
by Brian Thompson | Apr 23, 2025 | Employee Benefits, General, Identity Theft
Small and medium-sized businesses (SMBs) face the same cybersecurity threats as large corporations, without having the same budgets or dedicated security teams. Cybercriminals know this, so they’re increasingly targeting smaller companies with phishing attacks, ransomware, data breaches, and network intrusions. In fact, recent studies show that over 40% of cyberattacks today specifically target small businesses. This is why a VPN for small businesses is critical.
To protect your company from these threats, a Virtual Private Network (VPN) isn’t just beneficial—it’s essential. Remote WorkForce VPN is designed precisely for SMBs, offering business-level security without enterprise-level costs or complexities.
Why VPNs Are Crucial in a Remote and Hybrid World
With more employees working remotely, secure internet access has become vital. Employees regularly access company files, applications, and emails from home offices, airports, coffee shops, or hotels. Unfortunately, these public networks often lack security and are easy targets for cybercriminals.
A VPN solves this problem by creating an encrypted tunnel between an employee’s device and your company resources. As a result, it prevents unauthorized access, protecting credentials, customer information, and intellectual property from theft.
As cyberattacks continue to evolve, a VPN provides your first and most effective defense when employees connect from outside your secure office network.
Why Cybercriminals Target SMBs
You might assume your business is too small to attract cybercriminals. However, attackers think otherwise. Smaller companies often lack proper security measures, have outdated systems, or inconsistent policies. Additionally, many SMBs don’t have a full-time cybersecurity staff or IT team.
Even one compromised device can lead to data theft, costly fines, or significant disruption. Therefore, proactive cybersecurity, starting with a reliable VPN, is essential—not optional.
What Makes Remote WorkForce VPN Different
Many VPN solutions exist, but few cater specifically to SMB needs. Remote WorkForce VPN stands out in several key ways:
-
Easy to Deploy: Our cloud-based VPN can be set up within minutes, whether you have five employees or fifty. There’s no complicated hardware or difficult network configuration needed. Thanks to a simple interface and guided setup, you don’t need to be tech-savvy to secure your business.
-
Fast Performance: Many VPNs slow down internet connections—but not Remote WorkForce VPN. Using advanced traffic optimization and high-speed global servers, our VPN provides seamless, encrypted connections. Consequently, employees can work without delays or interruptions.
-
Strong Encryption: Our VPN uses military-grade encryption (AES-256) and trusted protocols (WireGuard and OpenVPN). This ensures all data remains secure during transmission, whether accessing cloud services or sending confidential documents.
-
Multi-Device Protection: Employees switch between laptops, tablets, and smartphones. Remote WorkForce VPN covers all major platforms—Windows, macOS, iOS, Android—protecting your team no matter their location or device.
-
Affordable Pricing: Most enterprise VPNs are expensive. In contrast, Remote WorkForce VPN offers flexible pricing specifically for small businesses. Thus, you pay only for the features you need, scaling affordably as your company grows.
Compliance and Building Client Trust
If your business manages customer data, financial details, or health records, using a VPN helps you comply with regulations such as HIPAA, GDPR, or PCI-DSS. Secure remote access is often required in compliance audits.
Moreover, clients and partners trust businesses that prioritize data security. Adopting a VPN shows your commitment to protecting sensitive information, helping build lasting credibility and trust.
VPNs and ZTNA: Better Together
Although Zero Trust Network Access (ZTNA) solutions are beneficial, VPNs remain effective, especially as part of a layered cybersecurity strategy.
VPNs are excellent at encrypting traffic and providing secure connections for employees, contractors, or consultants who require extensive resource access. For many SMBs, starting with a VPN and gradually moving toward ZTNA makes practical and financial sense.
Bottom Line: Why You Still Need a VPN for small businesses
In 2025, firewalls and antivirus software alone won’t fully protect your business. SMBs must proactively secure their data, employees, and reputations. Implementing a VPN is among the most effective, immediate, and affordable security upgrades you can make.
Remote WorkForce VPN specifically addresses the unique challenges faced by small businesses. It’s secure, fast, easy to use, and scales as your company grows.
Don’t wait until a cyberattack hits. Let us help you protect your business today.
Related Articles to VPN for small businesses:

by Brian Thompson | Jan 29, 2025 | Breach, General, Identity Theft
The 2024 Data Breach Trends Report from the Identity Theft Resource Center (ITRC) reveals a troubling reality—despite ongoing cybersecurity efforts, data breaches remain at near-record levels, with over 1.7 billion victim notices issued, a staggering 312% increase from the previous year. According to James E. Lee, President of the ITRC, “Stolen and compromised data is so ubiquitous that the number of people and businesses who have not been impacted by a data breach is now dwarfed by the number of victims who have—by a factor of five”. This surge, driven largely by six massive mega-breaches, underscores the urgent need for stronger data security measures, better breach disclosure policies, and widespread adoption of advanced authentication solutions like passkeys.
This report highlights the key trends shaping cybersecurity in 2024, including the industries most affected, the growing impact of AI in cyberattacks, and strategies to enhance data protection for businesses and individuals alike.
Key Findings: The State of Data Breaches in 2024
1. Data Breaches in 2024 Remain at Record Highs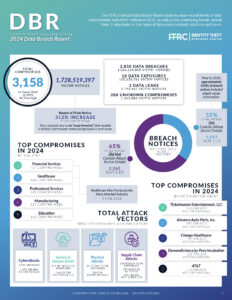
- Total breaches reported: 3,158 (only 44 short of 2023’s record).
- Victim notices issued: Over 1.7 billion notices, representing a 312% year-over-year increase.
- Six major mega-breaches accounted for 85% of all victim notices.
- Despite new privacy laws, data breaches continue to rise.
The rise in victim notices suggests that while breach disclosures may have increased, security improvements remain inadequate.
2. Financial Sector Overtakes Healthcare as the Most Targeted Industry
For the first time since 2018, financial services surpassed healthcare as the most breached industry.
Top Five Breached Industries in 2024
- Financial Services – 737 breaches
- Healthcare – 536 breaches
- Professional Services – 345 breaches
- Manufacturing – 317 breaches
- Education – 162 breaches
While commercial banks and insurance companies saw an increase in attacks, healthcare remained a major target, with breaches exposing sensitive medical and insurance records.
3. Cyberattack Trends and Emerging Threats
Cyberattacks remained the leading cause of data breaches, with stolen credentials, phishing, and AI-driven scams being the most common attack methods.
Most Common Cyberattack Methods in 2024
- Phishing & Smishing Attacks – 455 incidents
- Ransomware – 188 reported cases
- Malware Attacks – 48 breaches
- Credential Stuffing – 29 breaches
Alarmingly, 65% of breach notices failed to disclose the attack method, raising concerns about transparency in cyberattack reporting.
Enhance Protection in 2025
1. Strengthen Authentication and Password Security
One of the most effective ways to prevent data breaches is to eliminate weak passwords and implement stronger authentication methods.
- Adopt Multi-Factor Authentication (MFA) and Passkeys
- Eliminate password reuse across accounts
- Enable biometric authentication for added security
According to the ITRC, many of the biggest breaches of 2024 could have been prevented if organizations had properly implemented MFA and passkeys.
2. Improve Cloud Security Measures
21 major breaches were linked to misconfigured cloud security settings, emphasizing the need for better cloud security controls.
Key Cloud Security Best Practices:
- Implement a Zero Trust security model
- Regularly audit cloud permissions
- Enable automated patching for vulnerabilities
3. AI’s Role in Cybersecurity: A Double-Edged Sword
While AI is helping attackers create more sophisticated cyber threats, it is also being used to enhance cybersecurity defenses.
How AI is Helping Cybersecurity:
- AI-driven monitoring tools detect anomalies faster
- Automated security patches prevent vulnerabilities
- Predictive risk analysis enhances cyber resilience
Organizations should invest in AI-powered cybersecurity solutions to stay ahead of cybercriminals.
Are Data Breach Disclosure Laws Failing?
Despite state and federal breach notification laws, breaches continue to rise, and disclosure remains inadequate.
Key Issues with Current Disclosure Laws:
- 70% of cyberattack-related breach notices lacked details on attack methods
- Publicly traded companies accounted for 76% of all victim notices, despite being only 7% of affected organizations
- Many breaches remain underreported or undisclosed due to regulatory loopholes
However, state privacy laws are beginning to take the lead. Twenty U.S. states have passed comprehensive privacy laws, with eight more taking effect in 2025.
Final Thoughts: The Future of Data Security
The 2024 Data Breach Trends Report highlights ongoing cybersecurity failures but also presents opportunities for stronger data protection.
Key Takeaways for 2024:
- Businesses must implement MFA and passkeys to prevent credential-based attacks.
- Cloud security misconfigurations remain a major vulnerability.
- AI is transforming cybersecurity—for both attackers and defenders.
- Data breach disclosure laws need improvement for greater transparency.
By adopting proactive cybersecurity measures, businesses and individuals can reduce their risk of data breaches and better protect sensitive information.
FAQs on 2024 Data Breach Trends
1. What were the biggest data breaches in 2024?
The largest data breaches included:
- Ticketmaster Entertainment – 560 million victims
- Advance Auto Parts – 380 million victims
- Change Healthcare – 190 million victims
- AT&T – 110 million victims
2. What industries were most affected by cyberattacks in 2024?
The financial services sector had the highest number of breaches, followed by healthcare, professional services, and manufacturing.
3. How can businesses prevent data breaches?
- Use Multi-Factor Authentication (MFA) and passkeys
- Train employees on phishing scams and social engineering
- Monitor and secure cloud environments
4. How is AI impacting cybersecurity?
AI is being used by both attackers and defenders. Cybercriminals leverage AI for phishing and automated attacks, while security teams use AI for threat detection and automated responses.
5. Are state data privacy laws more effective than federal laws?
Yes. Twenty U.S. states have passed strong privacy laws, and more are expected in 2025, filling the gap left by federal inaction.
Articles related to 2024 Data Breach Trends:

by Ryan Smith | Aug 8, 2024 | Employee Benefits, General, Identity Theft
Where do you start with Personal Cyber or Identity Theft Protection? I’ve been getting this question more and more. Agencies I’ve been talking to are noticing the trend:
- Our data is out there due to breach after breach, and it’s only a matter of time before it gets used against us.
- Threat actors are targeting us (especially the elderly and minors) with sneaky social engineering attacks and using AI to get better and faster.
- The fear of ID Theft, Fraud, and the hassle of recovery are on more and more people’s minds.
- With cyber liability becoming more crucial for businesses, offering coverage for individuals makes good sense.
What do people need? And is it a viable option in today’s market? Let’s dig into it in today’s article!
What Do People Need to Protect?
For individuals, cyber threats and fraud risks can be similar to the cyber risks businesses face. It’s easier to start with the “What if I have an incident?” perspective and look at the CIA Triad of Cybersecurity for three easy categories to consider:
- Confidentiality: What data do I need to keep protected, and where is it?
- Integrity: What do I trust, and what if that trusted resource becomes compromised?
- Availability: What technology do I rely on, and what does it mean if it’s not there?
When thinking about home and family, consider these questions:
- Is sensitive data about me out there? What is out there? Is anyone using it?
- Could someone hack my computer or another account? What would they do if they did?
- If I trust a scammer by mistake, can I get any lost money back?
- If someone pretends to be me and accesses my accounts, how do I get my money back and restore my identity? How long will it take, and what do I do in the meantime?
It all comes down to monitoring for suspicious activity and recovering by restoring my identity and getting my money back. The second component is preventing this from happening, which involves awareness, security tools, and being cautious.
The good news is that the same types of coverage that provide monitoring and recovery often offer resources to help individuals reduce their chances of falling victim. Even when we do a good job of protecting ourselves, identity theft can still happen. This is why having protection and recovery services is crucial for everyone.
What Is Often Covered?
When looking into Personal Cyber or Identity Theft Protection, ensure your coverage includes three core capabilities:
- Detect, Monitor, and Alert: Every second counts, so knowing about suspicious activity quickly helps minimize damage. You need a service that can watch for misuse of your information and alert you promptly.
- Recover: Fixing your identity can take time and often pulls people away from work. You may need to change bank accounts, social security numbers, or other items related to your identity and accounts to protect yourself. Repairing your credit or getting money back can be stressful and difficult without experience. A team doing this on your behalf helps you get your life back to normal faster.
- Insure Against Loss: Recovering your identity can be costly. Expenses can mount up, and it can take weeks to get frozen bank accounts active again. Reimbursement insurance can help cover expenses related to restoring your identity.
The level of service behind these capabilities may vary from policy to policy. Many offerings have different levels of coverage offered at various prices to give consumers options. In addition to coverage, consider a few other areas to compare to find the right offering for you:
- Options for consumers (Levels of coverage, Family or Individual options, Group options for Employer Paid or Voluntary, and resources or services available to consumers)
- Price
- Minimum Group Size (when offered to individuals as a group benefit)
- Minimum Book Size
- Commission
- Reseller Costs
- Ease of Enrollment
- Reseller Tools and Resources
- Exclusivity (can you only have one option?)
How Do You Roll It Out?
Depending on the offering you choose, many agencies can find quick wins. I work with defend-id to help agencies become resellers, and here are three strategies I always recommend:
Personal Lines
Start with an announcement and content that will draw in quick wins with your current book of business and give you a good reason to advertise to current prospects. A webinar can bring awareness to the current risks of ID theft and fraud, how attacks happen today, and ways to help people protect themselves with tips, resources, and your new offering. Follow up with articles, newsletters, or tips shared through social media or other channels. For those who don’t engage initially, create a drip marketing or call campaign to share tips and build awareness so they’re primed to consider it upon renewal. Since this type of coverage can be sold to a business as a group benefit, create a referral system to get individuals discounted or paid-for coverage through their workplace.
Groups
If you already sell benefits and don’t offer Personal Cyber or Identity Theft Protection, you may find this easy to add. Many businesses don’t offer it yet, but it can add value for employers since identity theft impacts them too. Employees miss work, are stressed, and it affects others around them. There’s a good incentive for businesses to invest in this for their employees. Ask, “Should we include ID Theft Protection and Recovery?” Employer-paid rates can be as cheap as a cup of coffee per employee per month, so many people are open to it and want it for themselves. If they say no, offer the Voluntary option: “No problem! We have a voluntary option where the employee can get it at a discounted price.”
Cyber Liability
Consider leveling up your cyber liability offer by adding coverage for individuals at the business. If businesses are protecting themselves from cyber risks, one of their biggest challenges is culture. To change the culture, get employees bought in. Investing in them through personal cyber or Identity Theft Protection coverage gets their attention. By adding this, the business can say: “We are building a smarter culture around cybersecurity and want to start by investing in protecting you at home. Our company will provide coverage to help you detect and monitor for suspicious activity and services that will help you recover your identity if needed. This also gives you access to resources to learn how to protect yourself at home. In return, we ask you to take what you learn and apply it here. Help us protect the company and your coworkers from cyber threats by taking part in our training and supporting necessary changes to be safer.”
This approach not only helps change the business’s culture but also adds value to your cyber liability offering without much cost.
Is It Worth It?
I can’t speak to other offerings outside of defend-id, but here are some figures around the value of this kind of offering:
- defend-id’s average group size is 65 employees, with an average rate of $5/employee/month or $325/month.
- Our commission varies between 20% on our Retail (Individual) and Voluntary offerings and 25% on Employer Paid.
- Pricing depends on coverage choices, but every option we have is below $22/month (the average cost is $5/person/month).
- For our offering, there’s no cost to resell or minimum requirements, so there’s no real downside.
The biggest hurdle for many agencies isn’t seeing the financial potential but finding the time to get it going. We work to make it easy for you to implement this as a new offering. Our enrollment process is simple to learn and takes only a moment to set up a group, so the learning curve is minimal.
With strategies like those I laid out above, you should have some ideas about how to get initial sales. We’re always happy to work with agencies to provide templates, content, or other tools to help make launching easy. Just like cyber liability riders vs. a standalone option, having options helps you be more versatile in meeting customers’ needs and nurturing their accounts.
How Do People Get Going?
For defend-id, if you’d like to consider reselling, you can check out our site and sign up as a partner to start reselling right away. Check it out here: defend-id. If you want to explore it further first, I help with onboarding new agencies and would be happy to answer any questions you have. Just message me through my LinkedIn page, below.
Whatever you decide to offer, this is a product many people need today, and I encourage you to look deeper into finding a product that fits you and your agency. Best of luck!
-Ryan
RLSConsulting – strategic partner with defend-id

by Brian Thompson | Jul 2, 2024 | General, Identity Theft
The 4th of July is an amazing day filled with fireworks, barbecues, and celebrations of our nation’s independence. Unfortunately, scammers see see it as an opportunity to exploit unsuspecting patriots. Whether it’s through phishing emails, fake sales, or counterfeit event tickets, these scams can quickly turn a fun holiday into a nightmare. This guide aims to help you recognize and avoid common 4th of July scams so you can enjoy a safe and worry-free celebration.
1. Patriotic Emails and Social Media Posts
Scammers know that patriotic feelings run high around the 4th of July. They send out emails and social media posts designed to tug at your heartstrings, often using themes related to veterans, elections, or national pride. These messages might include links that download malware onto your device or steal your personally identifiable information (PII). Be cautious: if something seems off, don’t click on it. Verify the source before engaging with any patriotic-themed content.
2. Shopping Scams
Retailers love to offer deals during the 4th of July, and bad guys take full advantage of this. They create fake websites that look like real sites, offering unbelievable discounts on popular items. Before making a purchase, ensure the website is legitimate. Use trusted retailers, look for secure payment options, and read reviews. A password manager can help keep your online shopping secure by storing and generating strong passwords.
3. Fake Event Tickets
Summer concerts, parades, and fireworks shows are highlights of the 4th of July. Unfortunately, scammers sell counterfeit tickets for these events, often through social media or classified ads. Always buy tickets from official sources or authorized sellers. Check the event and seller’s legitimacy before purchasing, and avoid deals that seem too good to be true.
Real-Life Example: Last year, “Jane” bought tickets for a local fireworks show through an ad on social media. When she and her family arrived at the park, they were told the tickets were fake. Verify tickets through official channels, or potentially lose some money and have a few crying children on your hands!
4. Fireworks Scams
In states where personal fireworks are allowed, scammers often set up temporary stands selling fake or overpriced fireworks. These vendors might disappear after a day or two, taking your money with them. To avoid these scams, buy fireworks from well-known retailers and use cash to minimize risk. If something feels wrong, walk away and report the vendor.
5. Virus Attacks and Tech Support Scams
Bad guys love holidays because people are often distracted and more careless. They might send fake alerts claiming your computer is infected, hoping you’ll download malicious software or pay for unnecessary tech support. Remember, the Social Security Office does not contact you by phone. Use reliable antivirus software and never provide personal information to unsolicited callers.
Expert Quote: “Cybercriminals capitalize on the chaos of holidays to launch attacks. Always double-check the legitimacy of any unsolicited tech support offers,” advises Ryan Smith, a cybersecurity consultant at RLS Consulting.
6. Fake Online Sales and Deals
Scammers set up fake e-commerce sites offering amazing deals on electronics, fireworks, and other popular items. These sites often look professional but are designed to steal your credit card information. Stick to well-known retailers, check for secure payment methods, and be wary of deals that seem too good to be true.
7. Vacation Rental Scams
Planning a getaway for the holiday? Scammers post fake rental listings with attractive prices to lure you in. Always book through trusted platforms, read reviews, and verify the property’s details with the host. Avoid paying through wire transfers or prepaid debit cards, which are hard to trace and recover.
Local Resource: If you suspect a vacation rental scam, report it to the Federal Trade Commission (FTC) through their website.
8. Phishing Emails and Texts
Phishing scams are common during the 4th of July, with fraudsters sending messages that appear to come from reputable companies. These emails and texts might offer exclusive deals or contest entries. Scrutinize any unexpected messages, verify the sender’s information, and never click on suspicious links. Use security solutions to protect against phishing attacks.
Question: Have you ever received a suspicious email or text around a holiday? How did you handle it?
9. Charity Scams
During patriotic holidays, scammers often pose as charities supporting veterans or other causes. Research any charity before donating. Use websites like Charity Navigator to verify legitimacy, and always donate through the charity’s official website. Avoid giving out personal information or donating via cash or wire transfer.
Real-Life Example: “John” donated $75 to what he thought was a veterans’ charity. It turned out to be a scam, and his personal information was compromised. Now, he always checks Charity Navigator before making any donations.
10. Counterfeit Merchandise
Scammers often sell fake patriotic merchandise, from apparel to fireworks, during the 4th of July. These items can be unsafe and fail to meet safety standards. Buy from reputable retailers, check product reviews, and verify the seller’s authenticity to avoid wasting money on counterfeit goods.
11. Deceptive 4th of July Sales
Scammers exploit the holiday shopping frenzy by creating fake sales on popular items. To protect yourself, shop only from trusted retailers, verify secure payment options, and use prepaid credit cards for online purchases. Always double-check URLs to ensure you’re on the correct website.
12. Giveaways and Sweepstakes Scams
Fake giveaways and sweepstakes are another tactic scammers use to collect your personal information. Be cautious of offers that seem too good to be true. Verify the legitimacy of contests through official channels and never provide sensitive information.
Consider using a security tool like defend-id to monitor your credit for any unusual activity after entering sweepstakes or giveaways.
13. Social Media Scams
Scammers target users on social media with fake ads and posts. Report and block suspicious accounts and avoid clicking on unknown links. Using a VPN can help protect your online privacy and security.
14. Holiday-themed Text Messages
Fake holiday-themed text messages can contain malicious links. Never click on links from unknown senders. Report suspicious messages and block the numbers to prevent future scams.
15. General Cyber Safety Tips
- Keep your antivirus software updated: Regularly update your antivirus program to protect against new threats.
- Use a VPN: A VPN can help keep your online activity private and secure.
- Verify URLs: Always check the URL before entering personal information on a website.
- Update passwords: Regularly update your passwords and use a password manager to keep them secure.
Don’t let 4th of July scams ruin your summer!
By staying vigilant and following these tips, you can protect yourself from 4th of July scams and enjoy a safe holiday. Spread awareness among your friends and family to help them stay safe as well.
Share this article on social media to spread awareness about 4th of July scams. Subscribe to our newsletter for more tips on cybersecurity and scam prevention.
4th of July scams FAQs
- What are common 4th of July scams?
- Common scams include fake sales, counterfeit event tickets, phishing emails, and fake charity solicitations.
- How can I identify a fake online sale?
- Look for red flags like poorly designed websites, unusually low prices, and lack of contact information. Stick to known retailers and use secure payment methods.
- What should I do if I suspect a phishing email?
- Scrutinize the message, verify the sender’s information, and avoid clicking on suspicious links. Use security solutions to protect against phishing attacks.
- How can I verify the legitimacy of a charity?
- Research the charity on websites like Charity Navigator or the Better Business Bureau. Use credit cards or checks for donations and verify the request through the charity’s official website.
- What are the risks of buying fireworks from roadside stands?
- Risks include purchasing fake or overpriced fireworks and sharing payment information with fraudulent sellers. Buy from reputable vendors and use cash to avoid scams.
Detailed Steps for Reporting Scams
- Identify the Scam: Gather all information about the scam, including emails, texts, or receipts.
- Report to Authorities: Contact the FTC through their website or call their hotline. Report identity theft to the Identity Theft Resource Center.
- Notify Financial Institutions: Inform your bank or credit card company to freeze or monitor your accounts.
- Change Passwords: Update your passwords and use a password manager for added security.
- Monitor Credit: Use tools like Credit Karma to keep an eye on your credit report for any unusual activity.
- Spread Awareness: Share your experience with friends and family to help them avoid similar scams.
Articles related to 4th of July scams:

by Brian Thompson | Jun 5, 2024 | General, Identity Theft
Traveling can be exciting, but it also comes with risks, such as identity theft. Vacationers are often more relaxed and less vigilant about their personal information, making them easy targets for thieves. However, with a few simple precautions, you can enjoy your trip without worrying about your personal information falling into the wrong hands. Here are essential tips to protect your identity while traveling and ensure a secure vacation.
1. Secure Your Personal Documents
Before you leave for your vacation, make sure to secure your personal documents. This includes your passport, driver’s license, and any other identification cards you may be carrying. Keep these documents in a secure location, such as a hotel safe or a locked suitcase. Avoid carrying unnecessary documents with you, and if you need to bring them, make sure to keep them hidden and out of sight. By taking these precautions, you can minimize the risk of your personal information being stolen while you’re traveling.
2. Use a VPN When Accessing Public Wi-Fi
When you’re traveling and need to connect to public Wi-Fi, it’s important to use a virtual private network (VPN) to protect your identity. Public Wi-Fi networks are often unsecured, making it easy for hackers to intercept your personal information. A VPN creates a secure connection between your device and the internet, encrypting your data and keeping it safe from prying eyes. By using a VPN, you can browse the internet, check your email, and access your online accounts without worrying about your personal information being stolen.
3. Be Cautious with Your Credit Cards
When traveling, it’s important to be cautious with your credit cards to protect your identity. Avoid using your credit card for purchases at unsecured or unfamiliar locations, as these may be more susceptible to skimming devices or fraudulent activity. Instead, opt for cash or use a secure payment method such as a mobile wallet or chip-enabled card. Additionally, regularly monitor your credit card statements and report any suspicious activity immediately to your credit card company. By taking these precautions, you can enjoy your vacation without the worry of identity theft.
4. Avoid Oversharing on Social Media
While it may be tempting to share every detail of your vacation on social media, it’s important to exercise caution. Oversharing can make you a target for identity theft, as criminals can use the information you post to piece together your personal details. Avoid posting your exact travel dates, location, or any other sensitive information that could be used to compromise your identity. Instead, wait until you return home to share your vacation memories. By being mindful of what you share online, you can help protect your identity while traveling.
5. Set Up a Mail Hold
If you’re going to be away from home for more than a few days, submit a mail hold to the U.S. Postal Service for up to 30 days. You can retrieve your mail once the hold has expired. A mail hold can keep bank statements, credit card bills, and other mail from being used to steal your identity. To hold your mail longer or to reroute your mail, sign up for the Postal Service’s forwarding service.
6. Don’t Bring Unneeded Documents and Cards
Travelers typically need to carry a driver’s license or identification card, travel credit cards, insurance cards, and possibly a passport. But you should leave behind your Social Security card, birth certificate, and other documents that have sensitive personal information. In other words, your wallet, purse, or backpack shouldn’t hold documents and cards that you may want to bring but don’t need to bring.
7. Be Careful at ATMs
For identity thieves, an ATM can be a money-making machine. For instance, they might install a skimming device or shimming device on an ATM to capture card numbers and PINs. To protect your card number and PIN at an ATM when you’re traveling:
- Use a bank-operated ATM rather than a non-bank ATM. Non-bank ATMs, found at places like convenience stores, might not be as safe as those overseen by banks and other financial institutions.
- Change your ATM passcode before and after your trip.
- Use your hand to block the ATM keypad. This can help prevent a person or a hidden camera from seeing your PIN as you’re typing it.
8. Act Quickly if a Card Is Lost or Stolen
If your credit or debit card has been lost or stolen while traveling, report it right away to the card issuer. This may help prevent or minimize financial harm. You can contact the card issuer by looking for the customer service phone number on the card or finding it on the card issuer’s website or app. Federal law safeguards consumers against steep financial losses from a lost or stolen credit or debit card. In the case of a lost or stolen credit card, you might be responsible for as much as $50 in unauthorized charges (though many cards offer zero liability protection). For a lost or stolen debit card, your financial liability depends on how fast you report that the card went missing.
9. Consider an Identity Monitoring Service to protect your identity while traveling
Adding an identity monitoring service to your security toolkit could give you some peace of mind while you’re traveling. An identity monitoring service like the one offered by Defend-ID tracks personal information in credit applications, on websites, in public records, and in other places to spot possible signs of identity theft, and may also offer ID theft insurance.
Frequently Asked Questions
What should I do if my identity is stolen while traveling?
- Contact your providers: Reach out to all of your banks and credit card companies, not just the ones directly involved in the identity theft. You might be advised to close existing accounts and open new ones to help avoid problems.
- Contact the authorities: File identity theft reports with a local law enforcement agency and the FTC.
- Freeze your credit files: …with the three major credit reporting agencies—Experian, TransUnion, and Equifax. A credit freeze severely limits access to your credit information. You can unfreeze your files at any time.
- Review your recent transactions: Go through your bank and credit card accounts online to see whether any suspicious activity shows up. If it does, reach out to your bank or credit card company as soon as possible.
- Monitor your credit report: Obtain your credit report from each of the three credit bureaus to keep an eye out for any suspicious activity. You can also get your reports from all three bureaus weekly at AnnualCreditReport.com.
- Change online passwords: This is especially important for bank accounts and credit card accounts.
Should You Travel With Your Social Security Card?
You should never travel with your Social Security card. Instead, leave it at home in a safe place. In fact, the Social Security Administration advises not carrying your Social Security card with you at all, whether you’re traveling or not. Instead, share your card only when it’s required, which the federal agency says rarely happens.
Does Travel Insurance Cover Credit Card Theft?
Travel insurance might cover credit card theft. However, the coverage likely won’t include reimbursement for financial losses. Rather, a travel insurance company’s representatives can help you cancel credit cards, file a police report, and carry out other tasks associated with credit card theft.
By following these tips, you can significantly reduce the risk of identity theft while traveling and enjoy a secure vacation. Remember, while there is no foolproof way to prevent identity theft, taking these precautions can help you stay safe and protect your personal information.
Article related to protecting your identity while traveling

by Brian Thompson | Mar 27, 2024 | General, Identity Theft
Ah, public WiFi – that sweet, sweet symbol of connectivity when carrier service is poor! Whether we’re sipping a latte in our local cafe or waiting for our flight at the airport, many of us hop onto public WiFi without a second thought. It’s become as routine as brushing our teeth. But here’s the million-dollar question: is public WiFi safe in 2024? (Understanding the Risks and Safeguards)
Today public WiFi networks have shifted from a luxury to a staple of our daily lives. But with great convenience comes great risk, or so the saying should go when it comes to these networks. It’s about time we asked ourselves – are we leaving our digital doors unlocked?
The Evolving Risks of Public WiFi
Let’s face it, the phrase “all public WiFi networks are inherently insecure” has been echoed by cybersecurity experts for years. But what does this mean in today’s context? Essentially, if a WiFi network is public, your online activities could be an open book for those with the know-how to snoop.
The common misconception? “If I’m paying for access, or if it’s a network in a reputable place, it must be safe, right?” Wrong. The reality is, that whether it’s free or paid, the inherent risks remain. Cybersecurity threats have only become more sophisticated in 2024, making public networks even more of a playground for hackers.
Public WiFi Usage: A Love Affair with Risk
It appears our love affair with public WiFi hasn’t gone down over the years. A survey conducted by DecisionData.org highlighted an eye-opening trend: a whopping 82% of individuals will connect to any freely available WiFi when out and about. What’s even more alarming? The majority of these digital adventurers don’t understand the potential dangers. While 71% of users brush off concerns, only a fraction are vigilant about their security.
Protecting Yourself in a WiFi Wild West
So, what’s a savvy internet user to do? First, let’s bust a myth – just because you’re not doing anything ‘sensitive’ doesn’t mean you’re safe. Every connection is an opportunity for data thieves. But don’t fret! Here are some steps you can take to shield yourself:
- Use a VPN: A Virtual Private Network encrypts your internet traffic, making it unreadable to prying eyes.
- Stick to HTTPS: Ensure the websites you visit are secured with HTTPS, which adds an extra layer of security.
- Enable Two-Factor Authentication (2FA): This adds an extra step to your login process, significantly improving your accounts’ security.
- Keep Your Firewall Turned On: This helps block unauthorized access to your devices.
- Stay Updated: Regularly update your devices to patch any security vulnerabilities.
In the grand scheme, public WiFi in 2024 remains a double-edged sword – offering convenience at the cost of potential risks. But with the right precautions, you can enjoy the perks while minimizing the dangers. Stay informed, stay secure, and happy surfing!
Articles related to “Is Public WiFi Safe in 2024? Understanding the Risks and Safeguards”






