
by Brian Thompson | Jun 26, 2024 | Employee Benefits, Identity Theft
Identity theft is a serious crime that can devastate your finances and your life. When someone steals your personal information, they can use it to open new accounts in your name, run up debts, and damage your credit score. Here we will discuss How to Protect Your Credit from Identity Theft.
A low credit score makes it difficult to get approved for loans, credit cards, and other forms of credit. It can also make borrowing money more expensive since you will likely have to pay higher interest rates. A low credit score also makes it difficult to rent an apartment, get a job, or even get insurance.
How Identity Theft Can Ruin Your Credit Score
Identity thieves can damage your credit in various ways. Here are a few examples:
- Opening New Accounts: Thieves can open new accounts in your name and not make payments, leading to collections and even bankruptcy.
- Maxing Out Credit Cards: They can max out your existing credit cards, significantly damaging your credit score.
- Changing Addresses: They can change the address on your accounts so you don’t receive important billing information, leading to missed payments and further damage to your credit score.
- Filing for Bankruptcy: Thieves can file for bankruptcy in your name, which will stay on your credit report for up to 10 years, making it very difficult to get approved for credit.
The Impact of a Low Credit Score Due to Identity Theft
A low credit score can significantly impact your life. Here are a few examples:
- Loan Approval: You may not be able to get approved for a loan to buy a car or a home.
- Higher Interest Rates: You may have to pay higher interest rates on credit cards and loans.
- Difficulty Renting or Getting a Job: You may have difficulty renting an apartment or getting a job.
- Insurance Issues: You may have difficulty getting insurance.
- Job Promotions and Scholarships: You may be denied a job promotion or a scholarship.
The Emotional Impact of Identity Theft
Identity theft not only ruins your credit but also has a significant emotional impact on victims. Victims may experience feelings of anger, anxiety, stress, and depression. They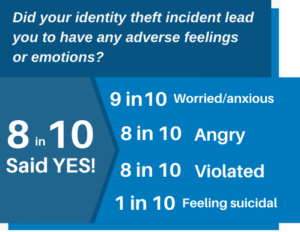 may also feel violated, betrayed, and helpless.
may also feel violated, betrayed, and helpless.
According to a study by the Identity Theft Resource Center, 70% of identity theft victims experience emotional distress. The study also found that victims are more likely to experience anxiety, depression, and post-traumatic stress disorder (PTSD) than people who have not been victims of identity theft.
If you are a victim of identity theft, it is important to seek help from a mental health professional. Talking to someone about what you are going through can help you cope with the emotional impact of the crime.
Steps to Recover from Identity Theft
If you find yourself a victim of identity theft, don’t panic. Here’s a systematic guide to help you regain control and mitigate any potential damage:
- Notify Your Insurance Provider: If you have identity theft insurance, inform them first for guidance and help.
- Alert Your Financial Institutions: Contact your bank and credit card issuers immediately to halt transactions and secure accounts.
- Contact Affected Companies: Reach out to companies where the theft occurred to inform their fraud department.
- Implement a Fraud Alert: Place a fraud alert on your credit with one of the three major credit bureaus.
- Review Your Credit Reports: Access your free credit reports from AnnualCreditReport.com and report any discrepancies.
- File a Report with the FTC: Visit identitytheft.gov to file a comprehensive identity theft report with the Federal Trade Commission (FTC).
- Report to Local Law Enforcement: Filing a police report provides an official record of the identity theft.
- Secure Your Online Presence: Change all online account passwords, consider using a password manager, and activate two-factor authentication.
- Replace Important Documents: Apply for replacements for stolen IDs like your driver’s license, passport, and Social Security card.
- Subscribe to Identity Theft Protection Services: Consider services like defend-id which monitor your financial and digital presence, providing alerts and insurance.
Steps to Take if You Suspect Identity Theft
If you suspect you’ve fallen victim to identity theft, take these essential steps promptly:
- Contact Your Financial Institutions: Reach out to your bank and credit card issuers immediately to freeze your accounts and halt unauthorized transactions.
- Report to Your Identity Theft Insurance Provider: Notify your provider right away for guidance and resources, including legal and financial assistance.
How Identity Theft Protection Services Help
Identity theft protection services, such as defend-id, play a crucial role in safeguarding your online and financial accounts from fraudulent activities. With defend-id’s advanced monitoring technology, subscribers receive alerts about potential fraud approximately four times faster than many competing services.
- Comprehensive Monitoring and Swift Alerts: defend-id provides detailed monitoring by keeping track of your personal and financial account activities. If something unusual is detected, defend-id promptly sends out an alert.
- Robust Insurance Coverage: defend-id offers significant financial protection with an insurance policy that can provide up to $1,000,000 in compensation for eligible losses caused by identity theft.
Protecting Yourself from Identity Theft and Fraud
Protecting yourself from identity theft and fraud is crucial. One effective way to safeguard your personal information is by using comprehensive services like defend-id, which offers robust monitoring and insurance coverage.
- Comprehensive Insurance Coverage: defend-id provides each plan member with a $1,000,000 insurance policy.
- Real-Time Monitoring and Alerts: defend-id monitors your financial and online accounts continuously, alerting you swiftly to any suspicious activity.
- Family Protection: defend-id’s Family Plan extends protection to up to five family members, including both adults and children.
- Trial Period: defend-id offers a 14-day free trial, allowing you to experience their service before committing.
Taking proactive steps by enrolling in a service like defend-id can provide peace of mind and significantly reduce the chances of suffering from identity theft and fraud.
Tactics Used by Identity Thieves
Identity thieves deploy various tactics to access personal data. They might steal your wallet, ID, or mail containing personal information, use a change-of-address scam, send phishing emails, texts, and calls, buy your data off the Dark Web, hack into your email, or intercept your data on an unsecured Wi-Fi network. Understanding these methods allows you to be more vigilant and take preventative measures to secure your personal and financial information.
Take Action Today
Identity theft is a serious crime, but you can protect yourself by taking necessary steps to safeguard your personal information and monitoring your credit reports regularly.
Resources:
- The Federal Trade Commission (FTC): 1-877-438-4338
- The Identity Theft Resource Center: 1-888-400-5530
- The National Association of Consumer Advocates: 1-800-644-7222
Don’t let identity theft ruin your credit and your life. Take action today to protect yourself!
Articles related to How to Protect Your Credit from Identity Theft:

by Brian Thompson | Aug 9, 2023 | Identity Theft
Wifi Safety: Don’t Fall for This Sneaky Trick! Do you use public WiFi? It’s a handy way to stay online while you’re out and about. But be careful! There’s a new trick called WiFi jacking that can steal your info.
Bad guys use a special tool to sneak into public WiFi networks. They can get into your phone and take your personal stuff. This is a big problem, but we can protect ourselves.
WiFi Jacking: A Sneaky Trick Crooks use a strong antenna to do WiFi jacking. They aim it at public WiFi spots and take info from people who are connected. They can grab things like passwords and credit card numbers.
This is really bad because they can use your info to do bad stuff like stealing money or pretending to be you. We need to be careful when we’re on public WiFi.
WiFi Jacking vs. Man-in-the-Middle WiFi jacking sounds like another trick called Man-in-the-Middle. But they’re a bit different.
WiFi jacking steals info from WiFi networks. Man-in-the-Middle attacks mess up conversations between two people online. Both are bad, but WiFi jacking is more about taking info from wireless networks.
Watch Out for Risks WiFi jacking is a problem because it tricks us on public WiFi. We think we’re safe, but the bad guys are listening. We have to be smart and keep our stuff safe.
Here’s what you can do:
- Use Safe WiFi: Pick trusted networks, not ones with strange names.
- Try VPNs: These make a secret path for your info so bad guys can’t take it.
- Use 2FA: Add an extra step when you log in, like a special code sent to your phone.
- Check Websites: Look for “https://” and a lock symbol when you visit a site. That is an indication that it’s safe.
- Update Stuff: Keep your phone and apps up to date. This helps stop bad guys.
Stay Safe and Smart WiFi jacking is a problem, but we can beat it. Connect smartly, use a VPN, try 2FA, and watch out for weird stuff online. Let’s make sure our info stays safe and keep having fun online!
Wifi Safety: Don’t Fall for This Sneaky Trick!
Related Articles:

by Brian Thompson | Feb 3, 2020 | Breach, Identity Theft

John Iannarelli, former FBI Special Agent offers 4 SMB Cybersecurity tips. Is your business safe from the cybersecurity threat?
According to the Allianz Risk Barometer for 2020, cyber incidents ranked as the number one business risk in its ninth annual survey of risk experts.
Based on the above, I just interviewed former FBI Special Agent John Iannarelli (http://fbijohn.com/) in between his national television appearances on Fox News and Fox Business.
Mr. Iannarelli retired from the FBI after more than 20 years of service, during which time he was the FBI’s National Spokesperson, on the FBI Cyber Division executive staff, an FBI SWAT team member, and the Assistant Special Agent in Charge of the FBI’s Phoenix Division, where he oversaw all Criminal, Cyber, and Counter Intelligence investigations throughout Arizona.
Since leaving the FBI, Mr. Iannarelli is an active contributor for national news outlets, keynote speaker, author, and security consultant.
I asked Mr. Iannarelli for simple advice on how to keep small businesses safer in 2020. Here are his 4 cybersecurity tips for small businesses and sole proprietors:
Ransomware
“Maintaining a strong firewall, keeping your security software up to date, and the patching of vulnerable software is critical”, said Iannarelli. He also said, “The restoration of your computer files from a backup is the fastest way to safely regain access to your data.” Mr. Iannarelli recommends “to not pay the ransom as there is no guarantee that you will be able to regain access to your files and that once you pay the cybercriminals they are likely to attack again.”
Hackers steal consumer data from devices connected to unsecured networks by positioning themselves between you and the connection point. This means that instead of talking directly with the hotspot, you end up sending your data to the hacker. Mr. Iannarelli recommends “use of VPN encryption to help prevent cybercriminals from hacking into your Wi–Fi connection and intercepting the data you send and receive.”
Vendor Due Diligence
According to the Ponemon Institute, third-party breaches remain a dominant security challenge for small and large businesses. Over 63% of data breaches are linked to a third party. He said, “Small businesses should establish information security and governance best practices including a data breach and incident response policy and plan.”. A plan will protect your business, help win new business, and elevate your due diligence profile.
State and Federal Notification Laws
Since the United States does not have a Federal Privacy law. Mr. Iannarelli stated“understanding current state privacy laws where your small business conducts business is critical to responding to a data breach event in a timely and effective manner.”
If you have been victimized by an online scam or any other cyber fraud, be sure to report it to the FBI’s Internet Crime Complaint Center at www.IC3.gov or call your local FBI office.
By Mark Pribish
Vice President and ID Theft Practice Leader

by Brian Thompson | Jul 30, 2019 | Breach
In the recently released 2019 Verizon Data Breach Investigations Report (DBIR), Verizon found that 43% of breaches affect small businesses and that a third (32%) of breaches involved phishing, a form of social engineering.
Verizon built this report upon the analysis of 41,686 security incidents and 2,013 confirmed data breaches, the Verizon DBIR digs into the overall threat landscape, the actors, actions, and assets that are present in breaches.
The 2019 Verizon Data Breach Investigations Report (DBIR) Key Takeaways (please see here) highlights 12 key takeaways including:
- Financial gain remains the most common motivate behind data breaches (71%)
- 43% of breaches affect small businesses
 A third (32%) of breaches involved phishing
A third (32%) of breaches involved phishing- The nation-state threat is increasing, with 23% of breaches by nation-state actors
- More than half (56%) of data breaches took months or longer to discover
- Ransomware remains a major threat and is the second most common type of malware reported
- Criminals increasingly target Business Executives with social engineering attacks.
- Crypto-mining malware accounts for less than 5% of data breaches, despite the publicity it didn’t make the top ten malware listed in the report
- Espionage is a key motivation behind a quarter of data breaches
- 60 million records breached due to misconfigured cloud service buckets
- Continued reduction in payment card point of sale breaches
- The hacktivist threat remains low, the increase in the DBIR 2012 report appears to be a one-off spike
An interesting takeaway:
Cyber attackers target the network, where executives are “six times more likely to be a target of social engineering than they were only a year ago; and, C-level executives are 12 times more likely to be the target.”
This means that Business Email Compromises (BEC) are proving successful for ID theft criminals and cyber thieves.
Verizon stated that BEC breaches represented 248 (18%) confirmed breaches out of the 2,013 confirmed data breaches. In addition, Risk-Based Security recently announced the release of its Q1 2019 Data Breach QuickView Report highlighting how over 1,900 data breach events — exposing over 1.9 billion records — were reported in the first three months on 2019.
According to Risk Based Security, “no other first quarter has seen this level of activity, putting 2019 on pace to be yet another ‘worst year on record’ for the number of publicly reported breaches.”
The report found “that 67.6% of records compromised in Q1 were due to exposure of sensitive data on the Internet.”
If you are a small business, considering Identity Theft Protection as an Employee Benefit or a breach readiness and response program is worth considering!

 may also feel violated, betrayed, and helpless.
may also feel violated, betrayed, and helpless.



