
by Brian Thompson | Sep 20, 2023 | Employee Benefits, Identity Theft, Mortgage
Did you know that something as simple as a change of address can protect or expose you to identity theft? Let’s dive in and discover why change of address monitoring helps in safeguarding your identity!
What is “Change of Address” Monitoring?
Imagine you’re moving to a new house. You’d want all your letters and packages to come to your new address, right? That’s when you inform the post office to redirect all your mail. But what if someone sneaky does this without you knowing? That’s where change of address monitoring steps in. It watches for any changes to your address and alerts you if something looks fishy.
Why is Address Monitoring Important?
- Stay In The Know: With address monitoring, you’ll always know where your mail is heading. No more lost birthday cards or missing bills!
- Spot The Bad Guys: If a sneaky person tries to change your address without you knowing, this tool will quickly let you know.
- Peace of Mind: You can sleep better knowing that you have an extra layer of protection for your personal info.
How Can Criminals Misuse Address Changes?
You might wonder, “Why would anyone want to change my address?” Here’s the scoop:
- Stealing Your Stuff: By rerouting your mail, criminals can snatch credit card offers, checks, or new credit cards before you even know they’re missing.
- Gathering Information: Identity thieves love to collect personal info. With your mail, they can learn a lot about you and potentially misuse it.
- Hiding Their Tracks: If they change your address, you might not get important bills or alerts, giving them more time to cause mischief.
Make Address Monitoring Your Secret Weapon!
You wouldn’t leave your front door unlocked, so why leave your mailbox unprotected? Change of address monitoring is like a security guard for your mail. By being in the know, you can stop identity thieves in their tracks.
*Interesting Fact: According to experts, millions of people have their identities stolen every year, but those with monitoring tools are more likely to catch and stop the bad guys!
Your address is more than just where you live. It’s a gateway to your personal information. By keeping an eye on any changes, you’re not only protecting your mail but also your identity. So, be smart, be safe, and consider adding address monitoring to your safety toolkit!
Remember: Safety first, because your identity is priceless!
Related articles to Change of Address Monitoring: Safeguarding Your Identity:

by Brian Thompson | Sep 6, 2023 | Employee Benefits, Identity Theft, Mortgage
The mortgage lending industry is a crucial pillar of the American dream. It enables people to buy homes, build credit, and secure a future for their families. But there’s a hidden threat jeopardizing this dream for everyone involved: identity theft and fraud. As a responsible mortgage lender, it’s not just good ethics but also good business sense to protect your employees from identity theft. Why? Because doing so further shields your company, your reputation, and most importantly, your borrowers. In this article, we’ll explore the many compelling reasons why mortgage lenders need employee ID Theft Protection to create a Safer, Trustworthy Business Environment.
The Domino Effect: Employees to Borrowers
Mortgage lenders handle a mountain of sensitive information daily. From Social Security numbers to financial statements, your company is a treasure trove for cybercriminals. If an employee’s identity is compromised, the ripple effects can easily extend to your borrowers and tarnish your brand reputation. Identity theft can also lead to cybersecurity issues.
No One Is Immune
We often think it won’t happen to us, but statistics suggest otherwise. According to a report by the Federal Trade Commission, there were 2.4 million identity theft reports in 2022 alone. If an employee falls victim to identity theft, they might inadvertently put borrowers’ data at risk due to distractions or emotional distress.
The Cost of Negligence Is High
Failing to protect your employees and, consequently, borrowers can result in severe financial repercussions. Legal consequences/Legal fees, penalties, and loss of business can add up quickly. Your reputation can take years to rebuild, and some borrowers may never return.
Peace of Mind Equals Productivity
Knowing that they’re protected, employees are more likely to be focused and efficient. They will handle borrowers’ information with the care it deserves, making your borrowers feel secure and satisfied. Happy borrowers lead to positive reviews, and we all know how vital those five-star ratings are in the digital age.
Easy Implementation
There are several top-notch identity theft protection services designed specifically for businesses. These platforms offer a variety of features, such as credit monitoring, alerts, and recovery services, that safeguard your employees’ identities. These services, such as defend-id, are designed to enhance employee safety where they protect sensitive data, and provide financial security.
In a world where data breaches are increasingly common, providing your employees with identity theft protection is not just an added benefit but a necessity. This proactive step will protect your company, preserve your reputation, and most importantly, offer peace of mind to your borrowers. Make the smart move today to shield your tomorrow.
With identity theft protection for employees, everyone wins—you, your staff, and your valued borrowers. Secure your business’s future by making this crucial investment now.
Articles Related to Why Mortgage Lenders Need Employee ID Theft Protection:

by Brian Thompson | Sep 1, 2023 | Employee Benefits, healthcare, Identity Theft
The Hidden Costs of Identity Theft & Employee mental health, an Urgent Call to HR Professionals
Human Resources (HR) professionals have a lot on their plates—everything from recruitment to performance evaluations. Yet, amidst all the paperwork and planning, the emotional well-being of employees often gets overshadowed. While companies are increasingly focusing on mental wellness—as highlighted in a recent [Business West article]—there’s one area that is often overlooked: the impact of identity theft on an employee’s mental health.
The Emotional Anguish of Identity Theft
Feeling Violated
Picture this: One day, you find out someone else is walking around, pretending to be you. They’re spending your money, ruining your credit, and maybe even endangering your reputation. The emotional trauma goes beyond losing a few bucks. It feels like a violation of your very identity.
Loss of Trust
Having your identity stolen can really mess with your ability to trust others. The invisible walls we put up around ourselves can easily make their way into our work environment, affecting how we interact with colleagues and supervisors. It can even result in reduced team collaboration.
Stress and Anxiety
Imagine living with a cloud of constant worry hanging over you—worry about more identity breaches, fear of financial ruin, and the exhausting rigmarole of restoring your identity. This heightened stress and anxiety are not conducive to a productive work environment.
Shame and Embarrassment
Many victims of identity theft end up blaming themselves. This internalized shame can be paralyzing and may cause them to disengage at work, further exacerbating the problem.
The Ripple Effects on the Workplace
Decline in Work Quality
When someone is emotionally and mentally distressed, their work often suffers. The creativity, focus, and determination needed to perform well can be significantly dulled, leading to missed deadlines and subpar work.
Absenteeism
Victims may need time off to resolve the legal and financial mess created by identity theft. These sudden and frequent absences can disrupt the workflow and set back team projects.
Team Dynamics
The mistrust and anxiety felt by one affected individual can have a domino effect, compromising the dynamics of an entire team and reducing overall productivity.
The Role of HR in Mitigating Emotional Strain
Offer Support
HR can play a pivotal role by providing emotional and logistical support. This can range from offering counseling services to granting flexible work hours for affected employees to resolve the issues.
Educate the Team
Proactive education is key. Inform your team about the risks and signs of identity theft and equip them with tools to protect themselves.
Encourage Open Dialogue
Fostering a work environment where employees feel comfortable sharing their concerns can go a long way. Encourage open conversations about mental health and personal challenges to lift the shroud of stigma.
Identity theft is not just a financial issue. It’s an emotional and mental ordeal that can have a significant impact on workplace performance and well-being. By recognizing and addressing the emotional ramifications, HR professionals can ensure a more secure and nurturing work environment. Ultimately, the investment in employee well-being translates into a more engaged, productive, and successful workforce.
Remember, a happy employee is a productive one, and that productivity drives organizational success. Ignoring the emotional toll of issues like identity theft is no longer an option. It’s time for HR to step in and be the change agents organizations so desperately need when it comes to Identity Theft & Employee Mental Health.
Related Articles:

by Brian Thompson | Aug 30, 2023 | Identity Theft
Identity theft is a serious concern in today’s digital age. It occurs when someone steals another person’s personal information to commit fraud or other criminal activities. Shockingly, college students make prime targets for identity theft. Below we dive into this issue, understand why it’s a problem, and learn how both parents and students can take preventative measures.
Why College Students Are Vulnerable:
Inexperience with Finances: Many college students are navigating financial responsibilities for the first time. Their lack of experience can make them susceptible to scams or giving out personal information.
Mounting Debt: With tuition fees, loans, and living expenses, college students often carry significant debt. Identity thieves see them as lucrative targets, aiming to exploit their financial vulnerability.
Shared Living Spaces: Dorms and shared apartments mean personal information is frequently in close quarters. Identity thieves may exploit this situation to access sensitive data.
Public Wi-Fi Usage: College campuses offer convenient but unsecured, public Wi-Fi networks. Hackers can easily intercept information sent over these networks, putting students’ data at risk.
Online Behavior: Young adults might be more likely to trust online sources, making them susceptible to clicking on phishing links or downloading malicious content that can compromise their information.
Protecting College Students from Identity Theft:
Document Security: Teach your child to shred any documents containing personal information before discarding them. This includes bank statements, credit card offers, and medical bills.
Guard Social Security Numbers: Stress the importance of keeping Social Security numbers private. They should only share this information when absolutely necessary.
Strong Passwords: Advise your child to create strong, unique passwords for each online account and avoid reusing passwords. Consider using a password manager for added security.
Social Media Caution: Remind your child to be cautious about sharing personal information on social media platforms. Even seemingly innocent details can be exploited by identity thieves.
Secure Online Shopping: Encourage your child to only make purchases from secure websites. Look for “https://” in the URL and a padlock symbol, indicating a secure connection.
Credit Monitoring: Emphasize the importance of regularly monitoring their credit reports. This helps catch any suspicious activities early and prevents long-term damage.
Safeguarding against identity theft is crucial, especially for college students who are particularly vulnerable. By following these precautions, students can significantly reduce their risk of falling victim to identity theft. Remember to maintain open communication with your child about these threats and how to stay protected. Stay informed, stay cautious, and stay safe in this digital age because College Students Make Prime Targets!
Resources: For more information and resources on identity theft protection, visit:
Additional Tips for College Student Parents:
-
Initiate a conversation with your child about identity theft risks and prevention strategies.
-
Assist your child in establishing a budget and managing their finances responsibly.
-
Educate them on responsible credit card usage and the implications of debt.
-
Show them how to properly shred sensitive documents to protect their personal information.
-
Reinforce the importance of cautious social media sharing to avoid oversharing personal details.
-
Regularly check your child’s credit report together to identify any potential red flags early on.

by Brian Thompson | Aug 9, 2023 | Identity Theft
Wifi Safety: Don’t Fall for This Sneaky Trick! Do you use public WiFi? It’s a handy way to stay online while you’re out and about. But be careful! There’s a new trick called WiFi jacking that can steal your info.
Bad guys use a special tool to sneak into public WiFi networks. They can get into your phone and take your personal stuff. This is a big problem, but we can protect ourselves.
WiFi Jacking: A Sneaky Trick Crooks use a strong antenna to do WiFi jacking. They aim it at public WiFi spots and take info from people who are connected. They can grab things like passwords and credit card numbers.
This is really bad because they can use your info to do bad stuff like stealing money or pretending to be you. We need to be careful when we’re on public WiFi.
WiFi Jacking vs. Man-in-the-Middle WiFi jacking sounds like another trick called Man-in-the-Middle. But they’re a bit different.
WiFi jacking steals info from WiFi networks. Man-in-the-Middle attacks mess up conversations between two people online. Both are bad, but WiFi jacking is more about taking info from wireless networks.
Watch Out for Risks WiFi jacking is a problem because it tricks us on public WiFi. We think we’re safe, but the bad guys are listening. We have to be smart and keep our stuff safe.
Here’s what you can do:
- Use Safe WiFi: Pick trusted networks, not ones with strange names.
- Try VPNs: These make a secret path for your info so bad guys can’t take it.
- Use 2FA: Add an extra step when you log in, like a special code sent to your phone.
- Check Websites: Look for “https://” and a lock symbol when you visit a site. That is an indication that it’s safe.
- Update Stuff: Keep your phone and apps up to date. This helps stop bad guys.
Stay Safe and Smart WiFi jacking is a problem, but we can beat it. Connect smartly, use a VPN, try 2FA, and watch out for weird stuff online. Let’s make sure our info stays safe and keep having fun online!
Wifi Safety: Don’t Fall for This Sneaky Trick!
Related Articles:

by Brian Thompson | Aug 2, 2023 | Employee Benefits, Identity Theft
In the evolving landscape of employee benefits, one crucial aspect often remains overlooked: identity theft protection. Employers are striving to provide comprehensive benefits packages that cater to the diverse needs of their workforce. BUT, Identity theft protection is an offering that has yet to receive the attention it truly deserves. There are 4 reasons agents don’t offer identity theft protection.
Below are the four most common objections we hear, keeping identity theft protection from benefits conversations. We unravel the layers of misconception and reveal reasons why identity theft protection should be in every company’s benefits portfolio. From debunking cost concerns to showcasing the tangible advantages for both employers and employees, we’ll illuminate how identity theft protection not only shields against financial turmoil but also nurtures a culture of trust and security within the workplace.
4 Objections
- Cost: While it’s true that identity theft protection can come with a cost, it’s important to consider the potential long-term savings. (defend-id Plans overview – it might be less expensive than you think) In the unfortunate event of a data breach or identity theft incident affecting employees, the costs can skyrocket due to legal fees, reputational damage, and employee downtime. By investing in identity theft protection as an employee benefit, companies proactively mitigate these potential financial burdens. Plus, the cost of offering this benefit is outweighed by improved employee morale, loyalty, and overall productivity.
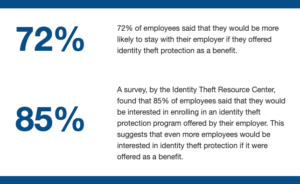 Lack of Demand: It’s understandable to have concerns about demand, but identity theft is a pervasive and growing issue impacting millions of employees yearly. Even if employees haven’t expressed an interest in identity theft protection, it doesn’t mean they wouldn’t value the added security and peace of mind. Offering this benefit demonstrates your commitment to their well-being and financial security. Additionally, proactive education about the risks of identity theft could help employees recognize its importance and drive demand over time. Here are statistics by the Identity Theft Resource Center showing a clear demand for the benefit:
Lack of Demand: It’s understandable to have concerns about demand, but identity theft is a pervasive and growing issue impacting millions of employees yearly. Even if employees haven’t expressed an interest in identity theft protection, it doesn’t mean they wouldn’t value the added security and peace of mind. Offering this benefit demonstrates your commitment to their well-being and financial security. Additionally, proactive education about the risks of identity theft could help employees recognize its importance and drive demand over time. Here are statistics by the Identity Theft Resource Center showing a clear demand for the benefit: - Limited Knowledge: Identity theft protection is increasingly relevant in today’s digital world. Taking the time to familiarize yourself with reputable identity theft protection providers and their features will not only enhance your credibility but also allow you to tailor solutions that best fit your client’s needs. Partnering with knowledgeable providers can also provide the necessary support to address any questions or concerns you may have.
- Concerns about Privacy: Privacy is a valid concern, but reputable identity theft protection providers prioritize data security and confidentiality. When partnering with established providers, you can assure your clients that stringent measures are in place to safeguard sensitive information. Offering identity theft protection can be an opportunity to educate employees about the importance of secure data handling and protection practices. Clear communication about how their data will be used and secured can help alleviate concerns and build trust.
Identity theft protection is a valuable benefit that employers should consider offering to their employees.
It can help to protect employees from the financial and emotional harm of identity theft, and it can also save employers money in the long run.
Cost, lack of demand, limited knowledge, and concerns about privacy are all valid concerns, but they can be overcome. By partnering with a reputable identity theft protection provider, employers can ensure that their employees’ data is secure and that they have access to the resources they need to protect themselves from identity theft.
Offering identity theft protection is a way to show employees that you care about their well-being and financial security. It is also a way to protect your company from the financial and reputational damage caused by an identity theft incident.
If you are an employer, I encourage you to consider offering identity theft protection as a benefit to your employees. It is a wise investment that can protect your employees and your company.
Related Articles






 Lack of Demand
Lack of Demand