
by Brian Thompson | Feb 19, 2025 | healthcare, Identity Theft
Protecting your personal health information is more important than ever. Medical identity theft—when someone uses your health data for fraudulent purposes—can lead to devastating financial losses, compromised care, and long-lasting credit issues. In this article, we explore what medical identity theft is, outline best practices for safeguarding your information, and provide actionable steps you can take if you suspect your data has been compromised.
I. Understanding Medical Identity Theft
What It Is and Its Impact
Medical identity theft occurs when a criminal uses another person’s health information (like your name, Social Security number, or health insurance details) to obtain medical care, submit fraudulent claims, or receive unauthorized prescriptions. Unlike traditional identity theft, this type of fraud affects your finances and ability to access necessary healthcare services. Victims may face billing errors, treatment delays, and damage to their credit scores.
Common Methods of Theft
- Data Breaches: Cyberattacks on hospitals and healthcare providers have led to massive leaks of patient data.
Link: FTC Data Breach Notifications
- Phishing Attacks: Fraudsters send deceptive emails or texts posing as trusted healthcare institutions to trick you into revealing sensitive information.
- Insider Threats: Unsecured patient records and unauthorized access by staff can also result in stolen data.
II. Best Practices for Protecting Your Medical Identity
Secure Your Health Records and Personal Information
- Strong Passwords & Multi-Factor Authentication: Use complex, unique passwords and enable multi-factor authentication for healthcare portals. This extra layer of security ensures that even if your password is compromised, unauthorized access remains unlikely.
- Digital Health Cards & Encrypted Portals: Whenever possible, opt for digital health insurance cards and secure, encrypted patient portals. Many healthcare providers now offer mobile apps for safe access to your records.
Monitor Your Medical and Financial Statements
- Regular Reviews: Make it a habit to review your Explanation of Benefits (EOB) statements and medical bills for any discrepancies or charges you don’t recognize.
- Account Alerts: Set up notifications on your bank and credit accounts to detect suspicious activities early.
Utilize Identity Theft Protection Services
- Credit Freezes & Fraud Alerts: Consider placing a credit freeze with major bureaus (Experian, Equifax, TransUnion) to prevent new fraudulent accounts.
- Professional Monitoring: Identity protection services can continuously monitor your data and alert you if your information is compromised.
Follow HIPAA and Regulatory Guidelines
- Know Your Rights: Familiarize yourself with HIPAA and state-specific regulations regarding medical data. Ask your healthcare provider about their data security measures.
- Secure Data Practices: Ensure that any provider you work with complies with federal and state guidelines.
Educate Yourself and Your Family
- Stay Informed: Cybersecurity threats are ever-evolving. Regularly update yourself on the latest scams and breaches.
- Family Awareness: Encourage your family—especially vulnerable members—to adopt secure practices, like using strong passwords and being cautious about sharing personal data.
III. Tools and Technologies to Combat Medical Identity Theft
Biometric Authentication & Digital Health Records
Modern healthcare providers increasingly use biometrics (such as iris scans and facial recognition) to verify patient identities. These technologies help ensure that only you can access your medical records.
Data Encryption and Secure Storage Solutions
Encryption protects your data in transit and at rest. Secure cloud storage and encrypted electronic health record (EHR) systems significantly reduce the risk of unauthorized access.
Trusted Identity Management Software
Specialized identity management tools help verify identities, monitor for suspicious activity, and provide immediate alerts if unauthorized access is detected.
IV. What to Do If You Suspect Medical Identity Theft
Immediate Steps to Take
- Document Suspicious Activity: Keep detailed records of any unauthorized charges or discrepancies in your medical or financial statements.
- Contact Your Healthcare Provider: Inform your provider about any irregularities in your records so they can verify and secure your information.
Reporting and Recovery
- Report to the FTC: File a report at IdentityTheft.gov to initiate a formal recovery plan.
- Notify Local Law Enforcement: A police report serves as crucial documentation if you need to dispute fraudulent charges.
- Seek Professional Help: Consider using professional identity recovery services for assistance in restoring your information and credit.
FAQ
Q: What is medical identity theft?
A: Medical identity theft occurs when someone uses your personal health information to commit fraud—such as obtaining unauthorized medical services or filing fraudulent insurance claims.
Q: How can I secure my health records?
A: Use strong, unique passwords, enable multi-factor authentication, opt for digital health cards and encrypted portals, and regularly review your medical statements for any discrepancies.
Q: What should I do if I suspect medical identity theft?
A: Document any suspicious activity, contact your healthcare provider, report the issue to the FTC via IdentityTheft.gov, and file a police report. Professional recovery services can also help restore your identity.
Conclusion
Medical identity theft is a serious threat with far-reaching consequences—not just financial, but also in terms of your access to vital healthcare. By securing your digital health records, monitoring your accounts closely, and staying informed about the latest cybersecurity threats, you can significantly reduce your risk. Take proactive steps today: update your passwords, educate your family, and use trusted identity protection services.
Download our free checklist for safeguarding your health data, subscribe to our newsletter for ongoing tips, and share this article with friends and family to help protect their identities in 2025 and beyond.

by Brian Thompson | Feb 12, 2025 | Identity Theft
Securing your personal data with reliable identity theft protection strategies is essential for financial and personal security. Many consumers are actively looking for answers on how to prevent identity fraud, what measures to take when suspicious activity occurs, and how to recover quickly if their identity is compromised. Below, we present a detailed FAQ addressing the most frequently asked questions we’ve been receiving recently.
1. How Can I Tell If My Identity Has Been Stolen?
Effective identity theft protection begins with recognizing the warning signs. Look for:
- Unexpected Accounts: Check your credit report for accounts you did not open.
- Unusual Inquiries: Monitor your credit for unauthorized inquiries.
- Missing Mail: A sudden absence of bills or statements may indicate a change of address by a fraudster.
- Unexplained Charges: Review bank and credit card statements for unfamiliar transactions.
Regular monitoring of your credit report—whether annually or quarterly—helps you catch any early signs of identity fraud.
2. What Is a Fraud Alert and How Do I Place One?
A fraud alert is a critical tool in identity theft protection. It signals to creditors that extra verification is needed before opening new credit in your name. Here’s how to place one:
- Contact a Credit Bureau: Call any of the major bureaus (Equifax, Experian, or TransUnion) to request a fraud alert.
- Automatic Notification: The bureau will inform the other agencies on your behalf.
- Alert Duration: A standard fraud alert lasts 90 days; extended alerts are available for confirmed victims.
This extra verification step helps prevent unauthorized credit applications.
3. How Do I Freeze My Credit, and Why Is It Important?
A credit freeze (also known as a security freeze) is a highly effective measure for identity theft protection. It prevents new creditors from accessing your credit report, thus stopping identity thieves from opening accounts in your name. Key points include:
- How to Initiate: Contact Equifax, Experian, and TransUnion to freeze your credit. This service is free for U.S. residents.
- Temporary Lift: If you plan to apply for new credit, you must temporarily lift the freeze.
- Benefits: Keeping your credit report inaccessible reduces the risk of new account fraud significantly.
Implementing a credit freeze is a proactive step that adds substantial security to your financial identity.
4. What Steps Can I Take to Protect My Identity Both Online and Offline?
Combining both digital and physical strategies is essential for comprehensive identity theft protection:
- Online Protection:
- Use strong, unique passwords for every account.
- Enable multi-factor authentication (MFA) on all accounts.
- Stay alert for phishing emails and texts; avoid clicking on suspicious links.
- Keep devices and software updated with the latest security patches.
- Offline Protection:
- Shred any documents containing sensitive personal information.
- Secure your mail with a locked mailbox.
- Regularly review bank and credit card statements for unauthorized transactions.
These practices together form a robust defense against identity theft.
5. What Should I Do If I Discover I’m a Victim of Identity Theft?
If you suspect your identity has been compromised, act swiftly:
- File a Report: Immediately contact your local law enforcement to file a police report.
- Notify Financial Institutions: Inform your bank and credit card companies to halt further unauthorized transactions.
- Place Fraud Alerts or Freeze Credit: Contact the major credit bureaus to request a fraud alert or initiate a credit freeze.
- Use Recovery Resources: Visit IdentityTheft.gov for a detailed recovery plan and further guidance.
- Document Everything: Keep records of all communications and actions taken for evidence and follow-up.
Quick and decisive action can minimize the financial and personal damage from identity theft.
6. How Do Scammers Steal My Personal Information?
Scammers employ a variety of methods to bypass identity theft protection measures:
- Phishing Attacks: Fraudulent emails or texts trick you into sharing sensitive information.
- Data Breaches: Hackers may infiltrate companies to steal large amounts of personal data.
- Physical Theft: Thieves may steal your mail, wallet, or electronic devices containing personal identifiers.
- Social Engineering: Tactics that exploit human psychology to extract personal details.
Understanding these methods is crucial to adopting effective measures to secure your personal information.
7. What’s the Difference Between Identity Theft and Financial Fraud?
While often confused, identity theft and financial fraud differ in scope:
- Financial Fraud: Involves unauthorized use of your existing accounts (such as fraudulent credit card charges).
- Identity Theft: Involves the broader misuse of your personal data—for example, using your Social Security number to open new accounts or file fraudulent tax returns.
The consequences of identity theft are typically more extensive and long-lasting, which is why comprehensive identity theft protection measures are vital.
Conclusion
Implementing robust identity theft protection strategies is crucial for securing your personal information and financial well-being. By recognizing the warning signs, using fraud alerts and credit freezes, and combining both online and offline security measures, you can significantly reduce your risk of identity fraud.
For further guidance, explore related topics on our website such as our Credit Monitoring Guide and our Fraud Prevention Tips. We also invite you to subscribe to our newsletter for the latest updates on protecting your identity.
Stay proactive—subscribe to our newsletter and follow us on social media for continuous updates on identity theft protection tips, news, and best practices.
Identity theft protection-related articles:

by Brian Thompson | Feb 5, 2025 | Breach, Identity Theft, Scams
Artificial intelligence (AI) is changing how companies and people protect themselves from fraud. AI helps find and stop fraud while also giving criminals new ways to trick people. This article explains both sides of AI in fraud prevention in clear, simple language.
How AI Helps Criminals Commit Fraud
Deepfakes and Fake Identities
AI can create deepfakes, which are very realistic videos, audio clips, and images that look real but are fake. Criminals use deepfakes to create fake identities.
Example: A fake video of a company leader might trick a business into sending money to a criminal.
Here is a fun example (note – this was done 3 years ago, consider how much better and accessible AI is today!): Tobey Maguire instead of Tom Holland in Spider-Man
AI-Driven Scams
Criminals use AI to create smart scams. They design phishing emails and phone calls that sound very real. These scams make it easier to steal money or personal information.
Important Numbers
- The FBI’s Internet Crime Complaint Center (IC3) said AI-assisted phishing scams increased by 35% in 2022. (Source: FBI IC3, 2022 – visit ic3.gov for more information.)
- Cybersecurity Ventures (2023) predicts that losses from AI-enhanced fraud could reach $20 billion by 2025.
How AI Helps Stop Fraud
Smart Computer Programs
Machine learning fraud detection systems use AI to study large amounts of data. They look for patterns that seem odd and can quickly spot fraud. This helps stop fraud before it causes big problems.
Watching for Strange Activity
AI tools can monitor transactions and user actions in real-time. They check every move and alert someone if something seems wrong. This fast response helps prevent more fraud.
Success Stories
- A 2021 report by IBM Security found that companies using AI fraud detection systems reduced fraud losses by 25% in one year. (Source: IBM Security, 2021 – visit ibm.com/security for details.)
- Some big banks have seen a 30% drop in fraud after using AI systems. (Source: McKinsey & Company, 2022 – learn more at mckinsey.com.)
Working With Other Technologies
Using AI with other tools like blockchain and behavior analysis makes fraud prevention even stronger. This mix helps companies protect customers and build trust.
The Ongoing Battle: Fraudsters vs. Fraud Detectors
Fighting Back with AI
As AI improves, criminals also get better at using it. They find new ways to beat security systems. This means the people who build AI tools must keep updating them to stop these tricks.
More Money for AI Research
Companies and governments are spending more money to improve AI for security. Working together, they hope to stay ahead of criminals who use AI for fraud.
Ethics, Laws, and Rules in AI Fraud Prevention
Balancing Safety and Privacy
While AI in fraud prevention has many benefits, it also raises questions about privacy. Companies must use AI carefully so that it does not invade people’s personal lives. Using AI safely and respectfully is very important.
Current Rules and Future Changes
Laws like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States help protect personal data. As AI changes, lawmakers need to update these rules to keep up with new challenges.
The Future of AI in Fraud Prevention
What to Expect Next
The future will bring even more advanced AI tools. Both criminals and defenders will continue to improve their techniques. New tools and better ways to watch for fraud will be needed.
Tips for Companies
- Invest in Advanced AI Tools: Use the latest AI systems to spot fraud quickly.
- Keep Watching All the Time: Real-time monitoring of transactions is very important.
- Train Employees: Teaching staff about new fraud scams can help protect the company.
Tips for Lawmakers
- Create Flexible Rules: Laws should be updated often to keep up with new technology.
- Support Cybersecurity Research: More funding is needed to develop new tools to fight AI-driven fraud.
Frequently Asked Questions (FAQ)
Q: What is AI in fraud prevention?
A: AI in fraud prevention uses artificial intelligence to detect and stop fraud. It can also be misused by criminals to create smarter scams.
Q: How does AI help stop fraud?
A: AI helps by monitoring transactions in real-time, spotting unusual patterns, and alerting companies when something seems wrong.
Q: Can criminals use AI to commit fraud?
A: Yes, criminals can use AI to create deepfakes, fake identities, and smart scams that make it harder to tell real messages from fake ones.
Conclusion
AI in fraud prevention shows both good and bad sides. On one side, AI gives companies strong tools to detect and stop fraud. On the other, criminals use AI to create smarter scams. To keep everyone safe, companies, tech experts, and lawmakers must work together. By using AI responsibly, we can build stronger defenses and a safer future.
References
- FBI Internet Crime Complaint Center (IC3), 2022 – ic3.gov
- Cybersecurity Ventures, 2023 – Annual Cybercrime Report, 2023
- IBM Security, 2021 – ibm.com/security
- McKinsey & Company, 2022 – mckinsey.com
Links to Related Topics:
Share this article on Twitter and Facebook to help others learn how AI in fraud prevention works.

by Brian Thompson | Jan 29, 2025 | Breach, General, Identity Theft
The 2024 Data Breach Trends Report from the Identity Theft Resource Center (ITRC) reveals a troubling reality—despite ongoing cybersecurity efforts, data breaches remain at near-record levels, with over 1.7 billion victim notices issued, a staggering 312% increase from the previous year. According to James E. Lee, President of the ITRC, “Stolen and compromised data is so ubiquitous that the number of people and businesses who have not been impacted by a data breach is now dwarfed by the number of victims who have—by a factor of five”. This surge, driven largely by six massive mega-breaches, underscores the urgent need for stronger data security measures, better breach disclosure policies, and widespread adoption of advanced authentication solutions like passkeys.
This report highlights the key trends shaping cybersecurity in 2024, including the industries most affected, the growing impact of AI in cyberattacks, and strategies to enhance data protection for businesses and individuals alike.
Key Findings: The State of Data Breaches in 2024
1. Data Breaches in 2024 Remain at Record Highs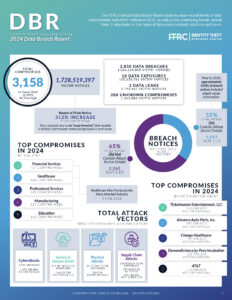
- Total breaches reported: 3,158 (only 44 short of 2023’s record).
- Victim notices issued: Over 1.7 billion notices, representing a 312% year-over-year increase.
- Six major mega-breaches accounted for 85% of all victim notices.
- Despite new privacy laws, data breaches continue to rise.
The rise in victim notices suggests that while breach disclosures may have increased, security improvements remain inadequate.
2. Financial Sector Overtakes Healthcare as the Most Targeted Industry
For the first time since 2018, financial services surpassed healthcare as the most breached industry.
Top Five Breached Industries in 2024
- Financial Services – 737 breaches
- Healthcare – 536 breaches
- Professional Services – 345 breaches
- Manufacturing – 317 breaches
- Education – 162 breaches
While commercial banks and insurance companies saw an increase in attacks, healthcare remained a major target, with breaches exposing sensitive medical and insurance records.
3. Cyberattack Trends and Emerging Threats
Cyberattacks remained the leading cause of data breaches, with stolen credentials, phishing, and AI-driven scams being the most common attack methods.
Most Common Cyberattack Methods in 2024
- Phishing & Smishing Attacks – 455 incidents
- Ransomware – 188 reported cases
- Malware Attacks – 48 breaches
- Credential Stuffing – 29 breaches
Alarmingly, 65% of breach notices failed to disclose the attack method, raising concerns about transparency in cyberattack reporting.
Enhance Protection in 2025
1. Strengthen Authentication and Password Security
One of the most effective ways to prevent data breaches is to eliminate weak passwords and implement stronger authentication methods.
- Adopt Multi-Factor Authentication (MFA) and Passkeys
- Eliminate password reuse across accounts
- Enable biometric authentication for added security
According to the ITRC, many of the biggest breaches of 2024 could have been prevented if organizations had properly implemented MFA and passkeys.
2. Improve Cloud Security Measures
21 major breaches were linked to misconfigured cloud security settings, emphasizing the need for better cloud security controls.
Key Cloud Security Best Practices:
- Implement a Zero Trust security model
- Regularly audit cloud permissions
- Enable automated patching for vulnerabilities
3. AI’s Role in Cybersecurity: A Double-Edged Sword
While AI is helping attackers create more sophisticated cyber threats, it is also being used to enhance cybersecurity defenses.
How AI is Helping Cybersecurity:
- AI-driven monitoring tools detect anomalies faster
- Automated security patches prevent vulnerabilities
- Predictive risk analysis enhances cyber resilience
Organizations should invest in AI-powered cybersecurity solutions to stay ahead of cybercriminals.
Are Data Breach Disclosure Laws Failing?
Despite state and federal breach notification laws, breaches continue to rise, and disclosure remains inadequate.
Key Issues with Current Disclosure Laws:
- 70% of cyberattack-related breach notices lacked details on attack methods
- Publicly traded companies accounted for 76% of all victim notices, despite being only 7% of affected organizations
- Many breaches remain underreported or undisclosed due to regulatory loopholes
However, state privacy laws are beginning to take the lead. Twenty U.S. states have passed comprehensive privacy laws, with eight more taking effect in 2025.
Final Thoughts: The Future of Data Security
The 2024 Data Breach Trends Report highlights ongoing cybersecurity failures but also presents opportunities for stronger data protection.
Key Takeaways for 2024:
- Businesses must implement MFA and passkeys to prevent credential-based attacks.
- Cloud security misconfigurations remain a major vulnerability.
- AI is transforming cybersecurity—for both attackers and defenders.
- Data breach disclosure laws need improvement for greater transparency.
By adopting proactive cybersecurity measures, businesses and individuals can reduce their risk of data breaches and better protect sensitive information.
FAQs on 2024 Data Breach Trends
1. What were the biggest data breaches in 2024?
The largest data breaches included:
- Ticketmaster Entertainment – 560 million victims
- Advance Auto Parts – 380 million victims
- Change Healthcare – 190 million victims
- AT&T – 110 million victims
2. What industries were most affected by cyberattacks in 2024?
The financial services sector had the highest number of breaches, followed by healthcare, professional services, and manufacturing.
3. How can businesses prevent data breaches?
- Use Multi-Factor Authentication (MFA) and passkeys
- Train employees on phishing scams and social engineering
- Monitor and secure cloud environments
4. How is AI impacting cybersecurity?
AI is being used by both attackers and defenders. Cybercriminals leverage AI for phishing and automated attacks, while security teams use AI for threat detection and automated responses.
5. Are state data privacy laws more effective than federal laws?
Yes. Twenty U.S. states have passed strong privacy laws, and more are expected in 2025, filling the gap left by federal inaction.
