
by Brian Thompson | Mar 17, 2022 | Uncategorized
Whether working at our local coffee shop or checking sports scores on a plane, most of us use public WiFi all the time. Indeed, because public WiFi networks have become so ubiquitous, we no longer associate them with risky behavior. They’re a normal part of our daily lives. BUT is public wifi safe in 2022?
But failing to understand the risks that are inherent to public WiFi networks, and not taking steps to protect ourselves when we use it is like leaving our front door unlocked when we go to sleep. Sure, if we do it once or twice, we probably won’t get robbed, but why would we take that risk?
The simple truth is that most of us use public WiFi networks all the time. Only a few of us understand the risks, and even fewer are taking steps to adequately protect ourselves.
The Risks of Public WiFi Networks
We’ve said this for years, but it bears repeating: all public WiFi networks are inherently insecure. If a WiFi network is public, that means anything you do online can be tracked and captured. We should never assume that any network is safe, especially it’s safe just because you paid for access to it.
Not everyone understands the difference in risk between secured networks (like you probably have in your home and workplace), and insecure networks like you get at the local Starbucks or at the airport.
Many of us assume that if we have nothing to hide, or are just checking stock prices, we don’t have to be careful.
And wouldn’t the providers of the WiFi network let us know if there were security issues?
People Love to Use Public WiFi
One thing that is very apparent is that we love to connect to public WiFi networks. According to a recent survey by DecisionData.org, nearly 82% of us will connect to any freely available WiFi network when out in public.
But the bigger problem is that most of us who connect to public WiFi networks don’t understand the danger. 71% of those who connect to these networks are not concerned at all, while 16% are a little concerned. Less than 1 in 10 people are very concerned.
Said one respondent: “I had no idea that public WiFi could even be dangerous.” Said another “Who cares. All our data is out there floating around anyways.
How WiFi Hacks Occur

by Brian Thompson | Mar 9, 2022 | Identity Theft
Imagine these scenarios and you will see how WiFi hacks occur in everyday life:
- You are on vacation and you open your laptop in your hotel room. You log into the public WiFi network, quickly agree to the Terms and Conditions (without reading them of course), and start your normal Internet activities. For just a second, you have a fleeting thought: “Is my computer at risk?” And then you begin your normal Internet activities and quickly forget all about it.
- You are waiting to catch your flight in an airport and, after grabbing a cup of coffee and opening your laptop, you see that there’s a “Free Public WiFi” network available. You log in to your banking account to transfer funds. Then you have a vague sense that you might not be doing something safe, but you figure that you’re only going to be online for fifteen minutes, so you’re probably okay, right?
BY JARED HOWE · March 7, 2022

How Safe Are WiFi Hotspots?
Many assume that using a WiFi network at a hotel or airport is the same as logging into our network at home or at the office. But the risks of using WiFi networks at a hotel or airport are exponentially greater than at home or work.
For example, while sharing folders, printers, desktops, and other services can be useful at home or in the office, doing so is inappropriate on a public network. Competitors or hackers can access this information in a public setting.
Most private networks use firewalls to defend users against Internet-based attacks. This is not necessarily true in public wireless networks, where security practices vary widely. You may assume you are safe from outside attacks, but you really have no idea what lies between your laptop and the Internet.
Business travelers willing to connect to any network that offers free Internet access are especially vulnerable to such attacks. It is literally impossible to tell the safe networks from the bad ones. Wireless eavesdropping is possible everywhere. Only a small percentage of public networks prevent wireless eavesdropping, and many networks leave wifi users completely responsible for their laptop security, with extensive or complete file and service exposure.
So What Should I Be Worried About?
Okay, so now you are probably aware that using a public WiFi network while on the road exposes you to a lot of security risks. But what risks are we talking about exactly?
The following is a list of different types of hacks that can occur in public WiFi hotspots:
-
Sniffers:
Software sniffers allow eavesdroppers to passively intercept data sent between your web browser and web servers on the Internet. This is the easiest and most basic kind of attack. Any email, web search or file you transfer between computers or open from network locations on an unsecured network can be captured by hackers. Sniffing software is readily available for free on the web and there are 184 videos on YouTube to show budding hackers how to use them. The only way to protect yourself against WiFi sniffing in most public WiFi hotspots is to use a VPN, such as PRIVATE WiFi™.
-
Sidejacking:
Sidejacking is a method where an attacker uses packet sniffing to steal a session cookie from a website you just visited. These cookies often contain usernames and passwords and are generally sent back to you unencrypted, even if the original log-in was protected via HTTPS. Anyone listening can steal this log-in information and then use it to break into your Facebook or Gmail account. This made news in late 2010 because a programmer released a program called Firesheep that allows intruders sitting near you on a public WiFi network to take over your Facebook session, gain access to all of your sensitive data and send viral messages and wall posts to all of your friends.
-
Evil Twin/Honeypot Attack:
This is a rogue WiFi access point that appears to be a legitimate one, but actually has been set up by a hacker to eavesdrop on wireless communications. An evil twin is the wireless version of the “phishing” scam: an attacker fools wireless users into connecting a laptop or mobile phone to a tainted hotspot by posing as a legitimate provider. When a victim connects, the hacker can launch man-in-the-middle attacks, listening in on all Internet traffic, or just ask for credit card information in the standard pay-for-access deal. Tools for setting this up are easily available (e.g., Karma and Hotspotter). One recent study found that over 56% of laptops were broadcasting the name of their trusted WiFi networks and that 34% of them were willing to connect to highly insecure WiFi networks.
-
ARP Spoofing:
Address Resolution Protocol (ARP) spoofing, is a technique used to attack a wireless network. ARP spoofing allows an attacker to sniff traffic on a LAN and modify or stop the traffic altogether. This attack can only occur on networks that make use of ARP and not another method of address resolution. ARP spoofing sends fake, or “spoofed”, ARP messages to a LAN which associates the attacker’s MAC address with the IP address of the victim. Any traffic meant for the victim’s IP address is mistakenly sent to the attacker instead. The attacker could then forward the traffic to the actual default gateway (passive sniffing) or modify the data before forwarding it (man-in-the-middle attack). The attacker could also launch a denial-of-service attack against a victim by associating a nonexistent MAC address to the IP address of the victim. A successful APR attempt is invisible to the user.
-
“Free Public WiFi” Rogue Networks:
“Free Public WiFi” networks are ad-hoc networks advertising “free” Internet connectivity. Once you connect to a viral network, all of your shared folders are accessible to every other laptop connected to the network. A hacker can then easily access confidential data on your hard drive. These viral networks can be used as bait by an Evil Twin. “Free Public WiFi” networks turn up in many airports. Don’t connect to these networks and you won’t infect your laptop. If you find this kind of network on your laptop, delete it! Then reconfigure your adapter to avoid auto-connecting to any wireless network.
-
Man-in-the-middle Attacks:
Any device that lies between you and a server can execute man-in-the-middle attacks, which intercept and modify data exchanged between two systems. To you, the man-in-the-middle appears to be a legitimate server, and to the server, the man-in-the-middle appears to be a legitimate client. These attacks can be launched by an Evil Twin in a wireless LAN.
You Should Know What You Are Agreeing To
Remember those Terms and Conditions that you agreed to and didn’t read? Well, we’ve actually read them, and here is what some of them say:
- Starbucks: It is the Customer’s responsibility to ensure the security of its network and the machines that connect to and use IP Service(s).
- Boingo Wireless: There are security, privacy and confidentiality risks inherent in wireless communications and technology and Boingo does not make any assurances or warranties relating to such risks. If you have concerns you should not use the Boingo software or service. We cannot guarantee that your use of the wireless services through Boingo, including the content or communications to or from you, will not be viewed by unauthorized third parties.
- JetBlue: Wireless internet connections such as that provided through the Service are not secure. Communications may be intercepted by others and your equipment may be subject to surveillance and/or damage. Since the wireless connection providing you with access uses radio signals, you should have no expectation of privacy whatsoever when using the service. Accordingly, in providing this service, JetBlue cannot and does not promise any privacy protection when you use the service. It is your sole responsibility to install and deploy technological tools to protect your communications and equipment that may be compromised by use of a wireless network.”
For additional examples of Terms and Conditions from hotspot providers, visit the ‘read the fine print’ section of our website.
So How Can I Protect My Laptop?
Okay, so now you know how dangerous wireless networks can be, and the various kinds of attacks you may face when using them. So what specifically can you do to protect yourself and your data?
Below are proactive steps to take and services you can use to protect yourself when using such networks.
- Disable or block file sharing
- Enable a Windows Firewall or install a third-party personal firewall
- Use file encryption
- Most importantly, use a VPN
The one thing that they all have in common is that it is your responsibility to protect yourself. The best way to protect your sensitive information is to use a Virtual Private Network, or VPN. AVPN encrypts the data moving to and from your laptop. The encryption protects all your Internet communication from being intercepted by others in wifi hotspots. In addition, VPNs can prevent hackers from connecting to your laptop and stealing your data files.
Most large companies have a company-support VPN to protect corporate communications. PRIVATE WiFi provides the same capability for individuals, business travelers, and small and medium-sized enterprises. Please visit our website for details.

by Brian Thompson | Feb 28, 2022 | General, Identity Theft
As we continue to see the Russian invasion of Ukraine, it is natural that we look for ways to help. Donating money is often one of the best and easiest ways to make an impact. Unfortunately, we need to ensure that we avoid Ukraine relief scams popping up which is causing more chaos.
Scammers have no shame and will try to lure out money from people like you who are just trying to help. Below are some tips to consider while looking to help.
Donation Tips
-
Give to Organizations You Trust:
Do your research before giving. Review the charity’s purpose and find out how the charity spends its donations. How much is spent directly on the charitable cause? How much goes to overhead and employee compensation? You should also confirm the charity’s name, address, and nonprofit status.
-
Be Wary of Social Network Fundraising:
If you are planning to donate through a social network solicitation, first do some research. Find out what percentage is going to the charity, whether you will be charged a fee, or if a percentage of your donation will be paid to the platform website.
-
Don’t Be Pressured by Telemarketers – Ask Questions Before Donating:
If you receive a call from a telemarketer, ask for the name of the fundraising organization, whether it is registered with the Attorney General’s Office, the name of the charity benefitting from the solicitation, how much of your donation will go to charity and how much to the telemarketer, and the direct telephone number of the charity. Don’t fall for pressure tactics or threats. Remember that you have the right to say no and if you feel pressured or threatened, just hang up.
-
Watch Out for Similar-Sounding Names, Web Addresses, and Other Deceptive Tactics:
Fraudulent organizations may use names that closely resemble those of well-established charitable organizations in order to mislead donors. Look out for fraudulent websites that have a slightly different web address (URL) than that of a legitimate charitable organization. Similar-looking URLs are sometimes purchased by fraudsters to lure in would-be donors. These sites may ask you for personal information or install harmful material onto your device. Be skeptical if someone thanks you for a pledge you never made, and always check your records.
-
Understand the Difference Between “Tax-Exempt” and “Tax-Deductible”:
Being a nonprofit does not mean the organization is exempt from taxation, or that your donation is tax-deductible. Generally, a tax-exempt organization is exempt from paying tax on its income/gifts, but may or may not be able to offer tax deductions to donors. Just because an organization has a “Tax ID Number” doesn’t mean it is a charity, tax-exempt, or tax-deductible. A few tax-exempt organizations – 501(c)(3) tax-exempt status – are able to offer charitable tax deductions for your donations. If you are not sure whether your donation is tax-deductible, verify the charity’s tax-exempt status by using the tools and information located on the IRS website.
-
Protect Your Identity:
Never give your Social Security number or other personal information in response to a charitable solicitation. Never give out credit card information to an organization unfamiliar to you. Some organizations sell or rent their donor lists to other organizations, including organizations that are not charities.
Please consider sharing this with others, you may be helping others avoid Ukraine relief scams!

by Brian Thompson | Feb 9, 2022 | Breach, Identity Theft, Uncategorized
Two years ago I wrote an article asking the question Is Your Digital Identity Safe? Two days ago I read an Infosecurity Magazine article stating Identity Theft Will Get Worse. It appears that Hackers are coming after you in 2022!
Specific to your digital identity and today’s threat landscape for consumers and small businesses, cyber thieves and ID theft criminals have evolved to the point where hacking and data breaches will happen at any time and can affect anyone.
As for the statement “identity theft will get worse,” the fact is that 2021 surpassed the all-time record for data breaches exposing the Personally Identifiable Information (PII) of millions of Americans.
As a reminder, examples of PII include:
- Name: full name, maiden name, mother’s maiden name, or alias
- Personal identification numbers: social security number (SSN), passport number, driver’s license number, taxpayer identification number, patient identification number, employee or student identification number, financial account, or credit card number
- Address information: street address, or email address
- Telephone numbers
- Personal characteristics: photographic images (particularly of face or other identifying characteristics), fingerprints, or handwriting
- Biometric data: retina scans, voice signatures, or facial geometry
- Information identifying personally owned property: VIN number or title number
- Asset information: Internet Protocol (IP) or Media Access Control (MAC) addresses that consistently link to a particular person
And now our digital world, combined with a two-year pandemic, has consumers and small businesses worried. There is so much uncertainty in our world and cybercriminals, and their new scams are adding to the challenge.
Consumer?
If you are a consumer, recent digital risk examples making today’s headline news include How to avoid buying fake Covid tests online and BBB warns consumers of hackers posing as apps like Paypal and Venmo to steal your money.
Cyber thieves and ID theft criminals depend on human nature and emotion such as an individual’s tendency to trust others (e.g. phishing and vishing) and desperation (e.g. the chaos of supply chain shortages such as Covid-19 tests). These phishing and vishing tactics and fake websites have gained attention in recent weeks over the increasing number of identity theft victims.
Small Business Owner?
If you are a small business owner – trusting others and desperation are common risk factors just like a consumer – but it gets worse as Cyber risks top worldwide business concerns in 2022.
According to the just-released 12th Annual Allianz Risk Barometer Survey, cyber incidents at the top of the list. This is only the second time cyber has been at the top of the list in the survey’s history.
Cyber incidents, ransomware attacks, data breaches, or major IT outages worry businesses more than anything else. They worry businesses even more than a business interruption, supply chain disruption, or the COVID-19 pandemic.
To conclude, cyber thieves and ID theft criminals continue to find new and innovative ways to steal your personal information.
Both consumers and small business owners need to keep security education and awareness top of mind. Protecting our digital identities is crucial because hackers are coming for you in 2022.
Mark Pribish

by Brian Thompson | Jan 24, 2022 | Identity Theft
“I didn’t know Agents offer Identity Theft Protection?”.. this is a statement I often hear when we tell people about identity theft protection as an employee benefit.
Most of our partner agents say that many of their clients are unsure of how they are exposed to cybersecurity losses, what cyber services are available as part of an ID theft protection program, or that they underestimate the threat. Also indicating that they just didn’t know Identity Theft Protection was a benefit they could even offer!
If we are serious about protecting our clients and their employees we need to first understand why we as agents need to offer this service in the first place.
The Problem Your Clients Already Face
The reality is that employees are already getting their information stolen and it is impacting employees. We get it though, the costs of benefits seem to constantly increase, and running a business is getting more and more expensive. BUT employers are already paying the price of identity theft due to absenteeism and lost productivity from employees who have had their identity stolen.
*Impacts of ID Theft on Employees:
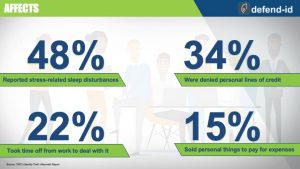

Realities of Identity Theft – Article
The Solution you have for clients
Identity theft protection can be a simple, low-cost, high-value solution. A solution that will protect the company and its employees from the impacts of identity fraud. Businesses Struggle with Rising Costs of Identity Theft – Article
But what does it do for you as an agent?
Yes, all of the things listed above are great reasons alone to offer the program. But, offering identity theft protection solutions as an agent can do many things for you and your business.
Our goal at defend-id is, yes to provide peace of mind with a place to turn for employees, but also to give you a simple solution to an ever-growing problem.
We want to provide you with another line of business to increase retention which increases revenue and recurring revenue for more years to come.
And we want to give you a new reason to reach out, to market your services with new clients or with clients you may have lost in the past – get your foot in the door and add other lines of business.
“I didn’t know Agents offer Identity Theft Protection?”.. this is a statement we do not have to hear. We, who have an opportunity to protect our clients further, can help protect our clients. We can turn this question around, “Did you know we offer identity theft protection as an employee benefit?” Now we are ahead of the curve, offering the best, timely products in the industry. Let us help you get there, it is simple to get appointed and easy to enroll your groups!
Become an appointed defend-id agent today!
*ITRC’s Aftermath Report







