
by Brian Thompson | Oct 26, 2022 | General, Identity Theft
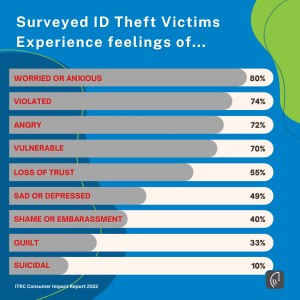
Identity fraud is a challenging and sensitive issue. It is typical for you and your family to experience emotional distress as a result of this crime. Give yourself time to work on mending the emotional impact of ID Fraud that you and your family experienced.
Be ready for a range of different feelings.
Few individuals are psychologically ready for the effects of identity theft.
Identity theft victims may at times experience overwhelming psychological pain from loss, helplessness, rage, loneliness, betrayal, and even embarrassment. Deep-seated worries about one’s ability to maintain financial security, keep family members safe, and regain trust are brought on by this crime. Another issue you might have to deal with is the possibility that the theft involved a person you know.
Finally, you might become irritated with the people you turn to for assistance. The justice system is still in need of some work, and identity theft is a challenging crime to solve. Be kind to both yourself and those who are trying to assist you.
It will take time to clean up the paper trail, but it’s critical that you get your emotional bearings back as soon as you can. Start by acknowledging and accepting your worries, anxieties, and frustrations.
Some people experience embarrassment as a result of identity theft. No one deserves to be the victim of identity theft, but they feel ashamed and as though they did something wrong, or perhaps deserved it to happen to them. Again, NO ONE deserves to be in this situation.
You don’t need to go through this experience alone.
The emotional harm and isolation you experience might feel worse if your family or friends don’t understand what you’re going through. And in reality, those who haven’t dealt with identity theft are unlikely aware of how long-lasting this crime can be or how stressful it is. Please know that if you are the main provider for the family, you have not failed them. You are a victim who is innocent. A portion of the burden is lifted when you are open and honest with your family. Allow your family and friends to support and encourage you, even if they do not fully understand.
Who did it?
Knowing the imposter may exacerbate your feelings of betrayal, especially if they were a friend or relative. It might be very challenging to report this person to the police. To help you decide or to cope with the consequences, you might want to talk to someone who can help guide you.
Victims frequently describe feeling uneasy when the imposter is unknown, wondering if the person squatting next to them in the grocery store or passing them on the street might actually be the imposter.
Even though you might want the criminal to be punished, it’s possible and even likely that this won’t happen. It is crucial to concentrate on the crime and not the criminal. You must make sure that your identity is cleared as your top priority.
What can you do?
One way to recover or mitigate the emotional impact of identity theft is to become active in a program that monitors your credentials and, more importantly, provides expert recovery solutions. Some victims discover that having a monitoring solution and a resource recovery expert to turn to is extremely beneficial.
Should you consider professional help?
Some victims may lose their capacity to function and manage day-to-day tasks. Some signs of severe depression include exhaustion, overeating, anxiety, drinking, forgetfulness, and a refusal to leave the house or bed. Waiting until you feel lost at the bottom of a pit is not advisable. Even if you don’t feel overwhelmed, speaking with an expert who focuses on helping crime victims can be very beneficial. This might be a supporter of victims, a spiritual figure, a certified therapist, a psychologist, or a psychiatrist.
Identity fraud is a challenging and sensitive issue. As you can see victims may experience overwhelming emotional pain on many levels and even feel embarrassed. It will take time to clean up the paper trail, but it’s important to recognize the emotional impact of ID Fraud. If you are the victim, make your identity the top priority. If you feel overwhelmed, speaking with an expert who focuses on helping crime victims can be helpful. We at defend-id are always here to help.
Related Articles:

by Brian Thompson | Oct 20, 2022 | General, Identity Theft
What is identity theft?… How common is it? How do identity thieves operate, and which online scams should you watch out for?
Identity theft continues to be the fastest growing crime in America. It’s consistently one of the top consumer complaints. If you are a college student or in the military, you are one of the most targeted populations by thieves.
It’s been known to cost the victim both time and money, as, on average, 100s of hours, many months, and thousands of dollars are spent to resolve each crime. Identity theft has increased because it’s so easy to do and the rewards are so large
Okay, now that we understand the seriousness of the crime, let’s get down to the business of beating it because it’s not going away, but it can be mitigated. Let’s start with a definition.
Identity theft takes many shapes and forms. We’ll condense it to this: Identity theft is when an unauthorized person uses your personal information to access your financial accounts, open new accounts, or commit a crime.
How can your identity be stolen?
From the theft of your personal information while you’re online, to a grab of data off your unattended paperwork, to the robbery of your credit card information, to breached personal information from companies you work with, identity thieves just need some basic information. The outcome can include fraudulent charges, damaged credit, and a drained checking account.
But you can take steps to avoid being a victim. We’re going to list some of the most common scams and how you can take steps to stop an identity thief.
- You’ll want to watch out for phishing, pharming, vishing, and smishing. These are the strangely named and commonly used tools for identity thieves. Phishing is an attempt to steal your personal information through email by pretending to be a trustworthy source.
- For example, say an identity thief sends you an email pretending to be your bank. Your bank’s logo is on the email, and it looks legitimate. The thief asks you to respond with personal information. The best way to avoid being caught in this scam is to never share personal information via email.
- Pharming is another type of scam where a hacker installs malicious code on a personal computer or server. This code then redirects clicks you make on a website to another fraudulent website without your knowledge. To avoid pharming before you submit any personal information on a website, look for a padlock symbol on the website and https in the website address.
- Vishing attempts to get you to provide personal information over the phone. The thief again pretends to be a legitimate business in need of your personal information to solve a problem for you. You might receive a voice mail asking for your immediate attention. The number provided leads to an automated service asking you to enter personal information. Before you ever give personal information over the phone, make sure you know this is a trusted source.
- Smishing uses cell phone text messages to get you to provide personal information. Often, the text will contain a URL or phone number. And again, just like vishing, the smishing message usually asks for your immediate attention. If something is vitally important, it’s unlikely to be sent via text message. Do not respond to smishing messages.
- Although these types of identity theft are frequently discussed, the most common way your identity can be stolen is through theft. When we say theft, we mean physically stealing something that belongs to you from right under your nose. This includes stealing your mail or searching through your recycling or trash for statements or documents containing personal information. It can also mean stealing your wallet or purse, and, sometimes, you might not even know that your information has been stolen. Take, for example, skimming.
- Skimming occurs when a device records your credit card information and sends it to the thief to make unauthorized purchases. It can happen at an ATM or a retail store, anytime someone gets a moment alone with your credit card.
- Help prevent physical theft by shredding any documents with personal information when they are no longer needed and locking away personal documents. If you’re in a dorm or share housing with other people, consider bringing these personal documents home where they are safer. Also, frequently check your credit and debit card accounts for fraudulent charges. Items with your full social security number, like a social security card, should not be carried in your wallet or purse but instead stored and transported safely.
It may seem like identity theft is everywhere, but if you protect yourself online, on your mobile device, at your mailbox, and always be on-guard for theft, you’ll start fighting the battle against identity theft. And, because identity theft can happen to anyone, everyone should take a few precautions to avoid becoming a victim. Identity Theft Protection is always an option as well. At defend-id we mitigate the risks of identity theft, insure against loss and help you recover fully if it happens to you!
Learn more about identity theft protection:

by Brian Thompson | Oct 11, 2022 | General, Identity Theft
The US Federal Communications Commission (FCC) provides tips on how to stay away from con artists who prey on people after natural disasters like Hurricane Ian. Preying on people after hurricane Ian is something we should all be aware of as with any natural disaster.
Disaster victims and those attempting to donate to charities are both targets of scammers.
“First, understand that officials with government disaster assistance agencies do not call or text asking for financial account information and that there is no fee required to apply for or receive disaster assistance from FEMA or the Small Business Administration,” according to the FCC. “Anyone posing as a federal official and asking for money is an imposter.”
Always be suspicious of phone calls that ask for information!
“Remember that phone scams often use spoofing techniques to deliberately falsify the information transmitted to your caller ID display to disguise their identity or make the call appear to be official,” the alert says. “If someone calls claiming to be a government official, hang up and call the number listed on that government agency’s official website. Never reveal any personal information unless you’ve confirmed you’re dealing with a legitimate official. Workers and agents who knock on doors of residences are required to carry official identification and show it upon request, and they may not ask for or accept money.”
You should also speak with your insurance companies directly rather than relying on opportunistic calls, emails, or texts.
“If you get a phone call about an insurance claim or policy, don’t give out any personal information or agree to any payment until you can independently verify that the call is legitimate,” the alert says. “If the caller says they’re from your insurance company, hang up and contact your agent or the company directly using the number on your account statement… Contractors and home improvement companies may also call claiming to be partners with your insurance provider,” the FCC says. “Never give policy numbers, coverage details, or other personal information out to companies with whom you have not entered into a contract. If your state requires licensing, verify that any contractor you are considering is licensed and carries adequate insurance. Many states have online databases you can check.”
Disasters victims and those attempting to donate to charities are both targets of scammers. Never reveal any personal information unless you’ve confirmed you’re dealing with a legitimate official. Preying on people after hurricane Ian is something we should all be aware of as with any natural disaster.
Related: Avoid Ukraine Relief Scams

by Brian Thompson | Oct 3, 2022 | General, Identity Theft
The Identity Theft Resource Center (ITRC) published the 2022 ITRC Consumer Impact Report last week. It details a new scam known as “social media account takeover fraud,” in which cybercriminals and ID theft criminals hijack Facebook and Instagram accounts to steal personally identifiable information (PII).
Account takeover fraud (ATO), is when a fraudster successfully accesses your bank account, credit card account, cell phone account, utility account, Social Security account, or reward/loyalty card account. This occurs when malicious actors attempt to take control of an account using weak passwords, phishing, hacking, and/or credential stuffing.
What is happening…
Social media account takeover attacks have increased by more than 1,000% in the past 12 months, according to the ITRC. The results of a quick survey of victims who reported a social media account takeover are included in the 2022 Consumer Impact Report. The victims who participated in the micro-survey stated the following:
- 85 percent had their Instagram accounts compromised, while 25 percent had their Facebook accounts compromised.
- At least 48 percent of people clicked on a link they thought came from a friend,
- 22 percent of people fell for a cryptocurrency scam.
- 51 percent of victims who had their accounts compromised lost personal money or sales revenue
- 70 percent have been permanently locked out of their social media accounts
- 71 percent contacted friends listed in the social media account
- 67 percent report the criminal continued to post as the account owner after the lockout.
- 66% of victims claim to have experienced a strong emotional response after losing control of their social media account,
- including feelings of being:
- violated 92%
- suicidal 77%
- 83% worried or anxious
- 78% anger.
Eva Velasquez, President, and CEO of the ITRC, asserts that obtaining social media verification shows how reliable and credible your profile is. Scammers are, however, developing new methods of attack. According to Velasquez, “criminals offer to help people in the verification process.” After taking control of the account, they block the real owner and start posting as that person or company. ”
Velasquez recommends that “consumers follow the instructions for the verification process directly from platforms like Facebook and Twitter to get verified on social media safely.” Do not accept help from someone who says they can ‘assist’ you through the process. ”
When remote working began during the COVID-19 Pandemic, according to James Lee, the ITRC’s Chief Operating Officer, “social media account hijacking significantly increased.” Consumers should “be aware of suspicious messages from friends and not click on links found in emails or texts unless you are 100% sure they are safe,” according to Lee.
The article How Cybercriminals Use Public Online and Offline Data to Target Employees describes another social media account scam technique and shows how a LinkedIn post about a new job opportunity was actually a phishing scam.
We all need to be aware of how social media account holders are being set up for targeted attacks, including customers and business executives. Attackers may target your social media accounts if they have sufficient information about you or your online behavior.
What can you do, then?
With these five prevention suggestions, you can be proactive and avoid social media account takeovers:
- Never use the same password across multiple accounts, especially your social media ones.
- Use a strong passphrase with 20 characters or a password manager.
- Avoid clicking on any links or texts contained in shady (or unexpected) emails or texts.
- Use a VPN and two-factor authentication (2FA), especially when using public WiFi.
- Be wary of phishing scams that pose as well-known companies like LinkedIn, Microsoft, DHL, Amazon, Apple, Google, and Netflix.
Summary: Social Media Account Takeover Fraud
Cybercriminals and ID theft criminals hijack Facebook and Instagram accounts to steal personally identifiable information. Social media account takeover attacks have increased by more than 1,000% in the past 12 months. The quick survey results of victims are included in the Identity Theft Resource Center’s 2022 Consumer Impact Report. Scammers are developing new methods of attack to take control of social media accounts. Consumers can be proactive and avoid social media account takeovers. Use a VPN and two-factor authentication (2FA), especially when using public WiFi, to protect against account hijacking.

by Brian Thompson | Sep 6, 2022 | General, Identity Theft
ISP’s are spying on your family. But what’s an ISP and why should I care? An ISP, or Internet Service Provider, is a company that lets you access the internet from home, usually via a monthly subscription. It’s like a cable company, but instead of connecting you with TV channels, an ISP connects you to the internet. An ISP may sell one or more types of internet service, also called connection types.
Your Internet Service Provider (ISP) is the first connection point between the Internet and your computer. And you should know that ISPs represent one of the many potential threats to online security. After all, you connect to the outside world through their network. Your IP address is the one they assign to you for the duration of your session.
Is my ISP really spying on me?
In a word, yes. Your ISP is likely looking at the websites you visit online. They track you so they can sell your browsing history to other companies. Ever notice how creepy ads follow you around the Internet? This is because you are being tracked.
ISPs can see almost everything you’re doing online. They know the websites you visit, your streaming services, and more. And if you’re not using an encrypted connection, they may even be able to see the usernames and passwords you are using.
What is my ISP doing with my information?
Here in the U.S. ISPs have had the right to sell your private browsing history since 2017, as long as they anonymized your personal data. Major ISPs like AT&T, Comcast, and Verizon said their customers would be able to opt out of data collection, but they make it really hard to do that. Resource: How to Opt Out of your ISP’s Data Collection
Also, ISPs learn a lot by analyzing metadata, which provides them with general information about the kind of user you are. For instance, they could get information on size, timing, and destination of your data packets, which could tell them whether you’re browsing the web, using Skype, downloading files with BitTorrent or streaming movies from Netflix.
This means that ISPs may have more information about you than Google or Facebook, which we all know stores tremendous amounts of data about us.
A good rule of thumb: if you are not taking steps to protect your privacy online, then you should assume that everything you do online, including your emails, are being tracked.
How can I protect myself?
ISPs obviously know a lot about you, but the good news is that you can do a few things to protect your privacy online:
- Only visit secured websites: When you visit a secure website (they start with https://), ISPs can’t see what you’re doing there. The entire communication between you and the secure website you are visiting is encrypted, leaving your ISPs with ciphers it can’t read. The good news is that the most popular services are using HTTPS connections these days.
- Use a VPN like Private WiFi – Using a VPN like Private WiFi on all of your devices is the best way to mask what you do online, including from your ISP. Private WiFi encrypts the connection and routes your connection through the VPN’s server. This encryption prevents your ISP from seeing what you’re doing online.
So what are you waiting for? ISP’s – Spying on your family but defend-id can help secure your connection with Private WiFi. Contact us today to learn more!
Related Articles:
Home WiFi isn’t Safe from Hackers
I use a VPN whenever I work remotely

by Brian Thompson | Aug 25, 2022 | General, Identity Theft
Unfortunately, scammers often see students as easy targets for identity theft. Assuming, as young adults, they are less knowledgeable about identity theft and fraud. Often, students are more likely to fall victim to identity fraud and a lot of that has to do with the environment they are in, the way they communicate, and the information they have to share with the school. With these 7 student identity theft protection tips, students will be better prepared as they embark on their college life.
7 Student Identity Theft Protection Tips
- Don’t overshare.
Social media can make it easy for a scammer to learn personal details about you. Be careful what information you share on these sites because you never know who might see your posts. Your birthday, address, previous schools, and even your pets’ names could be used to gain access to your passwords and accounts if you’ve used them as answers to security or password retrieval questions.
- Speaking of oversharing, be particularly protective of your Social Security number. There are very few instances when it is necessary to provide it (possibly when you’re applying for financial aid or for a job). Make certain that the party requesting your SSN is reputable. Ask them why it’s needed and how they will keep your number secure. Never carry your Social Security card with you; keep it, along with any other documents containing your personal information, in a safe or other secure location.
- This also means keeping your Federal Student Aid (FSA) ID private. For questions about financial aid, contact the Federal Student Aid Information Center at studentaid@ed.gov or 1-800-4-FED-AID — don’t give out personal information over the phone unless you initiated the contact.
- Keep your devices secure.
Would the thief be able to access any private information? Use your security settings to their fullest and be careful what you store on your hard drive. Saved logins and easily accessible personal data make it easy for whoever stole your device to take over your identity.
- Build strong passwords and change them frequently.
It may be tempting to use the same passwords across your accounts so they are easy to remember, but don’t! Make passwords stronger by taking out vowels and adding in special characters. Most sites have their own requirements for what makes a password strong; typically, they should be unique, around 10 characters long, and not easy to guess.
-
Know what to watch for
Think before you click, phishing scams come in all shapes and sizes. For example, fake scholarships and loan listings can be used to target college students. Before sharing any personal information on an application, be sure that the institution is reputable. Look closely for anything suspicious. If a scholarship application asks you to pay an application fee or provide your bank account information, it’s probably NOT legitimate.
- Secure your connection with a VPN, (Virtual Private Network).
Unsecured computer networks make it easy for others to hack your personal information. Since secure network connections are not always available in libraries, student centers, or other public places, use a VPN to encrypt your online activity. Related Article: Public WiFi is Putting You at Risk
- Monitor and track your accounts and transactions.
Review your financial accounts frequently. Monitoring your bank statements, credit card bills, and credit score can help you notice suspicious activity and resolve it quickly. Enable two-factor authentication, which makes it more difficult for scammers to get access. Set up transaction alerts to be notified of suspicious account activity. And always log out of online banking and other secure sites before exiting. If you ever notice questionable account activity, whether login attempts from unknown devices or purchases you didn’t make, report them to the related institution immediately. That institution will provide you with the next steps, such as freezing the account or sending you a new card, to help protect your identity.
- Shred financial documents.
Financial documents often include personal information that you don’t want out in the open. Shred or black out the information printed on credit card offers, as well as on any bank or credit card statements you may receive in the mail, before disposing of them
So stay diligent, think before you click, and use these 7 Student Identity Theft Protection Tips. Identity theft can follow a student well into their professional career and family life. Do what you can now to prevent issues in the future.
Students Targeted for Identity Theft
Online Students are Targeted












