Identity fraud is a challenging and sensitive issue. It is typical for you and your family to experience emotional distress as a result of this crime. Give yourself time to work on mending the emotional impact of ID Fraud that you and your family experienced.
Be ready for a range of different feelings.
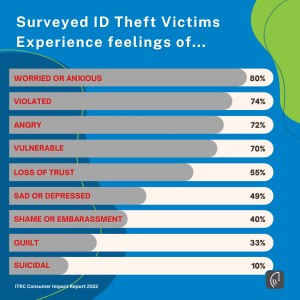
Few individuals are psychologically ready for the effects of identity theft.
Identity theft victims may at times experience overwhelming psychological pain from loss, helplessness, rage, loneliness, betrayal, and even embarrassment. Deep-seated worries about one’s ability to maintain financial security, keep family members safe, and regain trust are brought on by this crime. Another issue you might have to deal with is the possibility that the theft involved a person you know.
Finally, you might become irritated with the people you turn to for assistance. The justice system is still in need of some work, and identity theft is a challenging crime to solve. Be kind to both yourself and those who are trying to assist you.
It will take time to clean up the paper trail, but it’s critical that you get your emotional bearings back as soon as you can. Start by acknowledging and accepting your worries, anxieties, and frustrations.
Some people experience embarrassment as a result of identity theft. No one deserves to be the victim of identity theft, but they feel ashamed and as though they did something wrong, or perhaps deserved it to happen to them. Again, NO ONE deserves to be in this situation.
You don’t need to go through this experience alone.
The emotional harm and isolation you experience might feel worse if your family or friends don’t understand what you’re going through. And in reality, those who haven’t dealt with identity theft are unlikely aware of how long-lasting this crime can be or how stressful it is. Please know that if you are the main provider for the family, you have not failed them. You are a victim who is innocent. A portion of the burden is lifted when you are open and honest with your family. Allow your family and friends to support and encourage you, even if they do not fully understand.
Who did it?
Knowing the imposter may exacerbate your feelings of betrayal, especially if they were a friend or relative. It might be very challenging to report this person to the police. To help you decide or to cope with the consequences, you might want to talk to someone who can help guide you.
Victims frequently describe feeling uneasy when the imposter is unknown, wondering if the person squatting next to them in the grocery store or passing them on the street might actually be the imposter.
Even though you might want the criminal to be punished, it’s possible and even likely that this won’t happen. It is crucial to concentrate on the crime and not the criminal. You must make sure that your identity is cleared as your top priority.
What can you do?
One way to recover or mitigate the emotional impact of identity theft is to become active in a program that monitors your credentials and, more importantly, provides expert recovery solutions. Some victims discover that having a monitoring solution and a resource recovery expert to turn to is extremely beneficial.
Should you consider professional help?
Some victims may lose their capacity to function and manage day-to-day tasks. Some signs of severe depression include exhaustion, overeating, anxiety, drinking, forgetfulness, and a refusal to leave the house or bed. Waiting until you feel lost at the bottom of a pit is not advisable. Even if you don’t feel overwhelmed, speaking with an expert who focuses on helping crime victims can be very beneficial. This might be a supporter of victims, a spiritual figure, a certified therapist, a psychologist, or a psychiatrist.
Identity fraud is a challenging and sensitive issue. As you can see victims may experience overwhelming emotional pain on many levels and even feel embarrassed. It will take time to clean up the paper trail, but it’s important to recognize the emotional impact of ID Fraud. If you are the victim, make your identity the top priority. If you feel overwhelmed, speaking with an expert who focuses on helping crime victims can be helpful. We at defend-id are always here to help.
Related Articles: