
by Brian Thompson | Feb 5, 2025 | Breach, Identity Theft, Scams
Artificial intelligence (AI) is changing how companies and people protect themselves from fraud. AI helps find and stop fraud while also giving criminals new ways to trick people. This article explains both sides of AI in fraud prevention in clear, simple language.
How AI Helps Criminals Commit Fraud
Deepfakes and Fake Identities
AI can create deepfakes, which are very realistic videos, audio clips, and images that look real but are fake. Criminals use deepfakes to create fake identities.
Example: A fake video of a company leader might trick a business into sending money to a criminal.
Here is a fun example (note – this was done 3 years ago, consider how much better and accessible AI is today!): Tobey Maguire instead of Tom Holland in Spider-Man
AI-Driven Scams
Criminals use AI to create smart scams. They design phishing emails and phone calls that sound very real. These scams make it easier to steal money or personal information.
Important Numbers
- The FBI’s Internet Crime Complaint Center (IC3) said AI-assisted phishing scams increased by 35% in 2022. (Source: FBI IC3, 2022 – visit ic3.gov for more information.)
- Cybersecurity Ventures (2023) predicts that losses from AI-enhanced fraud could reach $20 billion by 2025.
How AI Helps Stop Fraud
Smart Computer Programs
Machine learning fraud detection systems use AI to study large amounts of data. They look for patterns that seem odd and can quickly spot fraud. This helps stop fraud before it causes big problems.
Watching for Strange Activity
AI tools can monitor transactions and user actions in real-time. They check every move and alert someone if something seems wrong. This fast response helps prevent more fraud.
Success Stories
- A 2021 report by IBM Security found that companies using AI fraud detection systems reduced fraud losses by 25% in one year. (Source: IBM Security, 2021 – visit ibm.com/security for details.)
- Some big banks have seen a 30% drop in fraud after using AI systems. (Source: McKinsey & Company, 2022 – learn more at mckinsey.com.)
Working With Other Technologies
Using AI with other tools like blockchain and behavior analysis makes fraud prevention even stronger. This mix helps companies protect customers and build trust.
The Ongoing Battle: Fraudsters vs. Fraud Detectors
Fighting Back with AI
As AI improves, criminals also get better at using it. They find new ways to beat security systems. This means the people who build AI tools must keep updating them to stop these tricks.
More Money for AI Research
Companies and governments are spending more money to improve AI for security. Working together, they hope to stay ahead of criminals who use AI for fraud.
Ethics, Laws, and Rules in AI Fraud Prevention
Balancing Safety and Privacy
While AI in fraud prevention has many benefits, it also raises questions about privacy. Companies must use AI carefully so that it does not invade people’s personal lives. Using AI safely and respectfully is very important.
Current Rules and Future Changes
Laws like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States help protect personal data. As AI changes, lawmakers need to update these rules to keep up with new challenges.
The Future of AI in Fraud Prevention
What to Expect Next
The future will bring even more advanced AI tools. Both criminals and defenders will continue to improve their techniques. New tools and better ways to watch for fraud will be needed.
Tips for Companies
- Invest in Advanced AI Tools: Use the latest AI systems to spot fraud quickly.
- Keep Watching All the Time: Real-time monitoring of transactions is very important.
- Train Employees: Teaching staff about new fraud scams can help protect the company.
Tips for Lawmakers
- Create Flexible Rules: Laws should be updated often to keep up with new technology.
- Support Cybersecurity Research: More funding is needed to develop new tools to fight AI-driven fraud.
Frequently Asked Questions (FAQ)
Q: What is AI in fraud prevention?
A: AI in fraud prevention uses artificial intelligence to detect and stop fraud. It can also be misused by criminals to create smarter scams.
Q: How does AI help stop fraud?
A: AI helps by monitoring transactions in real-time, spotting unusual patterns, and alerting companies when something seems wrong.
Q: Can criminals use AI to commit fraud?
A: Yes, criminals can use AI to create deepfakes, fake identities, and smart scams that make it harder to tell real messages from fake ones.
Conclusion
AI in fraud prevention shows both good and bad sides. On one side, AI gives companies strong tools to detect and stop fraud. On the other, criminals use AI to create smarter scams. To keep everyone safe, companies, tech experts, and lawmakers must work together. By using AI responsibly, we can build stronger defenses and a safer future.
References
- FBI Internet Crime Complaint Center (IC3), 2022 – ic3.gov
- Cybersecurity Ventures, 2023 – Annual Cybercrime Report, 2023
- IBM Security, 2021 – ibm.com/security
- McKinsey & Company, 2022 – mckinsey.com
Links to Related Topics:
Share this article on Twitter and Facebook to help others learn how AI in fraud prevention works.

by Brian Thompson | Jan 29, 2025 | Breach, General, Identity Theft
The 2024 Data Breach Trends Report from the Identity Theft Resource Center (ITRC) reveals a troubling reality—despite ongoing cybersecurity efforts, data breaches remain at near-record levels, with over 1.7 billion victim notices issued, a staggering 312% increase from the previous year. According to James E. Lee, President of the ITRC, “Stolen and compromised data is so ubiquitous that the number of people and businesses who have not been impacted by a data breach is now dwarfed by the number of victims who have—by a factor of five”. This surge, driven largely by six massive mega-breaches, underscores the urgent need for stronger data security measures, better breach disclosure policies, and widespread adoption of advanced authentication solutions like passkeys.
This report highlights the key trends shaping cybersecurity in 2024, including the industries most affected, the growing impact of AI in cyberattacks, and strategies to enhance data protection for businesses and individuals alike.
Key Findings: The State of Data Breaches in 2024
1. Data Breaches in 2024 Remain at Record Highs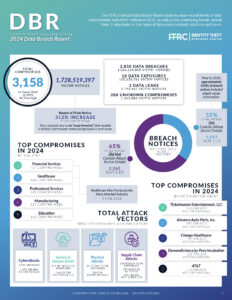
- Total breaches reported: 3,158 (only 44 short of 2023’s record).
- Victim notices issued: Over 1.7 billion notices, representing a 312% year-over-year increase.
- Six major mega-breaches accounted for 85% of all victim notices.
- Despite new privacy laws, data breaches continue to rise.
The rise in victim notices suggests that while breach disclosures may have increased, security improvements remain inadequate.
2. Financial Sector Overtakes Healthcare as the Most Targeted Industry
For the first time since 2018, financial services surpassed healthcare as the most breached industry.
Top Five Breached Industries in 2024
- Financial Services – 737 breaches
- Healthcare – 536 breaches
- Professional Services – 345 breaches
- Manufacturing – 317 breaches
- Education – 162 breaches
While commercial banks and insurance companies saw an increase in attacks, healthcare remained a major target, with breaches exposing sensitive medical and insurance records.
3. Cyberattack Trends and Emerging Threats
Cyberattacks remained the leading cause of data breaches, with stolen credentials, phishing, and AI-driven scams being the most common attack methods.
Most Common Cyberattack Methods in 2024
- Phishing & Smishing Attacks – 455 incidents
- Ransomware – 188 reported cases
- Malware Attacks – 48 breaches
- Credential Stuffing – 29 breaches
Alarmingly, 65% of breach notices failed to disclose the attack method, raising concerns about transparency in cyberattack reporting.
Enhance Protection in 2025
1. Strengthen Authentication and Password Security
One of the most effective ways to prevent data breaches is to eliminate weak passwords and implement stronger authentication methods.
- Adopt Multi-Factor Authentication (MFA) and Passkeys
- Eliminate password reuse across accounts
- Enable biometric authentication for added security
According to the ITRC, many of the biggest breaches of 2024 could have been prevented if organizations had properly implemented MFA and passkeys.
2. Improve Cloud Security Measures
21 major breaches were linked to misconfigured cloud security settings, emphasizing the need for better cloud security controls.
Key Cloud Security Best Practices:
- Implement a Zero Trust security model
- Regularly audit cloud permissions
- Enable automated patching for vulnerabilities
3. AI’s Role in Cybersecurity: A Double-Edged Sword
While AI is helping attackers create more sophisticated cyber threats, it is also being used to enhance cybersecurity defenses.
How AI is Helping Cybersecurity:
- AI-driven monitoring tools detect anomalies faster
- Automated security patches prevent vulnerabilities
- Predictive risk analysis enhances cyber resilience
Organizations should invest in AI-powered cybersecurity solutions to stay ahead of cybercriminals.
Are Data Breach Disclosure Laws Failing?
Despite state and federal breach notification laws, breaches continue to rise, and disclosure remains inadequate.
Key Issues with Current Disclosure Laws:
- 70% of cyberattack-related breach notices lacked details on attack methods
- Publicly traded companies accounted for 76% of all victim notices, despite being only 7% of affected organizations
- Many breaches remain underreported or undisclosed due to regulatory loopholes
However, state privacy laws are beginning to take the lead. Twenty U.S. states have passed comprehensive privacy laws, with eight more taking effect in 2025.
Final Thoughts: The Future of Data Security
The 2024 Data Breach Trends Report highlights ongoing cybersecurity failures but also presents opportunities for stronger data protection.
Key Takeaways for 2024:
- Businesses must implement MFA and passkeys to prevent credential-based attacks.
- Cloud security misconfigurations remain a major vulnerability.
- AI is transforming cybersecurity—for both attackers and defenders.
- Data breach disclosure laws need improvement for greater transparency.
By adopting proactive cybersecurity measures, businesses and individuals can reduce their risk of data breaches and better protect sensitive information.
FAQs on 2024 Data Breach Trends
1. What were the biggest data breaches in 2024?
The largest data breaches included:
- Ticketmaster Entertainment – 560 million victims
- Advance Auto Parts – 380 million victims
- Change Healthcare – 190 million victims
- AT&T – 110 million victims
2. What industries were most affected by cyberattacks in 2024?
The financial services sector had the highest number of breaches, followed by healthcare, professional services, and manufacturing.
3. How can businesses prevent data breaches?
- Use Multi-Factor Authentication (MFA) and passkeys
- Train employees on phishing scams and social engineering
- Monitor and secure cloud environments
4. How is AI impacting cybersecurity?
AI is being used by both attackers and defenders. Cybercriminals leverage AI for phishing and automated attacks, while security teams use AI for threat detection and automated responses.
5. Are state data privacy laws more effective than federal laws?
Yes. Twenty U.S. states have passed strong privacy laws, and more are expected in 2025, filling the gap left by federal inaction.
Articles related to 2024 Data Breach Trends:

by Ryan Smith | Aug 29, 2024 | Breach, Identity Theft
“No big deal!” Maybe this thought ran through your head after reading recent headlines about the National Public Data (NPD) being breached.
When big breaches like this are a regular headline, it’s easy to shrug it off. So I wouldn’t blame anyone for feeling that way.
As for myself, I’m really not worried about it. I say it for a few reasons but one of the biggest is that I have various protections in place that give me that peace of mind.
Today, we’ll talk about what this means and share some tips on how to say, “No big deal!” to big breaches with a bit more confidence than just complacency.
What Happened with NPD?
NPD is a database used for background checks. They have access to data that may include:
- Social Security Numbers (SSNs)
- names
- email addresses
- phone numbers
- and mailing addresses
The details of a breach came out after a proposed class action lawsuit claimed that 2.9 billion personal records may have been exposed (other reports suggest 2.7 billion records, according to CNBC)
The official breach notice said 1.3 million records were possibly exposed.
NPD believes a bad actor hacked them in December 2023 with potential leaks of information in April 2024 and over the summer.
According to the CNBC article, representatives from NPD claim that much of the data was already public or was inaccurate data to begin with.
(All of the above was gathered from CNBC’s article “‘Was my Social Security number stolen?’ Answers to common questions on the National Public Data breach” which is worth a read here: https://www.cnbc.com/2024/08/23/was-my-social-security-number-stolen-national-public-data-breach-questions.html)
What “IF”?
What can happen IF your data gets compromised from this or any one of the other breaches we find in the news each week or month?
The stories vary by victim, but ID Theft and Fraud is a pretty serious problem today.
When major breaches like this put data out there, it can be used by other bad actors to target us or access our accounts, credit, or even medical records. Sometimes it’s used to impersonate you, or it could be used to build a false sense of trust with someone malicious.
Attacks with this kind of data can usually involve theft, extortion, manipulation, or someone impersonating you to attack your friends and family if not also completely random victims.
It really depends on who’s behind the attack and what they have to work with, but the impacts tend to do much more than financial harm. It’s particularly scary when it comes to emotional damage and stress related to recovering.
What’s worse is that the elderly and minors tend to be targets, often sought out because they are easier to trick or because more can be done before a problem is discovered.
Two quick side comments on this:
- If you want to know more about the impacts of ID Theft, follow me because on Thursday, October 31st at 9 MT we’re doing a Halloween and Cybersecurity Awareness Month Special on the “Horrors of ID Theft!” where we’ll dig into some of the crazy cases out there and share more tips on protecting yourself. I’m doing a ton all October but this will be a great one for all to attend!
- And, if you like R-rated action movies, ‘Beekeeper’ with Jason Statham has some ties into the storyline with ID theft. A personal cyber-attack that happens very early on in the movie (before any R-rated stuff if you want to check it out but don’t want to see some hackers get their butts kicked). Some of the threat actor side of it is a bit theatrical but the attack and victim’s perspective is a great example of one way these attacks can play out.
So Why Am I Not Worried?
Of course, things can still happen to me, but I’m focusing on what I can control and there are layers of security I have in place to help me that I’d recommend considering for yourself.
First, we need to acknowledge what we can’t control and let that go so we can focus on what we do control.
I can’t control what companies like NPD do to protect my data. In many cases, people in that database could have no clue NPD even had their data. There are more and more laws around data privacy and disclosures as well as requirements for how to protect this type of data, but it’s going to take time and no one can be 100% secure – so that data is still at risk.
The spokesperson from NPD is probably right, much of this data may already be out there (that doesn’t let them off the hook though!). I can’t tell you how many times I get a letter in the mail that a data breach occurred and I may have had my data exposed.
We’re a bit helpless as consumers and it’s easy to throw our hands up – so that’s why I don’t really worry about these things I have no control over.
That being said, what can we control?
What I can do is monitor for suspicious activity and make it harder for anyone who gets my data to use it. I do this through defend-id and have their ID Theft Protection services. The services alert me when my data is out there, being used, and give me help to recover as quickly as possible to minimize damage.
I also have my and my family’s credit frozen, making it harder to access any of my credit.
To protect my banks, I’m picky with who I bank with but also have made sure to set up MFA and other restrictions on my accounts. Each one has a very random and long password that is unique.
Same with any social accounts or anything else that’s tied to the most sensitive types of data or ways of communicating with me. I keep them locked up as best as possible with MFA and strong passwords.
(While MFA makes it a little harder for me to log in, it makes it MUCH harder for threat actors and, while there are still ways around it, it will slow most of them down)
I’m not impervious to having a breach like this come back to haunt me, but I feel better knowing I’m harder to attack and that someone’s not only got my back but is also watching it.
I still need to be careful with day-to-day activity and watch out for scams or other personal cyber attacks, just like you. That’s where it pays to stay on top of security awareness, and threats and keep an eye out for news articles like the NPD breach. And, it’s one of the reasons it’s important to me to share tips with others and promote awareness.
Want some tips on what to do to protect yourself?
First, be careful with FUD (Fear, Uncertainty, and Doubt) around all of these kinds of breach stories.
Make no mistake, breaches like this get a lot of attention in news articles as well as marketing where your fears are used to get attention for solutions. It’s this kind of behavior around breaches like this that desensitizes us and wears us down.
We have to practice being smart consumers and users of technology by filtering through the noise and looking for what we can control and taking the right action.
Also, keep in mind that scammers use the FUD and confusion to trick more victims. Don’t get caught entering your SSN into someone’s website to search if it’s compromised because you may very well compromise it yourself in the process.
The safest way to find out if your data is out there is to use a legit service that can search for you.
With all that in mind, here are some things I highly recommend doing right now:
Freeze your credit until you need it
- Many of the same monitoring services will help with this but you can still do this yourself if you don’t have resources helping you. Essentially, you need to work with each credit bureau to do so. There’s a good resource here on the USA.gov page that includes other consumer resources: https://www.usa.gov/credit-freeze
- If you need help with this or want our guide on protecting your minors and their identity, let me know by messaging me here or emailing me at info@rlsconsulting.co. I’ll send out our guide directly to you if you want a copy.
Get a password manager
Yes, all of your keys go in one basket, but using randomly generated passwords is much safer. Just protect your Password Manager as much as possible with MFA and a VERY good password or passphrase that you do not share or use elsewhere.
- Most Password Managers will typically tell you if any of your passwords are compromised
- Need help finding one, let me know!
Monitor for activity
Check for data you have that’s out there or if you have any suspicious activity around it:
- It’s worth repeating: be careful giving out your SSN to do searches for it! You very likely would expose it by entering it into various search sites.
- There are many sites and services out there that will let you search for any credentials or sensitive info tied to email addresses. If you don’t have a service you trust, defend-id has a new tool where we can run a search for you. It’ll be available to run by yourself online soon but just let me know if you want me to run a search on your behalf in the meantime.
NOTE: There are easy ways to find if your email is affiliated with any other data out there, but it can still be inconclusive. Just because there are no results, it doesn’t mean it’s not still out there, results that are found could be limited, and again doesn’t mean it’s found ‘everything’.
Get ID Theft Protection or Personal Cyber
The best recommendation for getting back some peace of mind and having help to turn to if your data is used would be to get monitoring and recovery services in place through ID Theft Protection, also often called Personal Cyber:
- Get 20% off of defend-id with code “RLS20” here: https://defend-id-personal.merchantsinfo.com/Default.aspx
- When it’s offered as an employee benefit, it’s super cheap, and the price of a cup of coffee per month per employee is about the same, so if you want to do something cool for your staff this year, let me know!
If your Insurance Agency does not offer ID Theft or Personal Cyber as a solution and you’d like to sell it, I can help you there too. You can learn more in one of my recent articles: Should I Offer Personal Cyber?
Looking for a DYI Identity theft response plan?

by Brian Thompson | Apr 24, 2024 | Breach, Employee Benefits, Identity Theft
The need for robust identity theft protection is critical as businesses face growing cyber threats.. Annually, millions are affected by identity fraud, with businesses bearing a substantial brunt—both in terms of compromised employee data and overall organizational integrity. Beyond a mere perk, identity theft protection is essential for maintaining productivity, safeguarding sensitive information, and attracting and retaining top talent.
Benefits of Identity Theft Protection for Businesses:
- Reduced Employee Disengagement: Studies show resolving identity theft issues can take 100-200 hours, leading to decreased focus and productivity. Identity theft protection services help mitigate these disruptions, allowing employees to concentrate on their work without the added stress of personal security breaches.
- Enhanced Corporate Security: Employee identity theft can lead to broader data breaches affecting company data and client trust. Offering identity theft protection helps reduce the risk of such breaches, strengthening your cybersecurity posture and shielding both employee and corporate data from cyber threats.
- Ongoing Security Education: Identity theft protection programs include education on the latest security practices and vulnerabilities. This proactive approach empowers employees to safeguard their personal and professional data, contributing to overall corporate security.
- Safeguarding Corporate Information: Identity theft protection services monitor and alert employees about suspicious activities linked to corporate assets like credit cards and login credentials. This monitoring helps prevent unauthorized access, protecting sensitive data from cybercriminals.
- Attracting and Retaining Top Talent: Offering identity theft protection as a benefit can significantly enhance your company’s appeal to prospective employees, particularly millennials, who are projected to make up 75% of the workforce by 2025. Modern benefits like these demonstrate a company’s commitment to employee well-being, making them attractive places to work.
Building Trust and Loyalty:
A company’s reputation is bolstered by offering identity theft protection. This benefit showcases that a company cares about its employees’ safety and personal data, which can improve trust and loyalty among current employees and attract new ones.
Beyond Individual Protection:
Identity theft protection services go beyond individual protection, enhancing overall corporate security. They provide tools that monitor and report potential security breaches, not just internally but also on external platforms like social media and the dark web, where stolen data can be found.
Early Detection and Fast Resolution:
Identity theft protection services specialize in the early detection of identity threats, critical for minimizing damage. They monitor various channels to quickly identify and address potential threats before they escalate into serious issues.
Comprehensive Protection Features:
Many identity theft protection plans offer features beyond basic monitoring, including:
- Credit Lock: to restrict access to your credit report and prevent unauthorized accounts from being opened.
- Social Media Monitoring: to track your social media profiles for suspicious activity.
- Password Management Tools: to securely store and manage strong passwords.
These features provide layered security, helping employees protect their digital footprints from potential cyber threats.
Financial Protection and Support:
Financial recovery from identity theft can be daunting. Most identity theft protection services include insurance to cover financial repercussions like legal fees and lost wages, providing essential support during recovery. They also offer mitigation services like dark web monitoring and many others. The most important factor is their ability to help employees recover when fraud does occur!
Investing in identity theft protection is more than a security measure. It is a strategic business decision that enhances your corporate image, increases data privacy, and ensures a resilient organizational culture.
Ready to fortify your business against identity theft? Download your free Defend-ID Identity Theft Response Plan now and take a pivotal step toward comprehensive business security and employee satisfaction!
Articles related to identity theft protection for businesses:

by Brian Thompson | Apr 3, 2024 | Breach, Identity Theft
Cyber threats are as common as coffee breaks, making the myth that cybersecurity falls solely within the world of IT is a terrible oversight. It’s a wide-reaching challenge touching every role from the ground floor to the executive suite. This article aims to dismantle the outdated view of cybersecurity, highlighting the essential role of identity theft protection and individual responsibility in creating a secure digital environment for businesses. Cybersecurity- More Than Just IT’s Job
Everyone Has a Part to Play
Gone are the days when cybersecurity efforts are the sole responsibility of the IT department. In today’s workplace, a single click on a malicious link by any employee can open the floodgates to cyber threats. It’s a reality that highlights the importance of every team member’s role in cybersecurity.
Employees at all levels frequently handle sensitive data, making identity theft protection an essential element of an organization’s overall cybersecurity strategy. Simple habits, such as regularly updating passwords, recognizing phishing attempts, and securely managing personal and professional information, can significantly reduce the risk of identity theft and data breaches.
Training: First Line of Defense
Knowledge is essential when it comes to protecting against cyber threats. Regular, engaging training sessions can transform cybersecurity from an abstract concept to a fundamental practice embraced by all. These sessions should not only cover the basics of cyber hygiene but also the nuances of identity theft and how individuals can safeguard their digital personas.
An environment where cybersecurity is discussed openly and questions are encouraged can demystify the subject, making it more approachable for everyone. Remember, a well-informed employee is an organization’s first line of defense.
Leadership’s Role
The tone for cybersecurity readiness is set at the top. Leadership’s commitment to cybersecurity is critical. Allocating resources for security initiatives, setting clear policies, and fostering a culture where security is everyone’s business, leaders can elevate cybersecurity from a niche IT concern to a universal priority.
Executives and managers should lead by example, demonstrating good cyber practices and actively participating in training sessions. This not only reinforces the importance of cybersecurity but also signals to every employee that their role in protecting the organization is valued and vital.
Cultivating a Culture of Security
Building a culture that prioritizes cybersecurity requires more than just annual training sessions; it demands a shift in mindset. Recognizing and rewarding employees who adhere to security practices can motivate others to follow suit. Similarly, creating channels for reporting suspicious activities without fear of retribution encourages a proactive stance against cyber threats.
Such a culture not only enhances the organization’s resilience against cyber attacks but also fosters an environment where security becomes second nature and part of the daily activities of every employee.
The Collective Shield
The narrative that cybersecurity is an exclusive domain of the IT department must be left in the past. With cyber threats becoming more sophisticated, the responsibility falls on each of us. Every employee, from new hires to the CEO, must understand cyber risks. Embedding strong identity theft protection is crucial for all.
Emphasizing collective responsibility for cybersecurity fosters an environment where everyone is empowered to contribute to the digital safety of the organization. It transforms cybersecurity from a daunting challenge into a shared mission, reinforcing the idea that, together, we are a formidable shield against cyber threats.
Cybersecurity- More Than Just IT’s Job
Dismantling the myth that cybersecurity is just IT’s job is no small feat, but it’s a necessary step toward building more protected organizations. We must embrace our roles and focus on strong identity theft protection. Fostering a culture of security awareness will safeguard our digital realms.
Get your identity theft response plan here:  https://defend-id.ac-page.com/employee-identity-theft-response-plan?test=true
https://defend-id.ac-page.com/employee-identity-theft-response-plan?test=true
Articles related to “Cybersecurity- More Than Just IT’s Job”

by Brian Thompson | Jan 31, 2024 | Breach, Identity Theft
Businesses and organizations take note! The “Mother Of All Breaches,” involving an unprecedented 26 billion records, isn’t just a personal concern; it’s a corporate crisis. This breach, compromising data from major platforms, poses serious risks to both individual users and organizations. Dive into our mother of all breaches business data security tips.
Understanding the Breach: A Business Perspective
This isn’t just about leaked emails and passwords. The “Mother Of All Breaches” is a complex aggregation of multiple incidents, presenting a unique challenge for businesses. The breach’s vast scope means sensitive employee data could be at risk, leading to potential identity theft or financial fraud. Companies need to recognize the gravity of the situation and act swiftly to safeguard their data and support their employees.
Mother Of All Breaches business data security tips – Immediate Actions
For Employers: Ensure your team is aware of the breach. Encourage them to use tools like Have I Been Pwned to check their data status. For accounts with compromised credentials, enforce immediate password changes. Emphasize the necessity of unique passwords and the adoption of two-factor authentication across all work-related platforms.
Password Strength: A strong password is a blend of letters (both uppercase and lowercase), numbers, and symbols. For example, ‘Coffee_Mug123!’ is better than ‘coffee123’. Avoid using easily guessable information like birthdays or common words.
Long-Term Data Security Strategies
A robust approach to password management is non-negotiable. Encourage the use of password managers for generating and storing complex passwords. Regularly monitor company accounts for unusual activities and educate your employees on recognizing phishing attempts and other cyber threats.
Broader Implications for Companies
Responsibility: It’s not just about technical defenses; it’s about a culture of cybersecurity awareness. Regular training sessions and updates on data security policies are essential. Businesses must also stay abreast of global data protection regulations to ensure compliance and safeguard against breaches.
Securing Our Digital Future
The “Mother Of All Breaches” is a wake-up call for businesses and individuals alike. It’s a reminder that in our interconnected digital world, the responsibility for data security is shared. By fostering a culture of cybersecurity mindfulness and implementing proactive strategies, we can safeguard our collective digital future.
FAQs for Businesses:
- What are the first steps a company should take after a breach?Immediately check if company or employee data is involved, enforce password updates, and review security protocols.
- How can businesses educate their employees about cybersecurity? Regular training sessions, updates on cybersecurity best practices, and encouraging a culture of vigilance are key.
- What are the long-term implications of such breaches for businesses? Potential risks include reputational damage, financial losses, and legal implications due to non-compliance with data protection laws.
Articles/linkes related to mother of all breaches business data security tips:







