce. In a fiercely competitive talent market, offering this comprehensive benefit can bolster your employer brand. It makes you a preferred choice among top talents.
As the terrain of work continues to morph, adapting your benefits package to include identity theft protection is not merely about staying current; it’s about fostering a culture of comprehensive wellness and showing a genuine interest in the multifaceted well-being of your workforce.
Ready to arm your employees against identity theft and enhance their overall wellness? Click here to request a comprehensive Identity Theft Protection Employer Response Plan. Your employees will thank you for it!
Related:


 may also feel violated, betrayed, and helpless.
may also feel violated, betrayed, and helpless.