Articles related to 2024 Data Breach Trends:

by Brian Thompson | Jan 22, 2025 | Identity Theft, Scams
Tax fraud will be a growing threat in 2025. Check out these strategies for protecting yourself from tax fraud, including early filing, recognizing scams, and securing your data.
Tax fraud has become a sophisticated and costly issue affecting millions every year. In 2024 alone, the IRS identified and stopped $2.1 billion in fraudulent tax returns. Protecting yourself in 2025 requires an informed approach to protecting personal and financial data.
Below, we’ll look at the types of tax fraud, warning signs, and actionable steps you can take to mitigate risks.
Understanding Tax Fraud
What Is Tax Fraud?
Tax fraud occurs when an individual or organization intentionally falsifies information on tax returns to evade taxes or steal refunds. This can include inflating deductions, underreporting income, or filing false returns using stolen identities.
How Tax Identity Theft Works
Tax identity theft is a common subset of tax fraud where criminals use stolen personal information, like Social Security numbers (SSNs), to file fraudulent tax returns. Victims often discover the fraud only when their legitimate returns are rejected.
Who Is at Risk?
While everyone is vulnerable, these groups are particularly targeted:
- Seniors, due to phone scams and phishing emails.
- Immigrants, unfamiliar with U.S. tax systems.
- Small businesses with minimal cybersecurity measures.
- Individuals affected by data breaches.
Warning Signs of Tax Fraud
Knowing the red flags can help you act quickly:
- Unexpected IRS Notices: Letters about unfiled returns or tax discrepancies.
- Rejected Tax Returns: Your return is denied because someone already filed using your SSN.
- Suspicious Refunds: Receiving refunds or payments you didn’t request.
- Credit Report Changes: Unexplained accounts or activities on your credit file.
How Tax Fraud Happens
Criminals use diverse tactics to perpetrate fraud:
- Phishing Emails and Calls: Fake IRS communications requesting personal details.
- Data Breaches: Hackers access and sell sensitive information online.
- Mail Theft: Stolen tax documents like W-2s and 1099s.
- Fake Tax Preparers: Fraudulent preparers filing false returns or stealing refunds.
Top Strategies for Protecting Yourself from Tax Fraud
1. File Taxes Early
Early filing is one of the most effective defenses against tax fraud. By submitting your return before fraudsters have a chance, you can secure your refund.
2. Safeguard Personal Information
Treat your sensitive data as priceless:
- Shred documents containing personal information.
- Store tax records securely, both physically and digitally.
- Never share your SSN unless absolutely necessary.
3. Use Secure Technology
Filing electronically? Take these precautions:
- File using secure, password-protected networks or a Virtual Private Network (VPN).
- Avoid public Wi-Fi.
- Ensure tax software uses robust encryption.
4. Vet Your Tax Preparer
Not all tax preparers are trustworthy.
- Verify credentials using the IRS Tax Preparer Directory.
- Avoid preparers who promise excessive refunds.
- Ensure they sign your return with a Preparer Tax Identification Number (PTIN).
5. Monitor Financial Accounts
Proactive monitoring can reveal fraud early:
- Regularly review bank and credit card statements.
- Check your credit report at least annually.
6. Be Wary of Scams
- The IRS will never contact you via email, social media, or phone.
- Scammers often demand payment via gift cards or wire transfers—legitimate authorities won’t.
- Validate any communication by contacting the IRS directly.
Steps to Take if You Become a Victim
1. Contact the IRS Immediately
- Call the IRS Identity Protection Specialized Unit at 800-908-4490.
- Submit Form 14039, Identity Theft Affidavit, to report fraud.
2. Notify Credit Bureaus
Place a fraud alert on your credit file with Equifax, Experian, and TransUnion.
3. File Complaints
- Report identity theft to the Federal Trade Commission at identitytheft.gov.
- File a police report for local documentation.
4. Secure Your Identity
Consider subscribing to identity theft protection services that offer monitoring, insurance, and recovery support.
Emerging Trends in Tax Fraud for 2025
- AI-Powered Phishing: Bad guys are using AI to craft highly convincing fake IRS emails and messages.
- Cryptocurrency Scams: Exploiting crypto earnings and losses for fraudulent returns.
- Unemployment Insurance Fraud: Criminals filing fake unemployment claims tied to tax filings.
Tips for Businesses
Businesses can also be targets of tax fraud. Here’s how to protect your organization:
- Implement robust cybersecurity measures, such as multi-factor authentication.
- Train employees to recognize phishing scams.
- Use reputable payroll services with strong security protocols.
IRS Updates and 2024 Statistics
- In 2024, over 3 million taxpayers reported identity theft-related tax issues.
- The IRS has enhanced its authentication tools, like Secure Access, to help taxpayers protect their data.
- Taxpayers who filed early had 60% fewer fraud incidents compared to those filing later in the season.
FAQs
1. How can I verify if the IRS is contacting me?
The IRS sends initial contact via mail. Verify authenticity by calling 800-829-1040.
2. Is filing taxes online safe?
Yes, but only when done through encrypted, trusted software on secure networks.
3. Can businesses become victims of tax fraud?
Absolutely. Fraudsters often target payroll systems or use fake employee filings to claim refunds.
4. What is the most effective way to prevent tax fraud?
Early filing and safeguarding personal information are the most effective strategies.
5. Should I use identity theft insurance?
Yes, it provides financial protection and expert assistance in case of fraud.
6. What should I do if my tax return is rejected due to duplicate filing?
Immediately contact the IRS and follow up with a fraud alert on your credit report.
Tax fraud is a persistent threat, but taking proactive steps can significantly reduce your risk. By filing early, securing personal information, and staying vigilant against scams, you can protect your finances and peace of mind. For added security, consider using identity theft protection services that offer monitoring, recovery, and insurance.
Stay informed and take action this tax season—because prevention is the best defense against fraud.
Important articles and links related to Protecting Yourself from Tax Fraud

by Brian Thompson | Jan 16, 2025 | Identity Theft, Students
The rise in cyberattacks targeting educational institutions has exposed vulnerabilities that threaten the privacy and security of students, staff, and families. Notable incidents like the PowerSchool data breach reveal the need for robust protection mechanisms. This guide looks at the risks, impacts, and strategies to safeguard against Identity theft in educational institutions.
Understanding Identity Theft in Education
Identity theft involves the unauthorized acquisition and misuse of personal information, often for financial or criminal activities. Identity theft in educational institutions is particularly concerning due to the large volumes of sensitive data stored, including Social Security numbers, financial records, and academic details.
Educational settings are prime targets for cybercriminals because they rely on digital platforms and legacy systems. By understanding the causes and solutions, students and institutions can mitigate risks effectively.
Key Statistics:
- 74% of education data breaches occur in colleges and universities.
- Students aged 18–24 are five times more likely to experience identity theft compared to older adults.
- The Federal Trade Commission (FTC) highlights that younger victims take longer to detect fraud, leading to more severe consequences.
The PowerSchool Data Breach: What Happened?
Incident Overview
PowerSchool, a leading educational software provider, suffered a significant breach in 2024. Hackers accessed sensitive data from multiple institutions, exposing student’s and staff’s personal information.
Data Compromised
- Names and contact details
- Social Security numbers
- Academic and health records
Impact
The breach disrupted the operations of numerous schools and heightened the risk of identity theft for millions of individuals.
Why Educational Institutions Are Vulnerable
Outdated IT Systems
Legacy software lacks modern encryption, multi-factor authentication, and regular updates, creating entry points for hackers.
Mandatory Data Sharing
Students frequently provide sensitive information like Social Security numbers for admissions, financial aid, and enrollment processes. This centralized data storage becomes a liability if improperly secured.
Increased Online Presence
The widespread adoption of remote learning platforms and public Wi-Fi networks has expanded attack surfaces for cybercriminals.
Cybercriminal Tactics Targeting Students and Institutions
Phishing Scams
Deceptive emails and fake websites trick students and staff into revealing credentials or clicking malicious links.
Public Wi-Fi Exploitation
Unsecured campus networks allow hackers to intercept transmitted data, such as login details and financial transactions.
Social Engineering
Fraudsters manipulate individuals through deceptive interactions, gaining unauthorized access to sensitive information.
Consequences of Identity Theft in Educational Institutions
For Students
- Financial Losses: Fraudulent loans and ruined credit scores.
- Academic Disruptions: Altered academic records or delayed graduation.
- Emotional Impact: Stress and anxiety stemming from identity theft.
For Institutions
- Legal Penalties: Noncompliance with laws like FERPA can result in significant fines.
- Reputational Damage: Loss of trust from students, parents, and stakeholders.
- Operational Costs: Expenses for damage control and system upgrades.
Technological Solutions for Identity Protection
Identity Theft Protection Services
Platforms like Defend-ID offer:
- Real-Time Monitoring: Alerts for suspicious activity.
- Dark Web Scanning: Detects stolen data.
- Recovery Assistance: Dedicated teams help restore identities.
Cybersecurity Tools
- Password Managers: Securely store unique passwords for multiple accounts.
- Two-Factor Authentication (2FA): Adds an extra verification layer.
- Virtual Private Networks (VPNs): Encrypts internet connections to prevent data interception.
Practical Tips for Students
- Use Strong Passwords: Combine upper- and lower-case letters, numbers, and special characters.
- Avoid Public Wi-Fi for Sensitive Transactions: Use VPNs to encrypt your activity.
- Shred Documents: Properly dispose of bank statements and credit card offers.
- Enable Account Alerts: Receive notifications for unusual activity.
- Be Social Media Smart: Avoid oversharing personal details online.
Institutional Strategies for Cybersecurity
- Adopt Advanced IT Solutions: Upgrade to systems with robust encryption and 2FA capabilities.
- Conduct Regular Audits: Identify and rectify system vulnerabilities.
- Educate Students and Staff: Offer workshops and resources on cybersecurity best practices.
Legal and Regulatory Frameworks
FERPA Compliance
The Family Educational Rights and Privacy Act (FERPA) mandates strict data protection measures for educational institutions. Noncompliance can result in lawsuits and federal penalties.
General Data Protection Regulation (GDPR)
Institutions with international students must adhere to GDPR guidelines to protect personal data.
Case Studies: Success Stories
University of California, San Diego
This university implemented continuous system monitoring, collaborated with cybersecurity experts, and conducted regular training programs, significantly reducing breaches.
Student-Led Initiatives
Cybersecurity clubs at several universities have raised awareness, helping peers secure their digital footprints through peer-education workshops.
Government Support for Cybersecurity in Education
Funding and Resources
- Grants for upgrading IT infrastructure.
- Public awareness campaigns about cybersecurity threats.
Initiatives
Programs like the Cybersecurity and Infrastructure Security Agency (CISA) provide educational institutions with actionable resources to strengthen defenses.
Future Trends in Cybersecurity
Emerging threats like AI-driven phishing and ransomware attacks demand proactive security measures. Institutions must invest in predictive analytics and threat intelligence to anticipate and mitigate risks.
FAQs on Identity Theft in Education
1. How can I check if my data was part of the PowerSchool breach?
Visit the school’s website or contact administrators for updates. Consider using a breach-checking tool online.
2. What immediate steps should I take if I’m a victim?
- Notify your bank and credit bureaus.
- File a report with the FTC.
- Freeze your credit to prevent new accounts from being opened.
3. Are schools liable for breaches?
Yes, if negligence can be proven. Schools must comply with data protection laws.
4. How can parents help protect their children?
Educate children on cybersecurity, monitor their accounts, and invest in identity theft protection services.
5. What role does FERPA play in data security?
FERPA protects student records and enforces penalties for noncompliance.
Conclusion
The PowerSchool breach is a stark reminder of the growing cybersecurity challenges in education. Students and institutions must adopt proactive measures to safeguard sensitive data. By leveraging advanced technology, adhering to legal frameworks, and fostering a culture of cybersecurity, we can mitigate the risks of identity theft in education.
Call-to-Action
Protect yourself with Defend-ID. Get real-time alerts, dark web monitoring, and recovery support today!
Articles related to Consequences of Identity Theft in Educational Institutions






